
UKOV Vyacheslav Sergeevich, Candidate of Technical Sciences
The state, features and development prospects of contactless (radio frequency) identification technology are considered
Achievements of information technology in recent years have made it possible to carry out a kind of information revolution.
The widespread introduction of automated control systems has significantly changed our lives.
Until recently, the only brake on this path was the weakest link — a person, to whom nothing human is alien: mistakes, poor health, poor memory, etc.
This did not allow us to fully solve the problem of collecting and inputting/outputting information into a computer control system for any process – be it production, trade, transportation, etc.
This continued until we remembered the technology of radio frequency identification (RFI), the principles of which had been successfully used since World War II for automatic identification of aircraft (“friend or foe”).
This example once again confirms the truth that everything new is a well-forgotten old, but based on new approaches.
Contactless identification technologies most fully meet all the requirements of a computer control system (including control of mobile objects), where recognition and registration of objects and user rights in real time are required.
They are usually built on an optical (well-known barcodes) or radio frequency principle.
Radio frequency recognition is carried out using special tags attached to the object, carrying identification and other information.
This method, which has already become the basis for building modern contactless information systems (CIS), which has the established name of RFID technology (which means radio frequency identification in translation), its capabilities and development prospects will be discussed in this analytical review.
Composition and features of the RFID system
Physical principles of RFID
The general principle of operation of any RFID system is quite simple.
The system always has three main components: a reader, an identifier (card, tag, key fob, tag) and a computer.
The reader emits electromagnetic energy into the surrounding space.
The identifier receives a signal from the reader and generates a response signal, which is received by the reader's antenna, processed by its electronic unit and sent to the computer via the interface (Fig. 1).
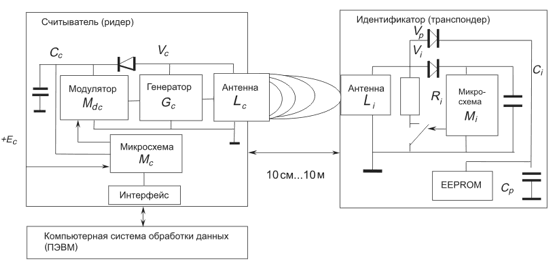
Fig. 1. Operating principle of the RFID system
The reader has: a transceiver and an antenna that send a signal to the tag and receive a response; a microprocessor that checks and decodes the data; memory that stores the data for subsequent transmission, if necessary.
The main components of the transponder (tag): an integrated circuit that controls communication with the reader, and an antenna.
The chip has a memory that stores the identification code or other data.
The tag detects the signal from the reader and begins transmitting the data stored in its memory back to the reader.
There is no need for contact or direct line of sight between the reader and the tag, since the radio signal easily penetrates non-metallic materials. Thus, tags can even be hidden inside the objects to be identified.
Tags can be active or passive.
Active tags operate from an attached or built-in battery, require less reader power, and typically have a longer reading range.
A passive tag operates without a power source, drawing energy from the reader signal.
Passive tags are smaller and lighter than active tags, are less expensive, and have a virtually unlimited service life.
Active and passive tags can be:
— read-only;
— read-write;
— write-once, data into which can be entered by the user.
According to the operating principle, RFID systems can be divided into passive and interactive.
In a simpler passive system, the reader's radiation is constant in time (not modulated) and serves only as a power source for the identifier.
Having received the required energy level, the identifier turns on and modulates the reader's radiation with its code, which is received by the reader.
Most access control systems operate on this principle, where it is only necessary to obtain the serial number of the identifier.
Systems used, for example, in logistics, operate in interactive mode. The reader in such a system emits modulated oscillations, i.e. forms a request.
The identifier decrypts the request and, if necessary, forms an appropriate response.
Anticollision
The need for interactive systems arose due to the need to work with more than one identifier simultaneously.
For example, if it is necessary to read all the labels in a product package in a warehouse.
In such situations, you cannot do without an anti-collision mechanism, which ensures selective sequential work with several identifiers that are simultaneously in the reader's field.
Without such a mechanism, the identifier signals would overlap.
During the anticollision process, the reader identifies all identifiers by their unique serial numbers and then processes them one by one.
Rewritable identifiers
To make a decision on admitting a person to a room or to count the number of boxes on a pallet, it is enough for each identifier to have its own unique number.
However, there is a large class of tasks when it is necessary to place additional information in the tag that reflects the progress of the technological process.
In this case, rewritable identifiers with additional non-volatile memory are used, in which information is retained even after power is lost.
The volume of such memory can vary from several tens of bits to tens of kilobytes, depending on the application.
Frequency ranges and standards
There are two key definitions in RFID technology:
— Proximity (cards and key fobs) short-range identifiers, usually about 10 cm. They are used in access systems, transport applications;
— Vicinity – medium-range identifiers (about one and a half meters); They are used to identify goods and products, mainly in logistics applications. In terms of operating frequencies, the main ones are low-frequency (125 or 134 kHz), mid-frequency (13.56 MHz) and high-frequency (800 MHz … 2.45 GHz). The features of the standards are given in Table. 1.
