UKOV Vyacheslav Sergeevich,
Candidate of Technical Sciences
INTEGRAL INFORMATION PROTECTION Continued. Beginning in No. 5, 2002.
Means of detecting hidden bookmarks. Nonlinear locators
One of the most dynamic sectors of the Russian market for comprehensive information protection is the sector of hidden bug detection tools.
Moreover, at present, the task of detecting information leakage channels is solved using radio monitoring and nonlinear location tools.
The most extensive group consists of technical tools used to detect radio, video and telephone bugs.
To detect workingradio bugs most often use radio monitoring devices based on scanning radio receivers (scanners).
To detect any non-working electronic devices, the most effective method is to use non-linear radars.
The operating principle of such devices is based on the fact that when irradiating electronic devices containing non-linear elements such as diodes, transistors, etc., the signal is reflected at higher multiple harmonics.
The reflected signals are registered by the locator regardless of the operating mode of the electronic device (on-off).
The main comparative characteristics of nonlinear locators available on the Russian market today are given in Table 5.
Table 5. Main comparative characteristics of nonlinear radars
The analysis shows that the technical characteristics of domestic developments of non-linear locators are at the level of world models, and their prices are significantly lower than foreign ones.
Currently, non-linear locators in Russia are actively being improved and are widely used.
Mobile phone blockers
The rapid development of mobile telephony technologies has given rise to a number of problems.
In the field of information security, in particular, protection of information from unauthorized access, completely new tasks have emerged to determine the operation of a cell phone in a protected area and block its operation in order to prevent unauthorized transmission of information that may be confidential.
This concerns both private business and government agencies, since a cell phone is potentially a ready-made eavesdropping device that transmits information in a traffic channel of the corresponding standard.
In addition, the widespread use of mobile phones has given rise to a number of problems of both an ethical and legal nature concerning various aspects of their use in public places.
All of this has stimulated the emergence and development of a new sector of the information security market – mobile phone blockers, the features of which are presented in Table 6.
Table 6. Mobile phone blockers
As can be seen from the table, almost all blockers presented today on the Russian market use a common principle: determining the fact that a mobile phone is working and turning on a generator of barrage interference.
However, among them there is already an intelligent blocker “RS jammer”, which minimizes the harmful effects of interference generators on human health. In case of detection of a working or simply connected to the network mobile phone, it determines the number of the occupied frequency channel and the time slot allocated to this phone.
When a subscriber attempts to access the network (outgoing call) or when responding to a base station request (incoming call), the blocker emits a suppression signal and blocks the connection within a short time.
Currently, mobile phone blockers are necessary for:
- government agencies and departments;
- law enforcement agencies;
- enterprises working with state secrets;
- conference halls and meeting rooms;
- churches and auditoriums;
- theater and concert halls, etc.
Considering the dynamics of development and the relevance of the tasks being solved, the sector under consideration is very promising in the information security market.
Computer polygraphs
Statistics of modern information leakage channels show that almost 50% of “leaked information is somehow related to personnel.
The development of electronic computing technology has led to the emergence of computer polygraphs (CP), which have great potential for blocking information leakage through personnel and employees of companies.
Digital processing, storage and transmission of signals have significantly expanded not only service capabilities, but also made it possible to create new classes of technical means, including remote and contactless polygraphs.
Modern technologies make it possible to create new computer polygraphs with high operational and technical characteristics. In this area, such domestic companies as EPOS, Geolid, Inex, Grotek and others have achieved good results at present.
Analysis of the Russian computer polygraph market shows that at present domestic developments of PCs are not inferior to foreign ones in terms of key indicators, and in some (especially cost indicators) have better characteristics (Table 7).
Table 7. Comparative characteristics of computer polygraphs
Means of protection against destructive force effects
At present, due to the current circumstances (terrorism, crime, etc.), special importance is attached to means of protection against destructive force effects (SDF).
These means are essentially electromagnetic weapons, which are capable of remotely and silently striking virtually any security system.
The main thing is to ensure the appropriate power of the electromagnetic pulse.
The secrecy of the attack is significantly increased by the fact that the analysis of damage to the destroyed equipment does not allow for the unambiguous identification of the cause of the damage, since the cause may be either intentional (attack) or unintentional (for example, induction from lightning) force impact.
This circumstance allows the attacker to successfully use technical means of force destructive impact (TMFDI) repeatedly.
It has now been established that a computer or any other electronic equipment of the security system, taking into account the environment of energy transmission, can be subjected to degradation by SDV through three main channels of destructive force impact (CFDI): through the power supply network, through wired channels and through the air.
Expert forecasts show that the probability of using SDV is growing year by year.
Therefore, when developing a security concept, it is necessary to take into account the possibility of a SDV, for which, first of all, it is necessary to classify the SDV TS.
However, given the specific purpose of these means and the reluctance of the companies producing them to widely advertise their work, the classification task turned out to be non-trivial.
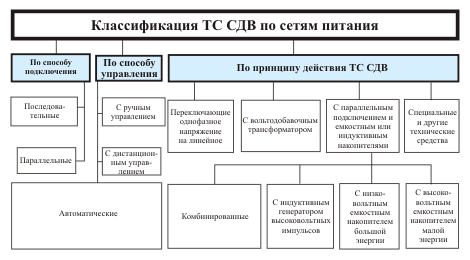
A possible classification of modern SDV TS is shown in Fig. 7 — 9.
