Wireless technologies of the last inch.
UKOV Vyacheslav Sergeevich, Candidate of Technical Sciences
PONOMAREV Andrey Alekseevich
The problem of the so-called “last mile” in information transmission systems has long attracted the attention of specialists: how to reliably deliver information to the user at the last, usually most difficult stage of delivery.
With the active development of information technologies, with the avalanche-like expansion of the range of peripheral devices, taking into account security, this problem has become even more acute and has already grown into a problem of the “last inch”.
The article analyzes the current capabilities and prospects for the development of technologies that provide a solution to this problem.
With their unique capabilities, wireless communication technologies are increasingly conquering the world, making it increasingly mobile and active.
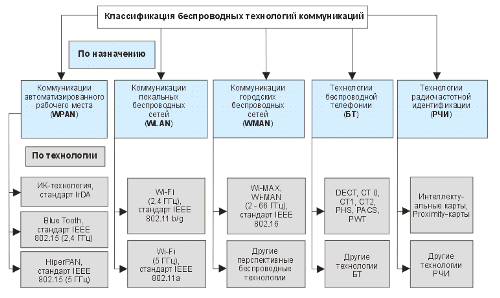
Fig. 1 shows a classification of existing and promising wireless communication technologies that provide a solution to the “last inch” problem.
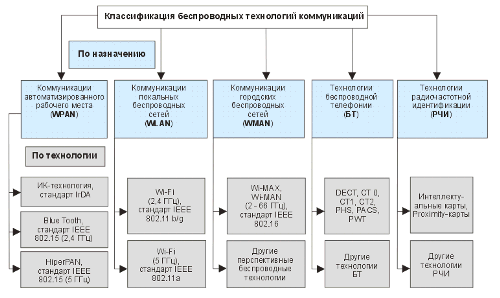
Fig. 1. Classification of wireless communication technologies
Below are the results of a detailed analysis of wireless communication technologies that provide the greatest solution to the “last inch” problem.
IR technology
This technology is perhaps one of the “oldest” wireless technologies of the “last inch” and the most developed at present.
It has found wide application for operational wireless communication between office computers, in remote controls for household appliances (TVs, music centers, air conditioners), etc.
Today it is actively used for communication between digital cameras and mobile radio telephones with a computer and for a number of other applications.
IR technology allows for wireless communication in the infrared (IR) range between devices located several meters away.
Infrared communication – IR (InfraRed) Connection – is safe for health, does not create interference in the radio frequency range and ensures confidentiality of transmission.
Currently, there are infrared systems of low (up to 115.2 kbps), medium (1.152 Mbps) and high (4 Mbps) speed.
Low-speed systems are used to exchange short messages, high-speed systems are used to exchange files between computers, connect to a computer network, output to a printer, projection device, etc.
Higher data rates are expected to appear in the near future, which will allow the transmission of “live video.”
To ensure compatibility of equipment from different manufacturers, the Infrared Data Association (IrDA) was created in 1993.
Currently, the IrDA 1.1 standard is in effect, along with which there are still proprietary systems from Hewlett Packard (HP-SIR) and Sharp (ASK IR).
The emitter for IR communication is a light-emitting diode with a peak spectral power characteristic at a wavelength of 880 nm.
This light-emitting diode produces a cone of effective radiation with an angle of about 30 degrees during transmission.
PIN diodes are used as receivers, effectively receiving IR rays in a cone of 15 degrees. The IrDA specification provides a bit error rate of no more than 10-9 at a range of up to 1 m and daylight (illumination — up to 10 klux).
Binary modulation and various coding schemes are used to transmit signals.
The software allows you to establish a connection to a local network (to access the Internet, use network resources), print data, synchronize data from a PDA, mobile phone and desktop computer, download captured images from a camera to a computer and perform a number of other useful actions without worrying about cable management.
Bluetooth wireless technology
Bluetooth technology is designed to provide universal network connectivity for:
- organization of data and voice transmission channels;
- replacement of cable connections;
- the widespread use of compact and inexpensive network adapters built into all kinds of communication equipment, computers and household appliances.
The intensive development of Bluetooth technology is expressed by equipping various devices with a Bluetooth interface.
This process is also stimulated by the fact that Bluetooth is recognized as a new standard for wireless communication, as well as the involvement of new companies in the Bluetooth SIG initiative group, beginning the development and release of products using Bluetooth technology.