The low frequency range is typically used in access control systems, as well as for identifying animals and metal objects (such as beer kegs).
The mid-frequency range is currently the most popular.
It is used in transport and other similar applications that require rewritable cards.
The basic standard is ISO 14443, and virtually all smart cards are manufactured in accordance with this standard.
For tags in the mid-frequency range, two standards are relevant: ISO 15693 and EPC. According to ISO 15693, mainly rewritable tags with a fairly wide functionality are produced.
EPC (electronic product code) has a simpler structure and is an electronic analogue of bar codes.
High-frequency The range (800 MHz…2.45 GHz) has only recently begun to be developed, but is of great interest due to the fact that with the existing standards for the radiation power level in this range, passive identifiers achieve ranges of up to 4…8 m, which is very important, for example, for warehouse applications.
Two standards dominate in this range: ISO 18000 and EPC.
Today, it can be said that the EPC standard for the mid-frequency and high-frequency ranges is very promising, especially for logistics applications.
To overcome the technical problems associated with the development of an international standard for RFID, the largest manufacturers of RFID systems have formed a working group within the International Organization for Standardization (ISO) and the International Electrotechnical Committee (IEC) to develop international standards for RFID systems intended for product management. Subcommittee 31, which includes this working group, is working on product labeling with bar codes.
The RFID working group itself is divided into four subgroups: application requirements profiles, data syntax, unique identification of RFID tags, and radio interface.
These subgroups are working on the creation of international standards devoted to, respectively, general issues of RFID system application, information content of the RFID tag and its operation management system, a unified system of unique identification of the RFID tag, and, finally, the rules of radio exchange occurring between the RFID tag and the information reading device.
The result of the work of these subgroups will be a series of international standards that will completely resolve all problems associated with the compatibility of components of RFID systems from different manufacturers.
To facilitate the process of selecting the functionality of an RFID system, standards are being developed for several frequency ranges: below 135 kHz, 13.56 MHz, 433 MHz, 860-960 MHz and 2.45 GHz.
It is assumed that RFID systems operating at these frequencies will satisfy all the needs of users of these systems.
The process of developing an international standard requires its approval by all national standardization bodies participating in its development.
In total, an international standard goes through 6 stages of approval at different levels of the International Organization for Standardization.
By now, the draft standards have overcome the most difficult half of their journey, which can be regarded as a sign that in the near future, interconnected international standards for RFID systems will be created.
The main features of modern RFID standards are given in Table 1.
Table 1. General characteristics of RFID technology
| Standard | Frequency | Applications | Notes |
| ISO 14223 ISO 11784/11785 |
125 (134) kHz | for animal identification (including livestock) |
used widely (e.g. in car immobilizers) |
| ISO 14443 ISO 15693 ISO 10373 |
13.56 MHz | smart cards tags testing methods for cards |
|
| ISO 18000 | 800 … 2.45 GHz | extended range tags |
Currently, the ISO 18000 series of standards is of the greatest interest, the main features of which are presented in Table 2.
Table 2. ISO 18000 series RFID standards
| RFID standard | Title | Main content |
| ISO 18000-1 | Part 1: Definition of parameters to be standardized. | Definition of parameters to be standardized |
| ISO 18000-2 | Part 2: Parameters for air interface communications below 135 kHz | Parameters for contactless interface communications below 135 kHz |
| ISO 18000-3 | Part 3: Parameters for air interface communications at 13.56 MHz | Parameters for contactless interface communications at 13.56 MHz |
| ISO 18000-4 | Part 4: Parameters for air interface communications at 2.45 GHz | Parameters for contactless interface communications at 2.45 GHz |
| ISO 18000-6 | Part 6: Parameters for air interface communications at 860-930 MHz | Parameters for contactless interface communications at 860 – 930 MHz |
| ISO 18000-7 | Part 7: Parameters for Active Air Interface Communications at 433 MHz | Parameters for Active Air Interface Communications at 433 MHz |
Advantages of RFID technology:
— RFID does not require contact or direct line of sight;
— RFID tags are read quickly and accurately (approaching 100% identification);
— RFID can be used even in aggressive environments, and RFID tags can be read through dirt, paint, steam, water, plastic, wood;
— passive RFID tags have a virtually unlimited service life;
— RFID tags carry a large amount of information and can be intelligent;
— RFID tags are almost impossible to counterfeit;
— RFID tags can be not only for reading, but also for recording information.
Application areas of RFID technology
Until recently, RFID systems were more expensive than barcode contactless identification systems.
However, technical progress in the field of tags has led to their use in areas where previously only barcodes were used.
Currently, tag systems successfully compete with barcode systems, including in price.
Moreover, RFID technology allows for solutions for work in optically difficult conditions.
An RFID chip is like a talking barcode, transmitting information to a reader or scanner.
Printed barcodes are typically read by a laser scanner, which requires a clear line of sight to detect and extract the information.
With RFID technology, a scanner can read encoded information even when the tag is hidden, such as embedded in a product or sewn into clothing.
A tiny RFID tag can contain much more information than a barcode.
