Все про видеонаблюдение
Все про умный дом
Все о пожарной безопасности
Сейчас читают
 Как ускорить и смотреть ютуб без тормозов и замедленияЕсли Вы на этой странице, то Вам, скорее всего, […]
Как ускорить и смотреть ютуб без тормозов и замедленияЕсли Вы на этой странице, то Вам, скорее всего, […] 10 лучших прогрессивных языков программирования для разработки мобильных приложенийЗнаете ли вы, что мобильные приложения — это не только […]
10 лучших прогрессивных языков программирования для разработки мобильных приложенийЗнаете ли вы, что мобильные приложения — это не только […] 6 важных особенностей, которые следует учитывать при строительстве нового домаСтроительство нового дома – это уникальная возможность […]
6 важных особенностей, которые следует учитывать при строительстве нового домаСтроительство нового дома – это уникальная возможность […]
Гороскоп на Сегодня
TECHNICAL CHANNELS OF INFORMATION LEAKAGE PROCESSED BY TECHNICAL MEANS..
KHOREV Anatoly Anatolyevich, Doctor of Technical Sciences, Professor
This publication opens a series of articles that make up the journal version of the book by Khorev A.A. “Protection of Information from Leakage through Technical Channels”.
General characteristics of technical channels of information leakage
The current stage of development of society is characterized by the increasing role of the information sphere, which is a set of information, information infrastructure, entities that collect, form, disseminate and use information [2].
Information is usually understood as data about persons, objects, facts, events, phenomena and processes, regardless of the form of their presentation [1].
Protected information refers to information that is the subject of property and is subject to protection in accordance with the requirements of legal documents or requirements established by the owner of the information [1]. This is, as a rule, restricted access information, containing information classified as a state secret, as well as information of a confidential nature.
The set of operations of collecting, accumulating, inputting, outputting, receiving, transmitting, recording, storing, registering, destroying, transforming and displaying information is often referred to by the general term information processing[1].
To technical means of transmitting, processing, storing and displaying restricted access information (TSPI)include [3, 4]: technical means of automated control systems, electronic computers and their individual elements, hereinafter referred to as computer technology (CTE); means of producing and reproducing documents; sound amplification, sound recording, sound reproduction and simultaneous translation equipment; internal television systems; video recording and video reproduction systems; operational command communication systems; internal automatic telephone communication systems, including connecting lines of the above equipment, etc. These technical means and systems are in some cases referred to as main technical means and systems (MTMS) [3].
The set of information processing tools and systems, as well as the premises or objects (buildings, structures, technical means) in which they are installed, constitutes a information processing facility, which in some documents is called an information processing facility[1].
Along with technical means and systems that process restricted access information, auxiliary technical means and systems are also installed at information processing facilities.(VTSS), not directly involved in its processing. These include [3, 4]: systems and means of urban automatic telephone communication; systems and means of data transmission in the radio communication system; systems and means of security and fire alarms; systems and means of notification and signaling; control and measuring equipment; systems and means of air conditioning; systems and means of wire radio broadcasting network and reception of radio and television programs (subscriber loudspeakers, radio broadcasting means; televisions and radio receivers, etc.); electronic office equipment; systems and means of electric clock and other technical means and systems. In some documents, VTSS are called means of providing an informatization object[1].
Power supply of TSPI and VTSS, as a rule, is carried out from distribution devices and power boards, which are connected by special cables to the transformer substation of the city electric grid.
All technical equipment and systems powered by the power grid must be grounded. A typical grounding system includes a common ground electrode, a grounding cable, buses and wires connecting the ground electrode to the technical equipment.
As a rule, wires and cables that are not related to the TSPI and VTSS, as well as metal pipes of heating and water supply systems and other conductive metal structures, which are called extraneous conductors[3], pass through the premises in which technical means for processing restricted access information are installed.
