#unauthorized access, #NSD
NSD: THEORY AND PRACTICE.
MASYUK Mikhail Igorevich
Terminology
When setting the task of information security, it is necessary to take into account the implementation of a whole range of measures.
The components of this complex are protection against unauthorized access (UAA), against leakage via technical channels, against possibly introduced special electronic devices and virus programs.
UAA can be implemented by a person or a program initiated by him in relation to the protected information, as well as by a person in relation to the equipment and channels for transmitting the protected information.
A number of guidelines (RD) of the State Technical Commission of Russia are devoted to the requirements for protection against UAA for information.
The protection of equipment and channels for transmitting protected information is provided for in these RDs indirectly, by introducing requirements for their physical protection.
In accordance with the RD “Protection from unauthorized access to information.
Terms and definitions of unauthorized access to information – access to information that violates the rules for access control using standard means provided by computer technology or automated systems.
Standard means are understood as a set of software, firmware and hardware support for computing equipment or automated systems.
Despite this, the action of an embedded software bookmark (“worm”, etc.), which resulted in the protected information getting into the hands of an intruder, can also be considered as an act of unauthorized access. Any other actions of malicious programs fall under the definition of unauthorized impact on information.
In a broad sense, protection of information from unauthorized access is an activity aimed at preventing an interested party from obtaining protected information in violation of the rights or rules of access to protected information established by legal documents or by the owner, holder of the information.
The interested party implementing the NSD to the protected information may be: the state, a legal entity, a group of individuals, including a public organization, an individual. (GOST R 50922-96 Information protection. Basic terms and definitions.).
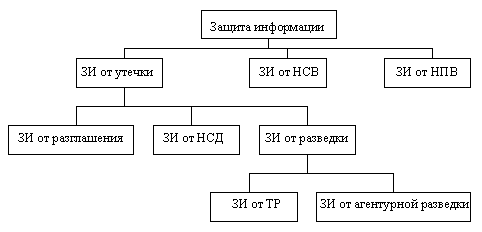
The place of information protection (IP) from NSD within the framework of information protection is shown in the diagram (Fig. 1).
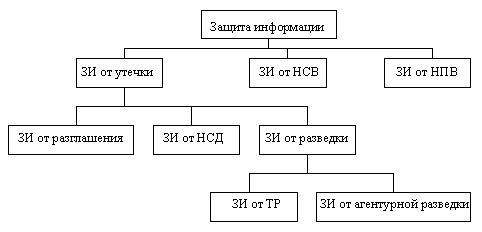
Fig. 1. UI – unauthorized impact;
UII – unintentional impact;
TR – technical intelligence.
In the definition of unauthorized access to information given in the RD “Protection from unauthorized access to information. Terms and definitions”, two concepts no less interesting than the term unauthorized access appear: computer equipment (CET) and automated systems (AS).
These concepts are necessary to represent the environment for implementing unauthorized access.
The division into CET and AS is provided for in the RD “Concept of protection of CET and AS from unauthorized access to information”.
The difference between the two directions is caused by the fact that the SVT are developed and supplied to the market only as elements from which functionally oriented AS are subsequently built, and therefore, without solving applied problems, the SVT do not contain user information.
In addition to user information, when creating an AS, such characteristics of the AS as user authority, intruder model, and information processing technology appear that are absent when developing the SVT.
An example of a data processing system is usually an expansion board with the appropriate hardware and software that implements the user authentication function (for example, using Touch memory).
RD «Data processing system. Protection against unauthorized access to information. Indicators of protection against unauthorized access» provides the term data processing system according to GOST R 50739-95 «Data processing system. Protection against unauthorized access to information. General technical requirements» as a set of software and technical elements of data processing systems that can function independently or as part of other systems.
Despite the fact that the computer technology is a set of software and technical elements, operating systems and specialized programs are also classified as computer technology.
According to GOST 34.003-90 “Information technology. Set of standards for automated systems. Automated systems. Terms and definitions”, automated systems are understood as a system consisting of personnel and a set of automation tools for their activities, implementing information technology for performing established functions.
Depending on the type of activity, the following types of AS are distinguished: automated control systems (ACS), computer-aided design systems (CAD), etc.