Moreover, unlike barcodes, RFID tags can transmit data from various packages, such as a shopping cart or product boxes.
The results of the comparative analysis of these two contactless identification methods are presented in Table 3.
Table 3. Comparative characteristics of two contactless identification methods
| Characteristics | RFID | Barcode |
| Identification of an object without direct contact | yes | no |
| Identification of out-of-sight, hidden objects | yes | no |
| Storage of data over 8Kb | yes | no |
| Possibility of repeated recording of data and multiple use of the information storage device | yes | no |
| Identification range over 1m | yes | no |
| Simultaneous identification of several objects | yes | no |
| Resistance to mechanical impact | yes | no |
| Resistance to temperature impact | yes | no |
| Chemical Resistance | yes | no |
| Moisture Resistance | yes | no |
| Safety | yes | no |
| Moving Object Identification | yes | no |
| Durability | yes | no |
| Susceptibility to interference in the form of electromagnetic fields | yes | no |
| Identification of metal objects | yes | no |
| Use of hand-held terminals for identification | yes | no |
| Use of stationary terminals for identification | yes | no |
| Automatic recording of information in Non-Stop mode | yes | no |
| Approximate cost of 1 label, $ | 1 | 0.01 |
| Approximate cost of a stationary card reader, $ | 64 | 40 |
| Information capacity | 8 KB | 100 bytes |
| Sensitivity to contamination | none | high |
| Possibility of tag forgery | impossible | easy |
| Multiple simultaneous reading | possible | impossible |
| Read speed | low | high |
| Maximum reading distance | 0.5 m | 8 m |
Currently, RFID systems are used in a variety of cases where prompt and accurate control, tracking and accounting of numerous movements of various objects is required.
Typical applications:
— electronic control of access and movement of personnel on the territory of enterprises;
— production management, commodity and customs warehouses (especially large ones), stores, issuance and movement of goods and material assets;
— automatic data collection on railways, toll roads, at freight stations and terminals;
— control, planning and management of traffic, schedule intensity and selection of optimal routes;
— public transport: traffic management, fare collection and optimization of passenger flows;
— electronic payment systems for all types of transport, including the organization of toll roads, automatic collection of tolls and transit fees, paid parking;
— ensuring security (in combination with other technical means of audio and video control);
— protection and signaling on vehicles.
The scope of application of the RFID system is determined by its frequency (Fig. 2).
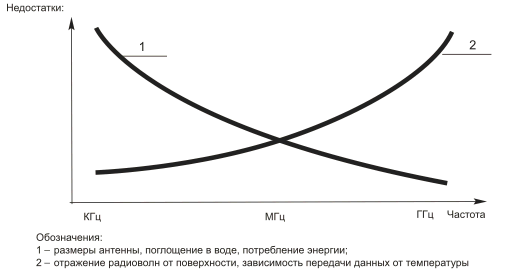
Fig. 2. Dependence of RFID system disadvantages on frequency
Considering the dependencies presented in Fig..2, RFID systems can be divided into three groups.
1. High-frequency (850 – 950 MHz and 2.4 – 5 GHz), which are used where long distances and high reading speeds are required, such as monitoring railway cars, cars, waste collection systems.
For these purposes, readers are installed on gates or barriers, and the transponder is fixed to the windshield or side window of the car. The long range makes it possible to safely install readers out of reach of people.
2. Intermediate frequencies (10 – 15 MHz) are used where large amounts of data must be transmitted.
3. Low-frequency (100 – 500 kHz). Used where a small distance between the object and the reader is acceptable. The usual reading distance is 0.5 m, and for tags built into small “buttons”, the reading range is usually even smaller – about 0.1 m. A large reader antenna can compensate for such a range of a small tag to some extent, but radiation from high-voltage lines, motors, computers, lamps, etc. interferes with its operation. Most access control systems, contactless warehouse and production management cards use low frequency.
Contactless information systems based on RFID technology are currently used when it is necessary:
— a sharp reduction in data entry costs and the elimination of errors associated with manual entry of information;
— high efficiency of registration information;
— a high degree of automation of property management, warehouses, transport, and people's access to premises;
— fully automatic registration with subsequent computer processing of the results (example: a registration system for passengers of a fixed-route taxi or bus with automatic collection of fares);
— improving quality control in manufacturing, warehousing and transportation operations;
— reducing accounting paperwork and labor costs.
All these and many other tasks can be successfully solved with the help of RFID systems.
Let's take a closer look at the main applications of RFID technology.
Transportation applications
In transport applications, the main place (about 80%) is occupied by Mifare cards manufactured by Philips Semiconductors.
In particular, they are used in the Moscow metro, in suburban trains and in a number of other means of transport.
The cards comply with the third level of ISO 14443 A and are supplemented by their own cryptographic protection mechanism, which excludes counterfeiting of transport cards by those who like to ride at someone else's expense.
These same cards are used in petrol station networks, club systems and many other applications where contactless technology is indispensable and protection from unauthorized use is required.
Logistics and warehouse
These applications use identifiers of two mid-range standards (ISO 15693 and EPC), as well as high-frequency identifiers according to the ISO 18000 standard.