Bluetooth technology is defined by the following key parameters:
- frequency range – 2.44 GHz – this is the ISM band – industrial, scientific and medical applications (ISM – industry, science, medicine);
- FHSS – frequency hopping with spread spectrum, when a radio transmitter transmits a signal, jumping from one operating frequency to another according to a pseudo-random algorithm;
- time division duplex (TDD), which provides full-duplex transmission of information;
- support for isochronous and asynchronous data transmission services, which ensures easy integration with TCP/IP, while slots (time intervals) are deployed for synchronous packets, and each packet is transmitted on its own radio frequency;
- the topology of the local radio network is organized according to the principle of multiple piconets interacting with each other via a standard radio channel, where the piconet always includes one master station synchronizing traffic in the piconet.
The areas of application of Bluetooth include almost all spheres of action — radio telephones and pagers, modems, local area network adapters, desktop computers, laptops, hand-held computers and much more.
Bluetooth provides radio communication within 10m/100m and does not require direct visibility of the signal source and the subscriber.
Advantages of the technology:
- uses the unlicensed ISM frequency range;
- ease of use;
- the ability to replace any cables;
- galvanic isolation of connections;
- the ability to connect mobile computers to other mobile devices;
- automatic “plug and play” configuration;
- support for voice and data transmission;
- the ability to create scalable microgrids;
- immunity to interference, which is ensured by transmitting signals using the Frequency Hopping Spread Spectrum method;
- small dimensions and ease of integration;
- low power consumption compared to the devices used;
- use worldwide;
- open standard;
- the ability to work with different devices;
- reliability and resistance to external influences.
The main features and technical characteristics of Bluetooth are presented in Table 1.
Table 1. Main features and technical characteristics of Bluetooth technology
| Characteristics | Value of parameters |
| Range, m | Up to 10/100 |
| Technical data transfer rate, Mbit/s | Up to 4 |
| Maximum data transfer in synchronous mode, kbit/s | Up to 432.6 |
| Maximum data transfer rate in asymmetric mode | 57.6 K – 723.3 kbit/s |
| Protocol | Switched/Packet Mode Combination |
| Maximum Piconet Population | 8 |
| Radio Frequency, GHz (ISM Band) | 2.4 |
| Frequency Usage | Frequency Hopping System |
| Number of Sub-Frequencies | 79 |
| Number of Frequency Hops Per Second | 1600 |
| Maximum output power, dB | 20 |
| Output power classes | 1, 2 , 3 |
| Power distribution by classes, dB | Class 1: 0…20 Class 2: -6…+ 4 Class 3: 0 |
| Frequency deviation, kHz | ±140…175 |
| Standby By Mode Listen Rate | Every 1.28 sec |
| Connection Security | — Authentication — Cryptoprotection with a key length of 8 to 128 bits — Using application programs |
Bluetooth is the name given to the new IEEE 802.15.1 standard of modern wireless technology that uses radio waves to transmit data over short distances and replaces cables for connecting mobile and/or fixed electronic devices.
This standard allows almost any device to be connected to each other with minimal user intervention: mobile phones, laptops, printers, digital cameras, and even refrigerators, microwave ovens, air conditioners.
The technology also offers home appliances and portable devices wireless access to various types of networks, including: LAN, PSTN, cellular networks of mobile phones and the Internet.
The use of Bluetooth technology creates a wide range of new services, among which we highlight the following:
- automatic synchronization of computers and mobile phones (for example, as soon as new data is entered into the address book on a laptop, the corresponding entries in the desktop computer are automatically modified, and vice versa);
- automatic backup synchronization, which provides automatic transfer of information from one PC via a mobile phone to another PC;
- connection of all peripheral devices to each other, which provides wireless connection of the PC with a printer, scanner and local area network;
- rapid compilation of electronic messages using a portable PC and their immediate sending using a mobile phone;
- wireless connection of the car kit «hands free» with a cell phone in a hidden state, which allows «hands free» not only to connect to it, but also to perform voice control of the phone (on/off, dialing, etc.);
- wireless transmission of photos and video clips via a mobile phone with the ability to add the necessary comments using the keyboard on the phone or laptop before sending them to the recipient;
- connection of several subscribers for prompt exchange of information;
- using a laptop to access the Internet regardless of the type of connection — via a mobile phone, modem or local network;
- using a laptop as a speakerphone (by connecting a wireless headset to a laptop, you can use it anywhere).
