PROTECTION AGAINST UNAUTHORIZED ACCESS. PASSWORD SYSTEM.
MASYUK Mikhail Igorevich
PROTECTION AGAINST UNAUTHORIZED ACCESS. PASSWORD SYSTEM
The password system as an integral part of the access control subsystem of the information security system (ISS) is part of the “front line of defense” of the entire security system. Therefore, the password system becomes one of the first objects of attack when an intruder intrudes into a protected system.
The access control subsystem of the ISS affects the following concepts:
Access identifier is a unique attribute of the subject or object of access.
Identification is the assignment of an identifier to subjects and objects of access and (or) comparison of the presented identifier with the list of assigned identifiers.
Password is the identifier of the access subject, which is its (the subject's) secret.
Authentication – verification of the access subject’s ownership of the identifier presented by him; confirmation of authenticity.
You can also find the following interpretations of the terms user identifier and password [1]:
An identifier is a unique amount of information that allows for distinguishing individual users of a password system (to identify them). An identifier is often also called a user name or user account name.
A password is a secret amount of information known only to the user and the password system, presented to pass the authentication procedure.
An account is a combination of a user identifier and password.
One of the most important components of a password system is the account database (security system database). The following options for storing passwords in the system are possible:
- in the open;
- in the form of hash values (hash (English) – mixture, hodgepodge);
- encrypted with a certain key.
The second and third methods are of the greatest interest, as they have a number of features.
Hashing does not provide protection against dictionary attacks if the database is obtained by an intruder. When choosing a hashing algorithm to be used to calculate password hash values, it is necessary to ensure that the hash values obtained from different user passwords do not match. In addition, a mechanism should be provided to ensure the uniqueness of the hash values if two users choose the same password. To achieve this, a certain amount of “random” information is usually used when calculating each hash value, for example, information generated by a pseudo-random number generator.
When encrypting passwords, the method of generating and storing the encryption key for the account database is of particular importance. The following options are possible:
- the key is generated programmatically and stored in the system, allowing it to be rebooted automatically;
- the key is generated programmatically and stored on an external drive, from which it is read at each startup;
- the key is generated based on a password selected by the administrator, which is entered into the system at each startup.
The most secure storage of passwords is provided by hashing them and then encrypting the resulting hash values, i.e. by combining the second and third methods of storing passwords in the system.
How can a password fall into the hands of an intruder? The following cases seem most likely:
- the password you wrote down was found by an intruder;
- the password was spied on by an intruder when entered by a legitimate user;
- the intruder gained access to the security system database.
The measures to counteract the first two dangers are obvious.
In the latter case, the attacker will need specialized software, since records in such a file are rarely stored in clear text. The strength of a password system is determined by its ability to withstand an attack by an attacker who has taken possession of the account database and is trying to recover passwords, and depends on the speed of the “fastest possible” implementation of the hashing algorithm used. Password recovery involves calculating hash values for possible passwords and comparing them with the existing password hash values, followed by their presentation in clear form, taking into account the case.
A password can be recovered from the account database in various ways: a dictionary attack, a sequential (complete) search, and a hybrid of a dictionary attack and a sequential search.
In a dictionary attack, the hash values for each dictionary word or dictionary word modification are sequentially calculated and compared with the hash values of each user's password. If the hash values match, the password is found. The advantage of this method is its high speed. The disadvantage is that only very simple passwords that are in the dictionary or are dictionary word modifications can be found in this way. The success of this attack directly depends on the quality and volume of the dictionary used (it is easy to find such ready-made dictionaries on the Internet).
Brute force uses a set of characters and calculates a hash value for each possible password made up of those characters. Using this method, a password will always be determined if the characters that make it up are in the selected set. The only drawback of this method is the large amount of time it may take to determine the password. The more characters (letters of different upper and lower case, numbers, special characters) the selected set contains, the more time it may take to complete the brute force attack.
When recovering passwords using a hybrid of a dictionary attack and brute force, characters are added to the right and/or left of each word or modification of a dictionary word (123parol). In addition, the following may be checked for use: usernames as passwords; repetition of words (dogdog); reverse order of word characters (elpoep); transliteration of letters (parol); replacement of Cyrillic letters with Latin layout (gfhjkm).
For each resulting combination, a hash value is calculated, which is compared with the hash values of the passwords of each user.