The need for the EPC (electronic product code) standard is caused by the following circumstances: firstly, rewritable tags according to ISO 15693 are unprofitable in those applications where it is only necessary to mark the goods, and secondly, their use violates the privacy principle, which has been the cause of several scandalous proceedings.
The EPC standard is similar to a bar code (in terms of data format), and the tag deactivation function allows it to be destroyed when it is no longer needed.
High-frequency tags (800 MHz … 2.45 GHz) provide the maximum range of writing and reading (up to 8 … 10 m), which is indispensable when implementing RFID technology in warehouse inventory management processes.
Electronic documents
This is a completely new, but very promising direction of using RFID technology. Reading speed and reliability, high protection from unauthorized access allowed to start introducing electronic tags into passports, driver's licenses, airline tickets and other documents. In particular, according to available data, in 2006 the EEC countries will switch to passports with RFID tags, entry visas will also receive electronic filling in the near future, and by about 2010 ICAO (International Air Carrier Association) plans to switch to electronic airline tickets.
Currently, many countries are working on projects to transfer domestic passports to an electronic basis. In this case, the memory of the tag implanted in the passport will record not only the usual data of the owner (full name, year of birth, etc.), but also biometric features, as well as a color digital photograph.
Access control and management systems (ACMS)
This is historically the oldest application of RFID technology. Nowadays, access to an office or enterprise using a contactless plastic card (proximity card) has become commonplace. The first solutions based on proximity technology were relatively expensive (compared to the then most popular magnetic cards), but the convenience and reliability provided by RFID allowed for almost all competing technologies to be ousted from the professional access systems market in a few years. The majority of cards and readers for access systems operate in passive mode in the 125 kHz frequency range. There are no established standards, but the most popular and widespread formats are those of EM Marin, HID and Motorola (Indala).
Recently, access control systems have also begun to use ISO14443 (13.56 MHz) smart cards. There are several reasons for this: firstly, the number of such cards in the hands of users worldwide is already in the hundreds of millions, and secondly, the use of such cards provides a number of advantages.
Readers
Readers for access control and management systems are manufactured for EM Marin, HID, Mifare cards. Structurally, readers can be made in a plastic case, in a plastic case with a keyboard, or in a metal case. The user purchases a unified reader and, through simple manipulations, selects the desired data format and indicator control method. All readers have built-in sound and two-color LED indicators, as well as a card reading prohibition input, usually used to create gateway algorithms for passage, etc. In addition, for medium and long ranges, frame-shaped readers (for EM Marin cards) and readers for active identifiers of the 2.45 GHz range are manufactured.
The readers for transport cards are designed for ISO 14443 A and B cards, as well as Mifare cards. For various applications, there are corresponding design solutions: desktop design and frameless readers for installation in customer equipment. For expansion and renewal of facilities equipped with discontinued Philips readers of the MF RD260/560 types, there are corresponding modifications compatible both in terms of overall and connection dimensions and in terms of the exchange protocol.
For applications related to the identification of goods, baggage, correspondence and various products, readers with various parameters are produced, adapted to a specific application.
This category includes:
— desktop readers;
— built-in caseless readers;
— medium and long range readers with remote antennas;
— hand-held readers with a keyboard and LCD.
The readers support two main standards: ISO 15693 and EPC.
Cards
Figure 3 shows a typical design of a proximity—card with contactless RFID identification.
Fig. 3. Typical design of a proximity
card with contactless RFID identification
Tags
ISO 15693 and EPC tags
Tags of this standard are designed to identify non-metallic objects with a maximum reading range of up to 120 cm. The standard tag has the dimensions of a plastic card, but is made on a flexible paper base with an adhesive layer. Supplied in reels of 500 pieces per spool.
Main characteristics:
— Philips I-Code SLI/I-Code EPC/I-Code UID crystal;
— unique serial number;
— EEPROM 128/0/24 bytes.
For special applications, the tags of this standard, made in the form of a plastic disk with a diameter of 20…30 mm, may be of interest. A smaller tag size leads to a decrease in the working range with it by approximately two times. Supplied in packages of 150 pcs. Tags of non-standard sizes can be made to order (for example, 40×40 mm, 60×100 mm and others).
For non-standard sizes, orders from 100,000 pieces are accepted. Standard and custom labels can be printed in either single-color or multi-color according to the customer's sketches. When printing, the minimum order volume is 5,000 labels.
ISO 18000 Labels
Tags of this group are intended mainly for logistics applications, where an identification range of up to several meters is required. In addition, with a special design, tags of this frequency range (900 MHz) work well on metal surfaces, which allows them to be used to identify containers, cars, and railway cars.
Tags for glass and cardboard
They are intended mainly for marking cardboard boxes and similar containers. They can also be used to identify cars by sticking them on the windshield of a car
Tags for metal
Made in a plastic case. The tag can be attached to the surface either with screws through the holes provided for this purpose, or by gluing it to the surface using the adhesive layer on the back of the case. Installation on metal does not impair, and in some cases even improves the performance of the tag.