Local wireless network technologies
IEEE 802.11a/b/g (Wireless LAN) standards describe the interaction of devices at the physical and transport levels for building local wireless networks, such as home, intra-office, warehouse, industrial, and public wireless networks. The main features of these standards are:
- random access to the medium (devices do not have priority for data transmission, but contention for the channel is used, while the bandwidth for the station is usually determined by the conditions of radio visibility and the workload of the access point by other subscribers);
- weak security (implemented authentication, authorization and cryptographic protection mechanisms are optional and rather weak).
The WEP (Wired Equivalent Privacy) algorithm described by the 802.11 standard is used for encryption. In this case, encryption is used with a 40-bit static key using the RC-4 algorithm.
The station authentication process occurs as follows.
In response to a broadcast request from a subscriber device, the access point sends a fragment of a well-known poem.
The subscriber to whom the text was addressed (it is distributed over the air in unencrypted form) encrypts it with his key and sends it back to the access point, which, having encrypted the same text with its own key, compares them.
Based on the coincidence of the encrypted texts, the access point makes a decision on authentication (to open access to the local network for the subscriber, or to reject it).
Thus, two sources of possible vulnerability can be identified: interception of traffic and sending a probe into the network. It is known a priori that the keys are static and their length can be calculated from the packet size.
By sending a probe, for example, ICMP packets of known length and known content via the Internet, directed to a subscriber station, and intercepting it on the radio, already encrypted, it is sufficient to simply determine the encryption sequence.
Indeed, for packet self-synchronization, the initialization vector (IV) increases by one on each packet and is reset to zero on each device restart.
In this case, the repeatability of the “IV – coding sequence” combination is achieved already on numbers of about 16,000, which can happen quite quickly under conditions of fairly intense traffic. Next, the key that encrypts the data for transmission is determined.
From this we can conclude that if encryption is not performed at levels above the transport level and using other technologies, then all subsequent data can be intercepted and decrypted.
Therefore, to ensure a modern level of security in local wireless networks, it is necessary to encrypt data at higher levels (network and above) using various standard methods, for example, VPN, etc.
Broadband wireless access technologies
The IEEE 802.16 fixed broadband wireless access standard is one of the most promising.
Currently, it is gaining popularity in discussions of the prospects for the development of wireless telecommunications, although its name has not yet been established and in discussions it usually appears as Wi-MAX, Wi-MAN, etc.
The main idea of the standard is the use of wireless technologies to build operator city-scale networks, and the main task to be solved is to ensure the security of the transmitted information. Let us briefly consider how security is ensured in the specified standard.
The main difference of this wireless network is that the base station (BS) is a modular design in which several modules with their own types of interfaces can be installed, but at the same time, administrative software for network management is always supported.
The subscriber kit (SC) is a device that has a serial number, address, and digital signature (standard X.509), while the validity period of the SC digital signature is 10 years. It is important to note that according to the standard, none of the parameters should be changed.
After the SC is installed at the client and power is supplied, the SC is authorized at the base station using a certain radio signal frequency, after which the BS, using the above identification data, transmits the configuration file to the subscriber via the TFTR protocol.
This file contains the necessary information about the sub-range for receiving and transmitting data, the type of traffic, the available bandwidth, the schedule for sending keys for encrypting traffic, and other information. The configuration file is created automatically after the administrator of the AK system enters the subscriber database with the assignment of certain access parameters.
After the configuration procedure is completed, the AK is authenticated at the base station as follows:
- The AC sends an authorization request, which contains an X.509 certificate, a description of the supported encryption methods, and the necessary additional information;
- The BS sends a response to the authorization request, which contains an authentication key encrypted with the subscriber's public key, a 4-bit key for determining the sequence necessary to determine the next authorization key, and the key's lifetime.
After a period of time determined by the system administrator, re-authorization and authentication occur and, if successful, the data flow is not interrupted.
It is necessary to dwell in more detail on the key information. According to the IEEE 802.16 standard, several keys are used in a communication session:
- АК
-
- (Authorization key) – a key used to authorize the АК at the base station;
-
- TEK (Traffic Encription Key) – a key used for cryptographic protection of traffic;
- KEK (Key Encription Key) – a key used for cryptographic protection of keys transmitted over the air.
These keys are used in the РКМ (Privacy Key Management) algorithm.
Another feature of this standard is that, to ensure uninterrupted operation in an environment with packet loss, two keys with overlapping lifetimes are used at any given time.