Fig. 7. Classification of SDV TS by power supply networks
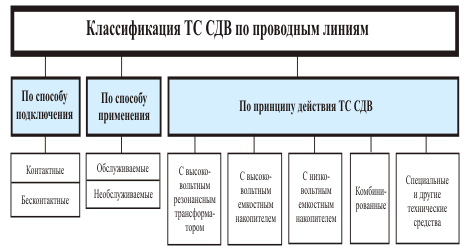
Fig. 8. Classification of VLF TS by wire lines
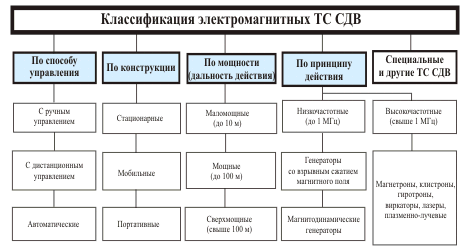
Fig. 9. Classification of VLF TS by ether (electromagnetic VLF TS)
The analysis shows that at present the main channel of destructive force impact continues to be the power grid.
Taking this into account, Table 8 presents the main characteristics and features of complex technical means of protection (TMP) against destructive force impacts along power supply chains, presented today on the Russian market.
Table 8. Main characteristics and features of complex TMP against destructive force impacts along power supply chains
Security services
An analysis of the modern Russian market of technical means and services for ensuring security shows that at present there are already more than 2,000 enterprises and firms actively providing their services and supplying special technical means for ensuring security, the range of which already comprises tens of thousands of items.
The commercial market of information security tools is currently formed by such companies as “Information Security”, CBI “Maskom”, “Informzashita”, “ANNA”, “Confident”, Laboratory No. 11”, “Nelk”, “NOVO”, “SET-1”, ELVIRA”, “Ankort”, “Ankad”, “IKMC-1”, “Surtel”, “IRKOS”, “Radioservice”, “Progresstech”, “ENSANOS” and others.
The previous development of the modern Russian market has caused serious changes in the policies of companies supplying technical means and services for ensuring security.
Serious competition that has emerged in recent years has forced many companies to pay more attention to quality issues, extend warranty periods, introduce an additional system of discounts, offer customers comprehensive services, starting with consultations, delivery of technical equipment, inspection of protected premises and ending with maintenance (prevention and repair).
Currently, three main approaches are used to solve information security problems: individual approach with a consistent solution of specific security problems, comprehensive approach with a simultaneous solution of a set of problems aimed at achieving a single goal, and integratedapproach – solving security problems using common (unified) technical means and software based on the principles of integrated security.
As a rule, in previous years, an individual approach was used (for example, it was necessary to ensure the security of telephone communications — a device for closing telephone conversations was purchased). This approach is still the main one on the modern Russian market.
However, today many companies offer a whole range of services and corresponding technical means for solving security problems.
For example, such companies solve the problem of telephone communication security in a comprehensive manner, simultaneously solving a number of access control problems, physical protection, closing technical channels of information leakage and using cryptographic closure.
Naturally, in the second case, the efficiency of the solution to the problem of ensuring security will be significantly higher than in the first.
The integrated approach is only taking its first steps and only a few individual companies can offer today, for example, special software and hardware security systems for solving the problem of ensuring information security, which make it possible to ensure the security of all types of information (voice, visual, alphanumeric, etc.) on the basis of a single personal computer (integrated system) during its processing, storage and transmission via communication channels.
Moreover, integrated protection is provided not only by the use of cryptography, but also by blocking both NSD and technical channels of information leakage.
Of course, the integrated approach requires the use of the most complex information technologies and is currently more expensive than traditional ones.
But it is more effective and promising. The era of system integrators is ahead.
Status and development trends of the market of integrated information protection tools and services
Based on the results of the analysis, we can briefly formulate the current status and features of the Russian market of integrated information protection tools:
- general stabilization
-
- of the market of integrated information protection tools;
- due to the specifics of the requirements, it continues to be the most conservativethe sector of cryptographic protection tools, while the most dynamic sectors of the market are access control tools, noise generators, radio control tools, etc.;
- transition to digital methods of processing, storing, transmitting and protecting information;
- implementation of new technologies for protecting information (biometric, holographic, steganographic and other technologies);
- integration of tools, systems and technologies (means of accumulation and encryption of information, means of communication and protection of information, etc.);
- development of network protection technologies (firewalls, means of network analysis, VPN organizations, etc.)
- emergence of new market segments (mobile phone jammers, destroyers of information on magnetic media, digital watermarks”, etc.);
- development of tools and services of system integration, etc.
Main directions and trends in the development of the market of tools and services for integrated information protection:
- integration based on computer technologies is the main direction of development of security tools and systems
- integrated security systems, integrated technologies, integrated tools);
- informatization (information technologies, networks and systems);
- intellectualization (artificial intelligence, neural network technologies, “smart security tools and systems, smart cards);
- globalization (Internet network technologies, means of protecting mobile networks and personal communications);
- widespread introduction of biometric identification means (due to their cost reduction);
- activation of means of protection against forceful destructive influences;
- development of environmentally friendly and safe for humans technologies for protecting information;
- market sectors that provide information protection in such network information structures as electronic business (e-business), electronic banking (e-banking) and electronic commerce (e-commerce) have good development prospects;
- active introduction of wireless technologies for transmitting and protecting information (BLUTOOTH technologies, PROXIMITY, contactless identification, etc.);
- growth of the market volume of system integration, expansion of the geography and range of services of system integrators.