“Smart” seals
When in working condition, the tag allows for a quick inventory of closed containers. If the seal is broken, the tag stops functioning, although this is not mechanically evident. The use of passive RFID technology provides a solution that is much cheaper than reusable active seals.
The results of the analysis allow us to formulate the following promising areas of application of RFID technology:
1. Access control systems (ACS).
1.1. ACS for any organizations, hotels, warehouses:
— autonomous (for doors, gates, etc.);
— network (locks, latches, turnstiles connected to a computer);
1.2. ACS for residential buildings (entrances, apartments, storage rooms), cottages, summer houses, vegetable stores;
1.3. integration of ACS with security and fire-fighting systems, video surveillance systems, etc.
2. Vehicles.
2.1. vehicle protection:
— electronic tags in the key head (Mitsubishi, Ford);
— plastic driver cards (Black Bug);
— discs on the windshield.
2.2. Determining the location of vehicles.
2.3. Authorized access to certain areas.
2.4. Payment for travel on bridges, highways, tunnels, filling up at gas stations, car washes, parking lots.
2.5. Garage access system.
2.6. Analogue of technical tickets, payment of fines.
2.7. Acceleration of passenger vehicle movement through traffic lights.
2.8. Optimization of the car assembly process (e.g. BMW) on conveyors.
2.9. Accounting and regulation of car refueling with gasoline.
2.10. Parking zones only for taxis at airports, railway and river stations.
2.11. Recording the weight, entry and exit times of vehicles (at the elevator, at coal and other stations).
2.12. Car service — a tag on the windshield with suction cups and a badge for the employee.
2.13. Marking car tires, etc.
3. Technical support for sports and entertainment events:
— determining the time of runners, skiers, etc.;
— accelerating the passage for participants and service personnel at stadiums (for example, the Olympics in Atlanta).
4. Protection of computer systems and telecommunications from unauthorized access:
— in the computer keyboard;
— in the computer case or in the desk.
5. Anti-theft systems for enterprises, apartments, shops.
6. Control and support of objects in technological processes
7. In animal husbandry, poultry farming (implantation of electronic tags under the skin).
8. Determining the location of railway cars, vans.
9. In the subway: passenger cards, accounting of working hours of cashiers, drivers, etc.
10. Medicines — processing orders by container codes.
11. Marking of barrels in the brewing industry and wineries.
12. Exhibition exhibits — «animation» of exhibits when a guide approaches.
13. Electronic signature for persons working at hazardous facilities (for example, in the oil and gas production and coal industries).
14. Stores — issuance and movement of goods and material assets.
15. Emergency notification and rescue services (e.g., the Ministry of Emergency Situations).
The main requirements for contactless identification systems by area of application are given in Table 4.
Table 4. Main requirements for radio frequency identification systems
| Requirements for the identification system |
Application area |
||||||||
| Animals ID | Transport ID | Parking systems | Conveyor flow lines | Staff ID | Air — baggage sorting | Parcel sorting | Payment systems | Prod. lines | |
| Frequency | KHz | KHz | GHz | KHz | KHz | MHz | MHz | MHz | MHz |
| Range | 1 m | 0.1 m | 1 –5 m | 0.1 – 1 m | 1 m | 1 m | 1 m | 1 m | |
| Speed | 3 m/s | & #8212; | 20 m/s | 3 m/s | 3 m/s | 3 m/s | 3 m/s | 3 m/s | 3 m/s |
| reading | |||||||||
| Data volume | 64 bit | 64 bit | 64 bit | 64 bit | 256 bit | 256 bit | 256 bit | 256 bit | |
| 384 bit | 384 bit | 384 bit | 384 bit | ||||||
| Read/write | R/O | R/O, R/W | R/W | R/O | R/O | R/W | R/W | R/W | R/W |
| Temperature | Х | Х | Х | Х | |||||
| Moisture- | Х | Х | Х | (Х) | (X) | X | |||
| stability | |||||||||
| Protection from | X | Х | Х | ||||||
| mechanical | |||||||||
| impacts | |||||||||
| Repeat | X | X | (X) | ||||||
| use | |||||||||
Main directions of RFID technology development
As mentioned above, RFID tags are passive devices consisting of an antenna, a capacitor, and a small semiconductor chip.
New manufacturing technologies now allow these components to be combined on an acrylic substrate, reducing the cost of RFID devices and allowing manufacturers to attach tags to products in the same way as traditional labels.
RFID tags do not require batteries and therefore do not require maintenance. They are powered by the scanner using inductive coupling or electromagnetic capture technologies.
The RFID system consists of tags and scanners. The tags contain identification information. The scanners are connected to the tags via radio, read the data from the tags at a distance of about a meter and send the received information to the databases. As the number of tags increases, the data flow between the computer and the reading devices also increases.
Another interesting application for RFID technology is door locks. The first such ideas began to appear a year ago, but only now have the first products appeared.
MyKey 2300 is the world's first lock with an RFID chip as a key (photo 1).
In addition to the main key, the lock can also be opened using a code — in case the user has lost or forgotten their key somewhere, this lock is equipped with a retractable keypad, similar to conventional combination locks.