Thus, the use of a large number of sufficiently long dynamically changing keys, as well as the establishment of secure connections using a digital signature, ensure the specified security of transmitted information in wireless broadband access networks.
Wireless telephony technologies
DECT standard(Digital European Cordless Telecommunications) for wireless telephony was introduced in 1992 by the European Telecommunications Standards Institute (ETSI).
In the same year, the European standard for the DECT radio interface (ETS 300 175) was adopted.
In 1993, several major telecommunications corporations (Ericsson, Siemens, Olivetti) introduced the first wireless communication and data transmission systems based on the DECT standard. After DECT was approved in many countries outside Europe, the standard changed its name to Digital Enhanced Cordless Telecommunications.
CEPT (Conference of European Postal and Telecommunications Administrations) in accordance with EEC Directive 91/287/EEC prescribes the allocation of the 1880-1900 MHz frequency band for DECT. Currently, there are several international standards for wireless telephony systems: CT0, CT1, CT2, PHS, PACS, PWT, DECT and others.
The CT0 and CT1 standards are analog standards with limited capabilities and a number of serious shortcomings: call blocking, mutual interference between systems, and the impossibility of ensuring the secrecy of information transfer.
These standards are not used in modern cordless communication systems. The first digital cordless communication standard CT2 turned out to be a good radio technology, providing high quality voice transmission and using dynamic channel allocation (DCA). But it does not have the ability to transmit data and flexibly change the frequency band, as is done in DECT.
In North America, the PWT (Personal Wireless Telecommunications) and PWT-E (Personal Wireless Telecommunications Enhanced) standards of the Telecommunications Industry Association (TIA) are used to provide personal mobile radio access, which provide the same basic services as DECT.
Using a similar communication scheme, they work with different types of modulation and frequency planning.
These standards may be widespread in some Latin American countries. PWT operates in the unlicensed 1910-1920 MHz band in the USA, PWT/E is an extension of the licensed 1850-1910 and 1930-1990 MHz bands. PWT and PWT-E use the basic DECT structure, so they coexist on a common spectrum band.
The American PACS (Personal Access Communications System) differs from DECT not only in its dedicated frequency range, but also in the need for frequency planning, frequency duplexing of receiving and transmitting channels, and time division multiplexing.
PACS and PWT systems are practically not used in Europe.
Since the PHS (Personel Handyphone System) standard was created in Japan, it is poorly developed in European countries and is mainly used in the Asian region. Today, more than 50 companies in various countries of the world are connected with the production of DECT equipment in one way or another. Table 2 presents some comparative characteristics of the DECT, PHS and PACS standards.
Table 2. Comparative characteristics of the DECT, PHS and PACS standards
| System parameter | DECT | PHS | PACS |
| Distribution region | Europe, Asia | Japan, Asia | USA, Canada |
| Operating frequency range, MHz | 1880 – 1900 | 1895 – 1918 | 1850 – 1910/1930 – 1990 |
| Frequency channel spacing, kHz | 1728 | 300 | 300 |
| Access scheme | TDMA/TDD | TDMA/TDD | TDMA/FDD |
| Number of channels per carrier frequency (time slots) | 12 | 4 | 8 |
| Data transfer rate in radio channel, kbps | 115.2 | 384 | 384 |
| Power of radio remote control (mW) | 10 | 10 | 200 |
| Communication range, m | 50 – 300 | 50 – 150 | 300 – 500 |
| Communication secrecy | Authentication, encryption | Authentication, encryption | Authentication, encryption |
| Start of operation | 1996 | 1995 | 1997 |
| Mobility, km/h | Up to 20 | Up to 70 | Up to 70 |
From the very beginning, the DECT standard was developed as a means of providing access to a telecommunications network of any type and for a variety of applications:
- for home and small office;
- microcellular cooperative systems;
- radio access systems (WLL);
- GSM network access systems;
- public microcellular systems (PMS);
- access to the local network.
DECT provides: voice telephony, fax, modem, e-mail and many other services.
DECT makes it possible to create a full-fledged telecommunications environment of wireless radio access (WLL) with a set of integrated services of fixed and mobile communications.
This provides:
- telephone services of the public network;
- facsimile transmission (G3 standard, maximum speed 4.8 kbps) and data transmission (maximum speed 9.6 kbps) via speech codec modem with compression up to 32 kbps;
- facsimile transmission (G3 standard, speed 28.8 kbps via modem; 64 kbps via speech codec modem without compression via a channel with noise protection).