One of the main components of an AS is an automated workstation (AWP) — a software and hardware complex of an AS designed to automate a certain type of activity, which is very similar to the definition of a computer system given above. In the simplest case, an AWP is represented as a personal computer and a user working on it.
Thus, a personal computer with installed software is formally a computer system until you put it into operation by installing it in a specific room and assigning a user to it.
Even if the user is the only one allowed to access all the information placed on a medium of one level of confidentiality, and uses the personal computer exclusively to create text documents in a single text editor, this is an AS in the form of an automated workplace (in this case, class 3B or 3A).
Unauthorized access: attack and defense
The main methods of unauthorized access include:
- direct access to access objects;
- creation of software and hardware that access access objects bypassing security measures;
- modification of security measures that allow unauthorized access;
- introduction of software or hardware mechanisms into the technical means of the computer equipment or automated systems that disrupt the intended structure and functions of the computer equipment or automated systems and allow unauthorized access.
Protection of information from unauthorized access is an integral part of the general problem of ensuring information security.
Measures to protect information from unauthorized access should be carried out in conjunction with measures to specially protect the main and auxiliary means of computer technology, communication systems and equipment from technical means of industrial espionage intelligence.
Some of the main principles of protection from unauthorized access are:
- ensuring the protection of the computer equipment with a set of software and hardware tools;
- ensuring the protection of the AS with a set of software and hardware tools and organizational measures supporting them.
Security from unauthorized access to information during its processing by the computer equipment is characterized by the fact that only duly authorized persons or processes initiated by them will have access to reading, writing, creating or destroying information.
Organizational measures within the framework of the system of protection of information from unauthorized access (SZI UAC) in the AS, processing or storing information that is the property of the state and classified as secret, must meet state requirements for ensuring the secrecy of the work carried out.
When processing or storing information in the AS that is not classified as secret, within the framework of the NSD SZI, state, collective, private and joint enterprises, as well as individuals, are recommended to implement the following organizational measures:
- identification of confidential information and its documentary registration in the form of a list of information subject to protection;
- determination of the procedure for establishing the level of authority of the access subject, as well as the circle of persons to whom this right is granted;
- establishment and registration of rules for access control, i.e. a set of rules governing the rights of access of subjects to objects;
- familiarization of the access subject with the list of protected information and his level of authority, as well as with the organizational, administrative and working documentation defining the requirements and procedure for processing confidential information;
- receiving from the access subject a receipt for non-disclosure of the confidential information entrusted to him;
- ensuring the security of the facility where the protected AS is located (territory, buildings, premises, storage facilities for information carriers) by establishing appropriate posts, technical security equipment or any other means that prevent or significantly complicate the theft of computer equipment, information carriers, as well as unauthorized access control devices for computer equipment and communication lines;
- selecting the AS security class in accordance with the specifics of information processing (processing technology, specific operating conditions of the AS) and its level of confidentiality;
- organization of the information security service (responsible persons, the AS administrator), which carries out the accounting, storage and issuance of information carriers, passwords, keys, maintenance of service information of the NSD ISS (generation of passwords, keys, support of access control rules), acceptance of new software included in the AS, as well as control over the progress of the technological process of processing confidential information, etc.;
- development of the NSD ISS, including the relevant organizational, administrative and operational documentation;
- acceptance of the NSD ISS as part of the AS.
An intruder is considered to be a subject who has access to work with the standard means of the AS and SVT as part of the AS.
Intruders are classified by the level of capabilities provided to them by the standard means of the AS and SVT. The RD «Concept of protection of SVT and AS from unauthorized access to information» identifies 4 levels of intruder capabilities: from the first — the lowest, to the fourth — the highest.
At his level, the intruder is a highly qualified specialist, knows everything about the AS and, in particular, about the system and its protection means. Unfortunately, none of the available RDs explicitly describe the threats to information that intruders pose.
On means of protection against unauthorized access
The purpose of this article is not to review and compare the existing means of protection against unauthorized access (hereinafter, means of protection).
Descriptions of such means are often found in the specialized press. However, the author of the article wants to draw attention to some aspects of the choice of means.
The choice is always a difficult task. It is important to take into account many things: from the availability of certificates to the features of using a specific product.