Photo 1. General view of the world's first MyKey 2300 lock,
the key to which is an RFID chip
The retail revolution may be new, but RFID technology itself is nothing new. It has been around and in use since the 1940s.
During World War II, the U.S. Air Force used RFID tags to identify aircraft.
Today, such tags are used on everything from helicopters to hot air balloons.
Concerned about the spread of mad cow disease, government agencies began requiring accurate livestock identification in the 1980s. Today, tens of millions of cows wear RFID tags in their ears.
RFID chips are also embedded in security tokens, installed on car windshields for automatic toll collection, and attached to packaging to simplify logistics.
While RFID technology has been around for a long time, its widespread use in supply chains will bring significant changes. As RFID technology becomes more widespread in this area, the economics of mass production will drive the cost of tags and scanners down.
Moreover, businesses that invest in installing a product management infrastructure will be able to use it with other applications at no additional cost. The revolution in retail supplier network management will result in new solutions for end consumers.
For example, mobile phone manufacturer Nokia is introducing a kit that turns a regular phone into an RFID scanner. In just a few years, mobile phones and pocket PCs that can scan RFID tags on products will give consumers the ability to automatically
access to information contained on computer networks without having to type in an Internet address. A person will be able to simply scan the RFID tag of any physical object to immediately access text and audio-visual information about that object, such as product descriptions, detailed directions, museum tours, videos, music, and more.
RFID: Pros and Cons
While RFID systems are already making life easier for many people today, not everyone is rushing to embrace these tiny gadgets.
In the United States and Europe, consumer advocates are concerned about the use of RFID tags on retail products, fearing that they will allow companies to track everything from their favorite type of sausage to the size, style, and color of their clothes.
Most industry analysts, however, believe that the benefits of RFID technology in terms of improved customer service will outweigh any privacy concerns. They are convinced that the benefits of RFID far outweigh its drawbacks.
In addition, the Auto-ID Center, an RFID research consortium based at MIT, has proposed giving retailers the ability to turn off RFID tags at the exit of stores.
Although there is no single RFID standard yet, some manufacturers have already started producing such tags.
Since information from an RFID chip can be read from a distance of several meters, civil rights and freedom advocates are concerned about the unauthorized use of such chips outside the store: an intruder with a reading device will be able to read the identifiers of your things and use the obtained information against you (for example, by hacking the database of the desired store and finding out your credit card number).
In short, there are also many options for using RFID for other purposes.
Until recently, the popularization of RFID chips was slowed down by their bulkiness and, most importantly, high cost. It is clear that such devices should be as small and as cheap as possible.
And customers got what they wanted: the media immediately reported two reports about the completion of a development that meets the most stringent requirements for radio identification chips.
The first came from Hitachi, which created the so-called mu-chip, which is less than a quarter of a square millimeter in size and can exchange data over a distance of a quarter of a meter. The short range and the need to connect an external antenna limit the use of this product to trade and services.
Then came a second announcement from the Malaysian government, about the acquisition for an undisclosed amount of intellectual property related to a development by the Japanese company FEC Inc.: the Manathir RFID chip, half a square millimeter in size and priced at 10 cents, suitable for tracking both goods and people (it can even be implanted in the human body).
Its range is not specified, but is apparently several meters.
The Malaysian authorities, where “smart electronic ID cards” have been in use for two years, hope to reduce the cost of these cards sevenfold with the help of the new chip, but they will not stop there and implant Manathir literally into everything that may require subsequent identification.
The prospects of such an initiative are obvious: the state will be able to find out everything about its citizens.
How can an ordinary person who wants to avoid total surveillance exercise his right to privacy? Fortunately, researchers have finally thought about this.
And they have found a solution that is as ingenious as it is simple: you need to make a “jammer” that could counteract reading devices.
And it is best to make it in the image and likeness of the RFID chips themselves: the “jammer” should be a device that copies the work of radio identification chips, with the only difference that in response to scanner requests it will not give out useful information, but random “garbage”.
There are two important points in the operation of such a blocking chip.
Firstly, it should understand requests from a wide variety of reading devices. Secondly, it would be good to give out multiple responses to one request at once.
Then, presumably, the scanner will simply get confused.
This idea belongs to specialists from RSA Security, who have brought it to the stage of a laboratory prototype and hope to manufacture trial microcircuits in the near future.
As an analysis of the latest news publications shows, RFID technology is currently experiencing a kind of boom, the results of which can seriously affect the development of many areas of technical progress.
With this in mind, the following are the most recent examples of RFID technology implementation, which reveal both its advantages and disadvantages.
Examples of positive and negative assessments of the use of RFID technology (according to information from the Internet as of November 2005)
RFID advantages
US introduces RFID passports for tourists and travelers
Tourist visas to the United States will soon be equipped with radio-frequency identification (RFID) tags. As part of the program, passive RFID chips will be placed in tourist visas of foreigners arriving in the United States, allowing for multiple rewriting.
The introduction of this technology will allow for greater control over the movements of foreigners and, if necessary, the ability to count the number of tourists leaving the country without having to stop them for document inspection.