DECT technology is a common access technology, while CTM (Cordless Terminal Mobility) provides terminal roaming services between DECT access networks.
In places where DECT radio coverage is provided by a system (home, office or public), a cordless telephone with the appropriate rights can service both incoming and outgoing calls.
In this case, the mobile terminal is registered only in one system with one phone number. Thus, communication is provided in any place where the DECT system is present.
Moreover, the terminal has the same network number in all networks, so incoming calls are not lost. Mobility is provided not only within the GSM network, but interaction with any network that supports mobility, for example, with the ISDN network, can also be carried out.
The principles of interaction between DECT and GSM systems are reflected in the specification of the GSM Internetwork Protocol (GIP), included in the DECT standard.
Such access is provided on the A interface of the GSM network (to the MSC).
In this case, the GSM network is unaware of the existence of DECT and perceives it as a base station system (BSC).
This allows building mobile DECT networks based on the GSM terrestrial infrastructure, since GSM networks effectively support mobility. For GSM network operators, it is possible to use dual-standard GSM/DECT mobile terminals.
DECT technology is called a microcellular or picocellular communication system, since the principle of building such systems is similar to the principle of building traditional cellular systems.
The only essential difference is that the cell size in DECT is limited to hundreds of meters (since the radiated power is 10 mW per channel). The architecture of a DECT network depends on the area of application, but, like many cellular communication systems, DECT includes base stations and mobile terminals.
A typical structural diagram of a DECT system includes:
- interface and control unit (IWU);
- control controller (CCFP);
- base station (RFP);
- mobile terminals (PP).
The control controller provides control of all base stations. All the main centralized functions of mobile terminals are performed in this block.
The switching and control unit ensures the interfacing of the DECT system with telephone networks, such as a city or corporate PBX. In addition, this unit implements the function of echo cancellation of the speech signal.
The switching and control unit also ensures the conversion of signaling protocols between the telephone network and the DECT subsystem.
Base stations determine the coverage area and capacity of the system. The size of the coverage area (cell) of each base station depends on where it is located.
Typical values are 30-50 meters indoors and about 150-300 meters for open spaces.
The coverage area is determined by the number of base stations included in the system. Directional antennas and repeaters are used to increase the coverage area of base stations.
A repeater (P) increases the coverage area of a base station by 50%.
The DECT standard is based on digital data transmission and radiotelephone technology with time division multiple access (TDMA). The main technical characteristics of DECT standard systems are presented in Table. 3.
Table 3. Main technical characteristics of DECT standard systems
| Operating range | 1880…1900 MHz |
| Number of frequencies | 10 |
| Frequency spacing | 1.728 MHz |
| Access method | MC/TDMA/TDD |
| Number of channels per frequency | 24 |
| Total transmission rate on 24 channels | 1.152 Mbit/s |
| Modulation method | GMSK |
| Output power | 10 mW (average) |
The DECT technology system has the following properties:
- high-capacity structured cellular access network;
- mobility within the entire network;
- flexible and powerful identifier system;
- high efficiency of radio spectrum use;
- stable operation in congested and aggressive radio environments;
- high-quality and reliable radio access;
- transmission quality comparable to that of wired networks.
The use of radio access technology that enables mobility involves significant security risks. The DECT standard provides measures to counteract the natural security flaws inherent in cordless communications.
Efficient registration, authentication and encryption protocols have been introduced to prevent unauthorized access, and the advanced encryption concept provides protection against eavesdropping.
Registration is the process by which the system allows a specific DECT handset to be serviced. The network operator or service provider provides the PP user with a secret registration key (PIN), which must be entered in both the RFP and the PP before the procedure can begin.
Before the handset initiates the actual registration procedure, it must also know the identity of the RFP to which it is to be registered (for security reasons, the registration area may be limited to one dedicated (low-power) RFP system).
The procedure is usually time-limited, and the registration key can only be used once, which is done specifically to minimize the risk of unauthorized use.
Registration in DECT can be done “over the air”.
After establishing radio communication, both sides verify that the same registration key is used.
Identification information is exchanged, and both sides calculate a secret key, which is used for authentication each time a connection is established and is not transmitted over the air.
A mobile DECT handset can be registered to several base stations.
For each registration session, PP calculates a new authentication key, linked to the network to which it is registered. New keys and new network identification information are added to the list stored in PP, which is used during the connection process. Handsets can only connect to the network to which they have access rights (the network identification information is contained in the list).