A number of VTSS connecting lines, as well as extraneous conductors, may extend beyond not only the TSPI facility, but also the controlled zone (CZ), which is understood as a space (territory, building, part of a building) in which uncontrolled presence of employees and visitors of the organization, as well as vehicles, is excluded. The boundary of the controlled zone may be the perimeter of the protected territory of the organization, as well as the enclosing structures of the protected building or the protected part of the building, if it is located in an unprotected territory [3, 4].
Thus, when considering a TSPI object as an intelligence object, it must be considered as a system that includes:
— technical means and systems that directly process restricted access information, together with their connecting lines (connecting lines are understood to be a set of wires and cables laid between individual TSPI and their elements);
— auxiliary technical means and systems together with their connecting lines;
— extraneous conductors;
— the power supply system of the facility;
— the grounding system of the facility.
To obtain information processed by technical means, the “enemy” (a person or group of persons interested in obtaining this information) can use a wide arsenal of portable technical intelligence (PTI).
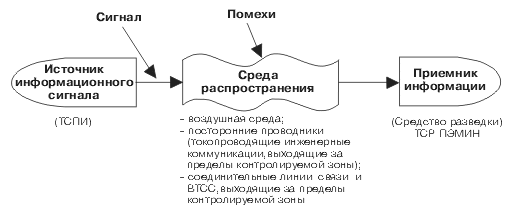
The combination of an intelligence object (in this case, a PTI object), a technical intelligence tool with which information is obtained, and the physical environment in which the information signal is distributed is called a technical information leakage channel(Fig. 1) [4].
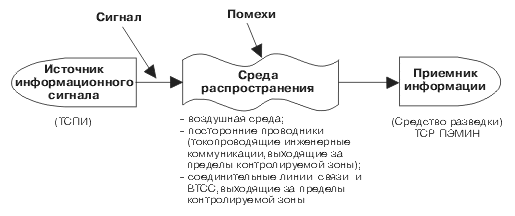
Fig. 1. Scheme of technical information leakage channel
During the operation of technical means, informative electromagnetic radiation occurs, and information signal interference may appear in the connecting lines of the VTSS and extraneous conductors. Therefore, technical information leakage channels can be divided into electromagnetic and electrical.
Electromagnetic information leakage channels
In electromagnetic information leakage channels, the information carrier is various types of side electromagnetic radiation (SER) that arise during the operation of technical equipment, namely [4]:
— side electromagnetic radiation that arises as a result of alternating electric current flowing through the elements of the TSPI and their connecting lines;
— side electromagnetic emissions at operating frequencies of high-frequency generators included in the TSPI;
— side electromagnetic emissions arising as a result of parasitic generation in the TSPI elements.
Side electromagnetic emissions of the TSPI elements.
In some TSPI (for example, sound amplification systems), the information carrier is an electric current, the parameters of which (current strength, voltage, frequency and phase) change according to the law of change of the information speech signal. When electric current flows through the current-carrying elements of the TSPI and their connecting lines, an alternating electric and magnetic field arises in the surrounding space. Due to this, the elements of the TSPI can be considered as emitters of an electromagnetic field modulated according to the law of change of the information signal.
Side electromagnetic radiation at the operating frequencies of high-frequency generators of the TSPI.
The TSPI may include various types of high-frequency generators. Such devices include: master oscillators, clock frequency generators, erasure and magnetization generators of tape recorders, heterodynes of radio and television receivers, generators of measuring instruments, etc.
As a result of external influences of the information signal (for example, electromagnetic oscillations), electrical signals are induced on the elements of high-frequency generators. The receiver of the magnetic field can be the inductance coils of the oscillatory circuits, chokes in the power supply circuits, etc. The receiver of the electric field are the wires of the high-frequency circuits and other elements. Induced electrical signals can cause unintentional modulation of the generators' own high-frequency oscillations, which are radiated into the surrounding space.
Side electromagnetic radiation arising due to parasitic generation in the elements of the TSPI.