The experiment will last until March 2006 – similar RFID chips will be embedded in documents issued by five major US airports, and after the test period, if the technology is approved by the government, then in all other customs points in the country.
RFID technology is part of the American passport system
Starting in October 2006, the US plans to provide the entire population of the country with a new type of passport. They will be based on RFID chips, which will allow officials at checkpoints and police officers to easily and quickly read the information contained on them.
The new passports will transmit a number of standard personal data, including even a photograph of the passport holder, which will allow the bearer to be instantly identified using special terminals.
In the future, fingerprints and iris scans will be added to this data.
Microchips to track immigrants
The United States is considering surveillance technology that could ensure constant monitoring of an immigrant's location.
As is known, this problem is especially acute in the United States on the border with Mexico and Canada.
The authorities plan to begin issuing special identification devices to foreigners arriving in the United States on foot or by car.
The devices will contain RFID chips that store a unique identification code, which will include such data as the tourist's full name, citizenship, date of arrival and expected departure, and biometric data.
The electronic ID cards will be issued for now in Nogal, Arizona; Alexandria Bay, New York; and Blaine, Washington, as part of a year-long pilot test of the system.
If the practice is accepted, similar electronic ID cards will be rolled out nationwide.
Currently, electronic ID cards have been issued to more than 17.5 million foreigners who have visited the United States since the pilot began.
U.S. Army Rolls Out RFID Tags
The US Department of Defense has notified the US Army that by 2005 all of its suppliers will be required to install RFID tags on all goods they deliver. Only bulk goods and large volumes of liquids will not be tagged with RFID tags.
The military believes that the innovation will allow monitoring and tracking of product deliveries around the world, which means it will be possible to increase the efficiency of the supply system.
RFID chips work by storing identification information about the goods they receive.
Now the contents of a shipping container can be found out without opening it, simply by identifying its RFID tag.
By January 2005, all suppliers will install passive RFID tags with information about each individually supplied product stored in memory.
Built-in radio tags can track goods and customers
RFID tags are already being used to track cattle, identify lost pets and allow commuters to drive their cars through toll gates into town without stopping.
At Prada's new store in the upscale New York suburb of SoHo, sensors in the fitting room walls can detect what clothes a customer is trying on and show whether the store has them in other colors, sizes or fabrics.
The baseball-card-sized tags cost about $4 each and are removed during checkout and re-attached to new items as the counter loads.
As an anti-theft technology, RFID makes sense in a store where a typical T-shirt can sell for $400 or more.
With tags soon shrinking to the size of a grain of rice and costing as little as 5 cents, RFID proponents suggest that in the not-too-distant future, dirty shirts could tell washing machines how they should be washed, and refrigerators could place an order with the grocery store when milk is running low.
Sokymat uses RFID tags to meet new EU regulations
EU legislation has recently regulated the use of identification systems for dogs, cats and ferrets travelling within and between EU member states.
The main objective of this initiative is to prevent epidemics in Europe.
RFID for priceless manuscripts
The Vatican Library has begun using radio frequency identification technology as the basis for its management system.
TESCO uses radio frequency tags
Tesco, the UK's largest retailer, has used radio frequency tags on Gillette razor blades to track the movement of goods.
Find counterfeit products with RFID
RFID technology, as well as the use of an electronic product code, can help manufacturers protect their brands from counterfeiting.
RFID system reduces risk of child abduction
Eagle Tracer specialists have proposed using one of the most promising solutions – RFID to protect children.
To combat counterfeiting, pills will be equipped with radio transmitters
US authorities are proposing to combat counterfeiting of medicines by issuing electronic “passports” to each box of medicines.
A solution for “five stars”
Radio frequency identification (RFID) has made new technologies available to hotels, improving security, reducing costs and improving service.
RFID chips and the euro
The European Central Bank is working on a project to equip every euro banknote with a radio frequency tag.
Safe beef: from farm to steak
A RFID tag attached to the ear or implanted in the muscle of an animal can guarantee that the entire path of meat is tracked from farm to steak
RFID disadvantages
Americans against product labeling technology
Wal-Mart's decision to label all products sold in its giant supermarket chain has caused a storm of indignation among consumers.
It has gotten to the point that human rights activists are preparing a corresponding draft law.
Not long ago, Wal-Mart decided to label the products it sells with RFID tags.
In response, the human rights organization CASPLAN (“Consumers Against Retailers Interfering with Privacy”) has put forward a draft law that would require all products containing these tags to be labeled accordingly.
The draft law also contains strict measures aimed at limiting the use of information obtained using RFID tags.
And although this technology is still in its infancy, consumers believe it is better to start protecting themselves now.
RFID technology is not secure enough
Unfortunately, the victorious march of RFID across the planet has been considerably overshadowed in recent months by the increasing frequency of statements from security experts, accusing the new technology of insufficient protection.
RFID tags, which allow for small payments, marking product packaging, or even serving as a kind of identification device in a car anti-theft system, have indeed proven to be insufficiently secure against the simplest hacking methods using simple devices with cheap processors.
RFID chips are especially vulnerable, as they do not even require direct contact to be hacked.