What password can be definitely called weak in all respects (except for memorability)? A typical example: a password of a small number (up to 5) of symbols/digits. According to some data, out of 967 passwords of one of the hacked Internet mail servers, 335 (almost a third) consisted exclusively of numbers. The number of passwords including letters and numbers was 20. The remaining passwords consisted of letters, mostly in lower case, with rare exceptions (in the amount of 2 passwords) including special characters (“*”, “_”). The “_” symbol, however, was often found in usernames. In 33 cases, the username and password were the same. The most popular password was 123 (it was found 35 times, almost every 27th password). In second place was the password qwerty (20 passwords). How convenient it is to type, isn’t it? Next come: 666 (18 times), 12 (17 times), xakep (14 times) and 1, 11111111, 9128 (10 times each). 16 passwords consisted of one symbol/digit.
In everyday life, a modern person has to remember a considerable amount of information: PIN codes for a bank card and mobile phone, combinations of code locks, passwords for accessing the Internet, various resources, and email accounts. Do you need to remember all passwords? It all depends on the assessment of the level of losses as a result of your password falling into the wrong hands. No one prevents you from writing down passwords for accessing the Internet and network resources in a notebook if you are not afraid that someone will log into the network without your knowledge and get acquainted with the contents of your email account. This conclusion, however, does not apply to passwords used in the workplace. Gaining access to a local network on your behalf may, for certain reasons, be a tempting option. It is also not prohibited to write down the PIN code for a bank card on paper, the main condition in this case is to store the card and the code combination written down without explanation separately.
The requirements for a password are increased due to its importance. An example of an “important password” is a password used for work in automated systems that process restricted access information (state secrets, confidential information). The guidelines of the State Technical Commission of Russia do not provide specific recommendations on choosing a password or calculating its strength, with the exception of the length, which is from 6 (class 3B, 3A, 2B, 2A) to 8 (class 1B, 1A) alphanumeric characters and the need to change the password periodically.
There are methods for quantitatively assessing the strength of password systems [2]:
(Anderson formula), where
k is the number of password guessing attempts per minute;
M is the password validity period in months;
P – probability of password selection;
A1 – power of password space (A – power of password alphabet, l – password length).
Thus, the greatest influence on the probability of password disclosure is exerted by the value l. Other components of this formula extremely rarely have an influence on the value P exceeding one order of magnitude. Increasing the password length by just one character significantly increases the time required for an attacker to disclose it.
Parameters P, V, T and A1 are related to each other by the following relationship [1]:
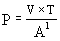 , where
, where
P is the probability of password selection during its validity period (the selection is carried out continuously during the entire validity period of the password);
V is the speed of password selection (the speed of processing one registration attempt by the verifying party or the speed of calculating the hash value of one trial password);
T – password expiration date (specifies the period of time after which the password must be changed);
A1 – password space capacity (A – password alphabet capacity, l – password length).
In the case where the exact length of the password being searched for is unknown, the maximum password guessing time (Tmax) will be calculated according to the following formula [3]:
| Tmax | 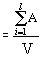 |
A thorough knowledge of the methods of storing user accounts in the security system database allows optimizing password recovery (breaking) programs. Detailed knowledge of the organization of the password system of Windows NT/2000/XP operating systems allows the authors of the specified programs to declare the speed of execution of the enumeration from 3.9 million passwords/sec. to 5.4 million passwords/sec. on a PC with an Athlon XP 1700+ processor or to talk about the possibility of finding all alphanumeric passwords in three days on a PC with a Pentium II/450 processor.
According to Kompyulenta (http://compulenta.ru/2003/7/24/40961/), Swiss researcher Philipp Jochslin manages to crack Windows alphanumeric passwords in an average of 13.6 seconds. A computer based on an Athlon XP 2500+ processor with 1.5 GB of RAM was used for the cracking. The table in which the password variants were stored occupied 1.4 GB and was completely loaded into the computer's RAM, which allowed the cracking speed to be significantly increased. With a table size of 20 GB and the presence of letters, numbers and 16 special characters in the password, the password is cracked in an average of 30 seconds.
So, what kind of password can resist attempts to pick it? A long one, consisting of letters of different registers, numbers and special characters. At the same time, it must be random, i.e. the choice of characters is made arbitrarily (without any system) and not used anywhere else, while the only place where the password is recorded should be the head of a single person. However, it is also necessary to consider the issues of practical use of the password. A very long password is difficult to remember, especially considering the fact that the user has to have more than one password. It is also not possible to quickly enter a long password. Randomly selected characters will be remembered if their pronunciation out loud has a memorable sound form (euphony) or they have a characteristic location on the keyboard, otherwise you cannot do without a cheat sheet.