Handset authentication can be performed as a standard procedure at each handshake. During the authentication session, the base station verifies the authentication key without transmitting it over the air.
The principle of “non-revealing” identification information over the air is as follows: RFP sends a random number to the handset, which is called a “challenge”.
The handset calculates the “response” by combining the authentication key with the received random number, and transmits the “response” to the base station.
The RFP also calculates the expected “response” and compares it with the received “response.” The comparison results in either continued connection or disconnection.
If someone is trying to intercept signals on the air, then in order to crack the authentication key, they need to know the algorithm for identifying the key from the “challenge” and “response.” Uncovering the algorithm for identifying the key requires enormous computing power.
Therefore, the cost of extracting the key by analyzing the authentication signals is incredibly high.
The authentication process uses an algorithm to calculate a “response” from a “challenge” and an authentication key in the handset and at the base station.
It is a way of sending the user's identification information in encrypted form over the air to prevent it from being stolen.
The same principle can be applied to user data (e.g. voice transmission). During authentication, both parties also calculate an encryption key. This key is used to encrypt the data transmitted over the air.
The receiving party uses the same key to decrypt the information. In the DECT standard, the encryption process is part of the standard (although not mandatory). Thus, the signal is scrambled and forcibly encrypted.
In this case, hack-resistant crypto protocols with open key transfer are used.
The use of encryption is not mandatory due to restrictions on the distribution and use of encryption technologies in different countries.
Registration, authentication and encryption algorithms provide a fairly high level of protection against unauthorized access and eavesdropping.
Radio frequency identification technologies
Radio frequency identification and object registration systems (abbreviated RFI-systems, from English RFID – Radio Frequency IDentification) – is a set of electronic means of automated control and collection of information about various objects, such as transport, personnel, cargo, goods, valuables, etc.
RFID systems became widespread in the early 90s.
Compared to the then existing methods of identification by barcode, magnetic stripe or contact key (TouchMemory technology from DALLAS), RFID systems had a number of significant advantages.
They made it possible to significantly speed up the identification process, did not require a special location of the object relative to the reader, as in barcode systems, were more reliable, durable and protected than magnetic stripe systems, and worked contactlessly, unlike TouchMemory systems.
Therefore, RFID systems are currently becoming increasingly widespread in trade, payment banking systems, access control systems, inventory control systems, etc.
The composition of a typical RFID system is shown in Fig. 2.
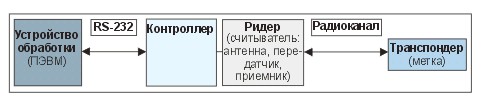
Fig. 2. Composition of the radio frequency identification system
The tag and the reader are connected by a radio frequency channel. The tag consists of a transceiver and an antenna.
The reader also contains a transceiver and an antenna. The controller can be part of the reader, or it can be made as a separate device. The controller forms an interface for communication with the PC.
Using the transceiver and antenna, the reader emits an electromagnetic field of a certain frequency.
Radio frequency tags that enter the reading field “respond” with their own signal containing certain information (for example, a product code) on the same or a different frequency. The signal is captured by the reader’s antenna, the received information is decoded and transmitted through the controller to the computer for processing.
The controller performs several functions.
The first is the docking of the reader with the computer ports: USB, RS-232, RS-485. The second is the multiplexing of several readers with one computer.
Some developer companies integrate the reader, antenna and controller in one product, while others, on the contrary, in different ones. The computer is directly involved in storing, processing and using the information received from the tags in various user programs.
Currently existing RFID systems from various manufacturers, as a rule, differ in the carrier frequency of the signals used, the type of modulation, the radio exchange protocol and the volume of information returned by the transponder.
Recently, a number of organizations have attempted to standardize these characteristics. This primarily concerns the carrier frequency of the signals.
Currently, there are three main frequency ranges in which RFID systems operate:
- low-frequency range (100–150 kHz);
- mid-frequency range (10–15 MHz);
- high-frequency range (850–950 MHz and 2.4–5 GHz).
Among the low-frequency RFID systems widely used on the Russian market, it is worth noting transponders operating at a frequency of 125 kHz (protocol of the Swiss company EM Microelectronic Marin).
These transponders use amplitude-modulated signals and Manchester code. Transponders from Temic, Atmel, Microchip and transponders manufactured in Russia by Angstrem have a similar exchange protocol.