A hacker only needs to be near a potential “victim.”
Thus, until encryption standard developers provide RFID tags with sufficiently robust protection, using this technology in areas where hacking a system can cause significant losses (cars, gasoline payments, etc.) is unsafe. RFID technology is not secure enough.
Gillette refuses to accept “marked” goods
The desire of companies to use tags on their products has not met with decent understanding from consumers.
The first to fall under the wrath of the masses was Gillette.
Consumers in many countries have already expressed their protest against the use of high-tech tags on products.
Not long ago, trial batches of Gilette products with RFID tags appeared in a Tesco store in Cambridge. This product was subjected to a public boycott.
After gauging consumer reaction, the company stopped testing and recalled tagged merchandise from the store.
Walmart to Remove RFID Tags
Marketing experts say the new technology, known as RFID, could revolutionize retail by personalizing service and enabling efficient inventory.
But not everyone is happy about it.
The use of such tags caused a storm of indignation from consumers. Walmart decided to stop this experiment. Walmart management officially announced that large-scale tests of RFID tags that the company planned to conduct are canceled.
However, this information cannot be considered a victory for consumers. As it turned out, the tags will not die completely: they will be used not in stores, but in warehouses and distribution centers. So consumers will still be subject to an attack on their confidential information.
Visiting the library threatens the reader's privacy
Libraries in the US are considering replacing barcodes on books with RFID tags.
These RFID tags would presumably be turned off when a person leaves the library with books.
From now on, it will be possible to track a person using the books in their bag, since no one can guarantee that they cannot be turned back on later.
Recently, some US citizens have been concerned about the provisions of the Patriot Act, which now give bailiffs access to information about library visits by readers.
RFID tags are implanted under the skin
Corporations are trying to tempt US residents to get RFID chips that are implanted under the skin.
These chips could replace credit cards, passports, and much more.
A huge advantage and disadvantage is that they cannot be lost.
They can also be used for unauthorized surveillance of the owner of the chip.
The system is known as VeriPay and looks like a miniature chip under the skin of the hand.
The manufacturer draws attention to the fact that this will solve the problem of losing magnetic cards, make intentional theft more difficult and generally make the user's life much easier.
In response to skeptical statements about the negative aspects of having such a chip, the company responds that the chip can be removed at any time.
However, the security issues of this system do not provide a fundamental solution — after all, with not very sophisticated equipment, thieves can theoretically eavesdrop on the signals emitted by the chip and force their devices to reproduce them.
More determined thieves can also extract the chip by force. To help promote the innovation, the owners of VeriPay suggest that those wishing to receive the chip register in advance — for statistics.
RFID tags — a turning point in technology
RFID tags are on track to become one of the most widely used technologies in retail today, but there are several factors that are holding back RFID from becoming mainstream.
While RFID chips are essentially high-tech bar codes that can be read from a distance and even through walls, wary potential buyers argue that RFID technology is too crude and expensive to be widely adopted.
Nevertheless, Wall Mart and other retail giants are eager to experiment with RFID.
The authority of these huge retail chains is sufficient to moderate the skepticism of others.
For now, RFID tags are mainly focused more on packaging of large quantities of items — containers and pallets, than on each individual product.
Summarizing the results of the analytical review of the state and prospects for the development of RFID technology, the following conclusions can be made.
Until recently, the main factors holding back the implementation of RFID technology were the relatively high cost of the radio frequency tag, the lack of international standards, and the resistance of public organizations fighting consumer rights violations.
Currently, a radio frequency tag costs from several tens of dollars to several tens of cents, depending on its functionality.
Of course, with mass production, its cost will decrease significantly, but there are strong doubts that it will be equal to the cost of a paper label with a bar code, which is present on every product today.
Therefore, today radio frequency tags are used to mark objects whose value significantly exceeds the cost of the tag itself.
Today, radio frequency identification is used to mark vehicles, returnable containers (shipping containers, pallets, kegs and other containers for transporting liquids), containers for collecting garbage and waste, marking rare wines, rental items such as bicycles, books and other paper carriers of important information (in medicine, these are medical records), instruments and animals.
The first reports are appearing about the use of RFID systems for marking individual goods in retail and for warehouse accounting.
So, over time, the cost of a radio frequency tag will decrease so much that it will be present on every product packaging and on the product itself.
But for this to happen, manufacturers of radio frequency identification systems must adhere to a single standard.
Since the production process of RFID systems is carried out in different countries, the standard must be international, the systems themselves must be unified and compatible so that radio frequency tags and reading devices produced by different companies can work with each other without any problems.
Such standards have now been developed and are in the process of being adopted.
The only serious obstacle to the introduction of RFID technology remains the resistance of the public fighting for consumer rights.
But as the experience of introducing modern technologies into our lives shows, you have to pay for everything and a compromise will definitely be found.
Moreover, RFID technology, by eliminating the weakest link in automated control systems, will probably soon make a real revolution in industry, agriculture, transport and other areas, including special equipment.
Currently, taking into account the development prospects, RFID technology has no serious competitors.

Добавить комментарий