Parasitic generation in the elements of the TSPI, including self-excitation of low-frequency amplifiers (e.g. amplifiers of sound reinforcement and sound accompaniment systems, tape recorders, public address systems, etc.), is possible due to random transformations of negative feedback (inductive or capacitive) into parasitic positive feedback, which leads to the amplifier switching from the amplification mode to the self-generation mode of signals. The frequency of self-generation (self-excitation) lies within the operating frequencies of nonlinear amplifier elements (e.g. semiconductor devices, vacuum tubes, etc.). The signal at self-excitation frequencies, as a rule, turns out to be a modulated information signal. Self-excitation is observed mainly when the amplifier is switched to a nonlinear operating mode, i.e. to an overload mode.
Side electromagnetic radiation occurs in the following modes of information processing by means of computing equipment:
— information output to the monitor screen;
— data input from the keyboard;
— information recording to magnetic storage devices;
— information reading from magnetic storage devices;
— data transmission to communication channels;
— data output to peripheral printing devices — printers, plotters;-
data recording from the scanner to magnetic storage media (RAM).
To intercept the secondary electromagnetic emissions of the TSPI, the “enemy” can use both conventional means of radio and radio-technical reconnaissance, and special reconnaissance means, which are called technical means of reconnaissance of secondary electromagnetic emissions and interference (TSR PEMIN). As a rule, it is assumed that the TSR PEMIN are located outside the controlled zone of the facility.
The quality of signal detection by a reconnaissance tool is characterized by the probabilities of correct detection Po of a signal and false alarm Plt. It is usually assumed that reconnaissance equipment uses receivers that are optimal for the types of signals being intercepted. Most often, they implement a signal processing algorithm based on the Neumann-Pearson criterion, which minimizes the probability of a type 2 error (signal omission) provided that the probability of a type 1 error (false alarm) is no greater than a certain specified value. The most common type of interference is the internal noise of the receiver, which is summed up with the received signal (additive noise). Knowing the noise level of the receiver, it is easy to calculate the signal level at the input of the receiver, at which the probability of its correct detection will be equal to a certain permissible (normalized) value Ро.доп, which is usually called the sensitivity of the receiver Урпм.
To ensure the required level of information protection, the acceptable value of the probability of correct signal detection is usually 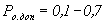 with the probability of a false alarm
with the probability of a false alarm 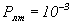 .
.
Using the characteristics of the receiving device and the antenna system of the reconnaissance facility, it is possible to calculate the permissible (standardized) value of the electromagnetic field strength at the location of the reconnaissance facility, at which the ratio “information signal/interference” at the input of the receiving device will be equal to a certain (standardized) value, at which it is still possible either to detect information signals by the reconnaissance facility with the required probability, or to measure their parameters with acceptable errors, and therefore to extract useful information.
The space around the TSPI, within which the electromagnetic field strength exceeds the permissible (standardized) value, is called zone 2 (R2) [3]. In fact, zone R2 is the zone within which interception of TSPI side electromagnetic emissions by reconnaissance means with the required quality is possible (Fig. 2).
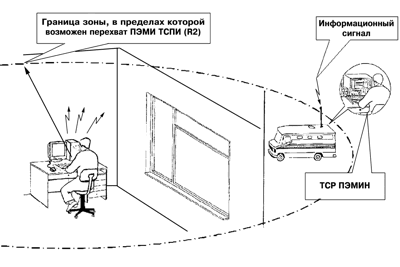
Fig. 2. Interception of TSPI side electromagnetic emissions
by PEMIN reconnaissance means
Zone 2 for each TSPI is determined by the instrumental and calculation method during special studies of technical means on the PEMIN and is indicated in the order for their operation or the certificate of conformity.
Thus, through electromagnetic channels of information leakage, information can be intercepted by receiving and detecting by the reconnaissance means the side electromagnetic radiation arising during the operation of the TSPI.
Along with the passive methods of intercepting information processed by the TSPI, and discussed above, it is also possible to use active methods, in particular, the method of “high-frequency irradiation”(Fig. 3),in which the TSPI is irradiated with a powerful high-frequency harmonic signal (for these purposes, a high-frequency generator with a directional antenna with a narrow radiation pattern is used). When the irradiating electromagnetic field interacts with the TSPI elements, it is re-radiated. On the nonlinear elements of the TSPI, the secondary radiation is modulated by the information signal. The re-radiated signal is received by the receiving device of the reconnaissance vehicle and detected.