In Russia, in relation to SVT, and the means of protection relates to SVT, the concept of “certification according to safety requirements” is used.
Compliance with the safety requirements of the AS is confirmed by the Certificate of Conformity. Processing of information constituting a state secret is permitted only with the use of certified means and protection systems.
The State Technical Commission Certificate for a protection means is usually issued for a period of 3 years. Sometimes in the text of the certificate you can find an explicit indication of what information can be protected using this means.
For example, a security tool may not be intended to protect information constituting a state secret. A certificate does not always certify the class of a security tool in accordance with the RD “SVT. Protection from unauthorized access to information. Indicators of protection from unauthorized access” (hereinafter RD SVT).
You can find an indication of the possibility of using this tool when creating an AS that meets the requirements of the RD “AS. Protection from unauthorized access to information. Classification of AS and requirements for information protection” (hereinafter RD AS) for a certain security class (for example, 1D).
In this case, the product probably has the capabilities that are used in the creation of the AS, but some functions required for certification according to RD SVT are missing.
Sometimes compliance with a certain class according to RD SVT is guaranteed with a clause of the following type: “subject to compliance with the restrictions specified in the technical conditions”. Unfortunately, familiarization with the technical conditions in accordance with which the product is developed and manufactured is not always a trivial task.
Returning to the issue of PCs as computer equipment, it should be noted that there are PCs that have a State Technical Commission certificate for “technical means of information processing, implemented in a protected design” according to the standards for protection against leakage due to PEMIN. Certification of PCs according to the requirements of RD computer equipment is not carried out.
A specific PC, as a component of an AS, receives confirmation of compliance with the safety requirements as a result of the certification procedure, mandatory for AS intended for processing information constituting a state secret.
During certification, we are talking about a specific sample intended for use in specific conditions with a given specific location relative to other technical means directly at the place of operation (certification is subject to a typical sample of the product without reference to the place of operation).
Many manufacturers of protective equipment provide demo versions of software free of charge.
They can be found on the Internet on manufacturers' websites or resources dedicated to information security. Do not neglect the opportunity to «feel», even a slightly cut-down version of the product that you plan to use.
If the product has similar characteristics, it is not a bad idea to compare them. In this case, the operating features and availability of the necessary functions, not to mention ease of use (if this term is generally applicable to information security tools), will not come as a surprise to users when putting them into operation.
It should be noted that the fulfillment of some requirements by the protection means can be difficult to verify in practice.
The RD AS contains a requirement to clear the released areas of the computer's RAM and external storage devices for classes 3A, 2A, 1G-1A by double random writing to the released area of memory previously used to store protected data (files).
For computer systems, this requirement sounds differently for different security classes:
- preventing the subject's access to residual information during the initial assignment or during the redistribution of external memory (for security class 5);
- hindering the subject's access to residual information during the initial assignment or during the redistribution of external memory; during the redistribution of RAM, it must be cleared (for security class 4);
- clearing RAM and external memory by writing masking information to memory when it is freed (reallocated) (for security classes 3, 2 and 1).
You must admit that checking the ability of a security system to erase RAM, not to mention how many times this procedure has been performed, is not an easy task.
It should be mentioned that there is another document of the State Technical Commission, according to which certification is carried out for the absence of undeclared capabilities in software intended to protect restricted information — this is the RD «Protection from undeclared information. Part 1.
Software for information security. Classification by the level of control over the absence of undeclared capabilities.» This document establishes four levels of control over the absence of undeclared capabilities.
Each level is characterized by a certain minimum set of requirements.
The highest level of control is the first, which is sufficient for software used to protect information classified as “special importance”.
The second level of control is sufficient for software used to protect information classified as “top secret”.
The third level of control is sufficient for software used to protect information classified as “secret”. The lowest level of control is the fourth, sufficient for software used to protect confidential information.
Undeclared capabilities are software functionality that is not described or does not correspond to that described in the documentation, the use of which may violate the confidentiality, availability or integrity of the information being processed.
The implementation of undeclared capabilities, in particular, are software bookmarks.
However, the presence of certificates is currently a mandatory requirement only when processing information constituting a state secret, so the choice is yours!

Добавить комментарий