Password generation programs can help the user create a password according to certain criteria.
One such program is Advanced Password Generatorallows you to create passwords using a random number generator or a user-defined keyword, and also contains an algorithm for creating words that are closest to the natural language (Russian or English). When using this mode, you get “memorable” but meaningless words. The term “memorable” should be understood as the euphony of the resulting combination. In this mode, the use of numbers, special characters, or mixed case letters is automatically disabled.
Here are some “rememberable” passwords created by the program: ELASWOWA, DEDRYTON, BENEROMO, SARMANED. The program allows you to create a password from 4 to 32 characters long. A “rememberable” password of 32 characters looks like this: NONEERESSPYOVENAPARDERETOURVENFF.
According to the author, the password DV24*KK4 can also be classified as “rememberable”, despite the presence of numbers and a special character.
The uniqueness of a password generated by such programs directly depends on the degree of “randomness” of the generator used for these purposes.
Modern information security systems limit the possible length of the password to 12-16 characters. Most often, these are Latin letters, numbers, and special characters.
Most information security systems have the following capabilities to increase the effectiveness of the password system:
- setting a minimum password length;
- setting a maximum password validity period;
- setting a requirement for passwords to be unique (prevents the password from being replaced after its expiration with one of the previously used ones);
- limiting the number of password entry attempts (blocks the user after exceeding a certain number of consecutive entry attempts; does not affect the administrator account).
In order to complicate the task of an intruder in obtaining the security system database, many information security systems store it in the non-volatile memory of their hardware.
Some NSD information protection systems contain built-in mechanisms for generating passwords and communicating them to users. An obvious disadvantage and the main factor that pushes the user to write down a password is the impossibility of remembering a gibberish of, for example, 8 alphanumeric characters that are not related to each other.
If the user needs to generate a password on their own, the following can be distinguished as criteria for choosing a password:
- using letters of different registers;
- using numbers and special characters together with letters.
When creating a password, it is not recommended to use:
- your registration name in any form (as is, inverted, in capital letters, doubled, etc.);
- your first name, last name, or patronymic in any form;
- names of close relatives;
- information about yourself that can be easily obtained. This includes phone numbers, personal account numbers, your car number, the name of the street where you live, etc.;
- a password of only numbers or only letters;
- a word that can be found in dictionaries.
You need to remember (try not to write down) your password. If remembering a quality password turned out to be an impossible task for you, do not write down the password in its entirety, divide it into two parts and write them down in different places. Just do not equip these entries with comments like: “This is the first part of my password for accessing the Internet, the second part is on the next page.” If you made up a password based on a phrase, then, for example, an entry like: Everybody*love(the)freedom will remind you that your password is: e*v(e)e (we took every third letter with the addition of special characters). A more secretive method involves supplementing what was written according to a principle defined by the user. In this case, the found entry: DeReVo will not automatically reveal the actual password: *DterReeeV*o.
And yet, the password used to work with restricted access information must be remembered and not written down anywhere.
It is necessary to practice entering a password so that this procedure takes as little time as possible. Although it is desirable to be able to enter a password without looking at the keyboard, at first, connect your visual memory. The main rule: no one except you should know your password.
Here are several options for selecting elements that make up a password:
- choose a line or two from a song or poem and use the first letter of each word, add numbers (special characters);
- choose a famous saying (proverb, slogan, etc.) and use every fourth letter, add numbers (special characters);
- replace one consonant and one or two vowels in a word, add numbers (special characters);
- choose two short words and connect them together with a punctuation mark between them, add numbers (special characters).
In conclusion, it is necessary to note the existence of the “human factor paradox”. It consists in the fact that the user often tends to act rather as an opponent of the password system, as, indeed, of any security system, the functioning of which affects his working conditions, than as an ally of the security system, thereby weakening it. Indeed, the need to enter a password every time you log into the system, not to mention the need to remember a complex character sequence, is not convenient. The only measure to counter this circumstance is to develop a competent approach to information security issues in users.
Literature
1. Theoretical Foundations of Computer Security: Textbook for Universities/P.N. Devyanin, O.O. Mikhalsky, D.I. Pravikov et al. Moscow: Radio and Communications, 2000. 192 p.: ill.
2. Hoffman L. Modern Methods of Information Security: Trans. from English/Ed. V.A. Gerasimenko. M.: Soviet Radio, 1980. 264 p. ill.
3. Emelyanov R. How do OSs store their passwords? //BYTE. 1999. No. 1 (5).

Добавить комментарий