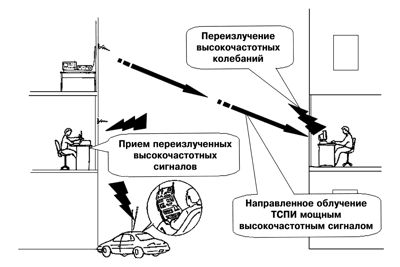
Fig. 3. Interception of information processed by the TSPI,
by the “high-frequency irradiation” method
To intercept information processed by the TSPI, it is also possible to use electronic devices for intercepting information (embedded devices), covertly introduced into technical means and systems (Fig. 4). They are miniature transmitters, the radiation of the master oscillators of which is modulated by an information signal. Information intercepted with the help of eavesdropping devices is either directly transmitted via a radio channel, or first recorded in a special storage device, and then transmitted via a radio channel upon command from a control center.
The most likely installation of eavesdropping devices in foreign-made TSPI.
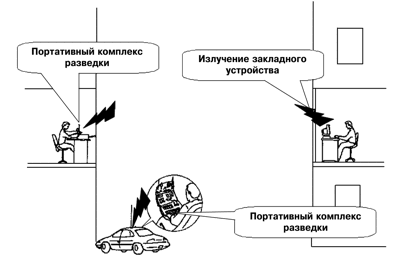
Fig. 4. Interception of information processed by TSPI,
by installing eavesdropping devices in them
Electric information leakage channels
The causes of the occurrence of electrical information leakage channels may be [3, 4]:
— galvanic connections of the TSPI connecting lines with the VTSS lines and extraneous conductors;
— interference of side electromagnetic radiation of the TSPI on the VTSS connecting lines and extraneous conductors;
— interference of side electromagnetic radiation of the TSPI on the power supply and grounding circuits of the TSPI;
— “leakage” of information signals into the power supply and grounding circuits of the TSPI;
— “leakage” of information signals in the grounding circuits of the TSPI.
Interference (currents and voltages) in conductive elements are caused by electromagnetic radiation of the TSPI (including their connecting lines), as well as capacitive and inductive couplings between them. Connecting lines of the VTSS or extraneous conductors are, so to speak, random antennas, to which, when galvanically connected to the PEMIN reconnaissance equipment, it is possible to intercept information signals induced in them (Fig. 5).
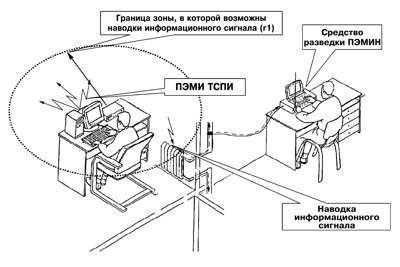
Fig. 5. Interception of induced electromagnetic radiation of the TSPI
from extraneous conductors (utility lines)
Random antennas can be concentrated and distributed [3]. Concentrated Random antennais a compact technical device (for example, a telephone, a loudspeaker of a radio broadcasting network, a fire alarm sensor, etc.) connected to a line extending beyond the controlled area. To distributed random antennasinclude random antennas with distributed parameters: cables, wires, metal pipes and other conductive communications that extend beyond the controlled zone. The level of signals induced in them largely depends not only on the power of the emitted signals, but also on the distance from the TSPI lines to the VTSS lines or extraneous conductors, as well as the length of their joint path.
When propagating through a random antenna, the induced information signal attenuates. The attenuation coefficient of the information signal can be calculated knowing the distance from the place of possible connection of the TCP to the random antenna to the TSPI object and the frequency of the side electromagnetic emissions. With a known attenuation coefficient, it is easy to calculate the value of the induced information signal in a random antenna, at which the level of the information signal at the input of the receiving device of the reconnaissance facility will be equal to a certain threshold (normalized) value, at which the probability of its correct detection will be equal to the required value Ро.доп.