The range of such systems is about 20 cm. Texas Instruments produces RFID system equipment operating at frequencies of 132 – 134 kHz, using frequency modulation of the signal and a different exchange protocol from other companies.
The range of such systems reaches two meters, and the exchange protocol has high noise immunity. The main results of the comparative analysis are presented in Table 4.
Table 4. Main results of the comparative analysis of RFID systems
| Advantages | Disadvantages |
| Low-frequency RFID systems | |
| — low cost; — small weight and dimensions of tags
|
— low radio speed; — short radio communication distances; — technological complexity of manufacturing highly inductive transponder antennas; — impossibility to distinguish between several transponders simultaneously located in the reader's antenna field; — large dimensions of reader antennas |
| Mid-frequency RFID systems | |
| — high speed of radio communication; — small weight and dimensions; — technological simplicity of manufacturing highly inductive transponder antennas; — use of anti-collision protocols that provide the ability to distinguish between several transponders simultaneously located in the reader's antenna field |
— short exchange distances between the reader and the tag; — low speeds of tag movement relative to the readers, at which exchange is possible |
| High-frequency RFID systems | |
| — high speed of radio exchange; — long ranges of radio exchange; — ease of manufacturing highly inductive transponder antennas; — ability to distinguish between several transponders simultaneously located in the reader's antenna field; — high speeds of tag movement relative to readers, at which exchange is possible |
— large weight and size parameters; — high cost of equipment |
It should also be noted that spiral or magnetic antennas of low-frequency transponders are large in size and difficult to transport.
This leads to high costs for manufacturing transponder housings and, ultimately, to their high cost.
In general, the low cost of low-frequency transponders ($1.2 – 1.5) and readers ($20 – 30) allows for the implementation of inexpensive access control systems, time and attendance systems, etc.
The transition to the megahertz frequency range allowed developers to get rid of the above-mentioned shortcomings.
The standard frequency in the mid-frequency range for the production of RFI systems is 13.56 MHz.
A number of well-known manufacturers have developed transponder microcircuits at this frequency — these are Philips, Microchip, Texas Instruments and many others.
The advantages of mid-frequency RFI systems, including high data rate and small weight and size parameters, make them very attractive.
They can be used to transmit information over short distances at low speeds of movement of tags relative to readers.
The transition of RFID system developers to the high-frequency range is due, first of all, to the need to increase the speed of information exchange between the reader and the tag, as well as to increase the distance between them.
High-frequency transponder devices are usually designed for identification at fairly large distances (10 — 15 m) of objects moving at speeds of up to 200 km/h. In the modern RFID market, such transponders are primarily represented by products from Amtech, Baumer Ident, Balogh, WhereNet and Micro Design ASA.
Radio frequency tags deserve special attention.
They usually include a receiver, transmitter, antenna and memory unit for storing information.
The receiver, transmitter and memory are designed as a separate microcircuit (chip), so it seems that the radio frequency tag consists of only two parts: a multi-turn antenna and a chip.
Sometimes a power source (for example, a lithium battery) is included in the tag design.
Tags with power sources are called active.
The reading range of active tags does not depend on the energy of the reader.
Passive tags do not have their own power source, and the energy required for operation is obtained from the electromagnetic signal coming from the reader.
The reading range of passive tags depends on the energy of the reader.
The advantage of active tags compared to passive tags is a significantly greater, 2-3 times, information reading range and a high permissible speed of movement of the active tag relative to the reader.
The advantage of passive tags is their virtually unlimited service life (they do not require battery replacement).
The disadvantage of passive tags is the need to use more powerful information reading devices with appropriate power sources.
Thus, active tags are advisable to use for transmitting information over tens of meters in motion. Passive tags can be used for long-term storage of information, due to their energy independence.
Information can be entered into the memory of a radio frequency tag in various ways, which depend on its design features.
The following types of tags are distinguished:
- RO
- WORM
– tags (Read Only), which only work to read information. The data required for storage is entered into the tag memory by the manufacturer and cannot be changed during operation.
- – tags (Write Once Read Many) for single recording and multiple reading of information. They come from the manufacturer without any user data in the memory device. The necessary information is written by the user himself, but only once. If it is necessary to change the data, a new tag will be required.
- R/W
- – tags (Read/Write) for multiple recording and multiple reading of information.
R/W tags have the main advantage: the identification tag data can, if necessary, be changed.
RO tag data is recorded only once (during manufacturing), while the information stored by a radio frequency R/W tag can be changed, supplemented or even replaced with other information (except for the identification code).