The space around the TSPI, within which the level of the induced information signal from the TSPI in concentrated antennas exceeds the permissible (normalized) value is called zone 1(r1), and in distributed antennas – zone 1* (r1*)[3].
Unlike zone R2, the size of zone r1 (r1*) depends not only on the level of side electromagnetic radiation of the TSPI, but also on the length of the random antenna (from the room in which the TSPI is installed to the place where a reconnaissance device can be connected to it).
Zones r1 (r1*) for each TSPI are determined by the instrumental-calculation method during special studies of technical means on PEMIN and are indicated in the order for their operation or certificate of conformity.
“Leakage” of information signals into the power supply circuits is possible in the presence of internal parasitic capacitive and (or) inductive couplings of the rectifier device of the TSPI power supply unit. For example, in a low-frequency amplifier, the currents of the amplified signals are closed through the power supply, creating a voltage drop on its internal resistance, which, if there is insufficient attenuation in the filter of the rectifier device, can be detected in the power supply line in the presence of a magnetic coupling between the output transformer of the amplifier and the transformer of the rectifier device. In addition, the average value of the consumed current in the final stages of the amplifiers depends to a greater or lesser extent on the amplitude of the information signal, which creates an uneven load on the rectifier and leads to a change in the consumed current according to the law of change in the information signal.
“Leakage” of information signals in grounding circuits. In addition to grounding conductors used for direct connection of the TSPI to the grounding circuit, various conductors extending beyond the controlled area may have a galvanic connection to the ground. These include the neutral wire of the power supply network, screens (metal sheaths) of connecting cables, metal pipes of heating and water supply systems, metal reinforcement of reinforced concrete structures, etc. All these conductors, together with the grounding device, form a branched grounding system to which information signals can be induced. In addition, an electromagnetic field arises in the soil around the grounding device, which is also a source of information.
Interception of information signals in power lines and grounding circuits of the TSPI is possible with a galvanic connection of the PEMIN reconnaissance tool to them (Fig. 6).
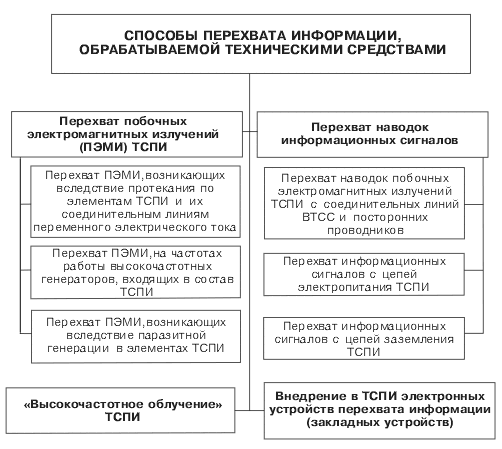
Fig. 6. Interception of information signals from power supply and grounding circuits of the TSPI
Thus, the interception of information processed by technical means can be carried out by (Fig. 7):
— interception of side electromagnetic radiation arising during the operation of technical means;
— interception of information signal interference from the connecting lines of the high-voltage telecommunications network and extraneous conductors;
— interception of information signals from the power supply and grounding lines of the high-voltage telecommunications network;
— “high-frequency irradiation” of the high-voltage telecommunications network;
— introduction of bugs into the high-voltage telecommunications network.Fig. 7. Classification of methods for intercepting information processed by technical means
Literature
1. GOST R 51275-99. Information security. Informatization object. Factors affecting information. General provisions. (Adopted and put into effect by the Resolution of the State Standard of Russia dated May 12, 1999, No. 160).
2. The Doctrine of Information Security of the Russian Federation (Adopted on September 9, 2000, No. PR-1895).
3. Terminology in the Field of Information Security: Handbook. Moscow: VNII Standard, 1993. 110 p.
4. Khorev A.A. Information Protection from Leakage through Technical Channels. Part 1. Technical Channels of Information Leakage. Moscow: State Technical Commission of the Russian Federation, 1998. 320 p.






Добавить комментарий