Thus, tags with multiple writes and multiple reads of information are of the greatest interest and are more promising. Table 5 presents the generalized parameters of modern RFID systems.
Table 5. Generalized parameters of modern RFID systems
| Company | Equipment name | F, MHz |
Weight,
g |
Dimensions, mm | DT, оС | D, m | V, kbit/s |
W , kbyte | Price, $ |
| Texas Instruments | Antenna RI-ANT-G01E | 0 ,1342 | 425 | 200x200x25 | -30..+60 | 2 | |||
| Reader RI-STU-MRD1 | 5 | 38х29х13 | -20..+50 | ||||||
| Label | |||||||||
| Baumer Ident | PC3352 reader | 2450 | 4000 | 300х200х85 | 0…+50 | 4 | 40 | — | 6800 |
| PC3104/33A tag | 100 | 87х64х30 | -40..+70 | 32 | 350 | ||||
| PC3312 Antenna | 1300 | — | 5060 | ||||||
| Balogh | HF-RSR0945 reader | 2450 | 1500 | 263х178х30 | 10 | — | 3412 | ||
| Mark HF-TCP0141 | 15 | 85.6х54х3.5 | -20..+70 | 0.02 | 22 | ||||
| Omron | V620-CD1D reader | 2450 | 360 | 165х68х80 | -10..+50 | 2 | — | 1100 | |
| Mark V620-D8KR01 | 120 | 86х54х23 | -25..+70 | 8 | 820 | ||||
| Antenna V620-H02 | 2000 | 240х190х41 | -25..+70 | — | 5000 | ||||
| Philips | Reader MF RD560 |
13.56 | 100 | 110х67х18 | -10..+70 | 0.1 | 106 | — | 300 |
| Mark S50 MF | 2 | -25..+70 | 8 | 3 |
Note. F – operating frequency; DT – operating temperature range; V – data transfer rate; W – information volume on the tag; D – exchange range.
As can be seen from Table 5, modern RFID systems provide storage, processing and transmission of information at a distance of up to 8 – 10 m, which largely solves the “last inch” problem.
Based on the results of the analysis, Fig. 3 shows the ratio of the considered wireless technologies of the “last inch” in terms of the parameters D (range without retransmission) and V (technical transmission speed).
For comparison, this figure shows a similar ratio for GPRS and UMTS mobile technologies, which, if necessary, can also be used to solve the “last inch” problem.
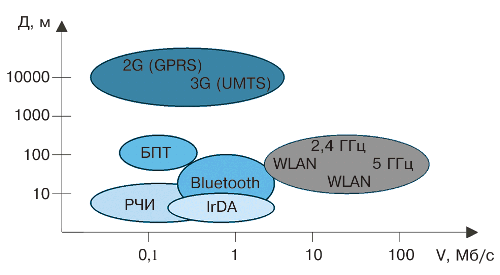
Fig. 3. The “range – speed” ratio of wireless communication technologies
As an example, Fig. 4 shows a block diagram of the possible use of wireless communication technologies in a modern home.
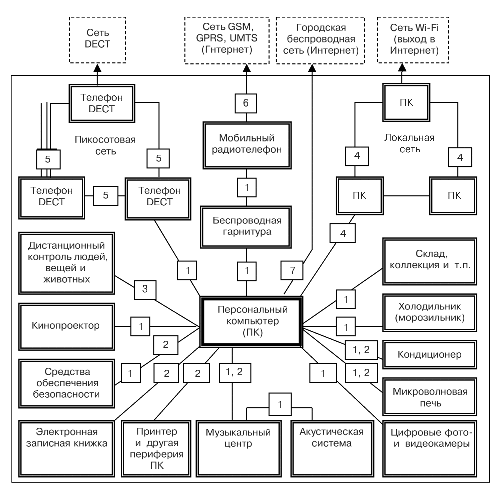
Fig. 4. Block diagram of the possible use of wireless communication technologies in a modern home: 1 – Bluetooth; 2 – IrDA; 3 – RFI; 4 – Wi-Fi; 5 – DECT; 6 – GSM, GPRS, UMTS; 7 – Wi-MAX
To sum it up, we can state that modern capabilities of wireless data transmission technologies provide a solution to a wide range of information security problems, including access control, identification, blocking unauthorized access, hidden mobile communications, etc.
The main thing now is to keep up with the development of technologies, to be able to see in them and use what many do not notice.

Добавить комментарий