#Fingerprints
Hardware implementation of fingerprint identification methods. |
Nikulin Oleg Yuryevich
How many different passwords do you have to keep in mind — two, three, or maybe more?
What happens if you forget the password?
Use many passwords are, at the very least, inconvenient. And one in all applications is unsafe.
Of course, you can partially solve the problem if you use a system on cards (contactless, smart or iButton).
But the card can be lost, it can be stolen, and the code typed on the keyboard can be spied on or guessed.
The methods widely used today only partially solve the problem of protection against unauthorized access to premises or computer information.
The only indisputably reliable and convenient identifier can only be the user himself, his unique biometric features — the shape of the limbs, fingerprints, face, eyes, voice, etc. Biometrics is certainly the future.
And not that distant.
The leader among biometric identification systems
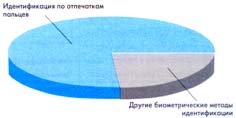
According to Western experts, 80% of the biometrics market today is occupied by fingerprint identification devices (Fig. 1). What is the reason for this?
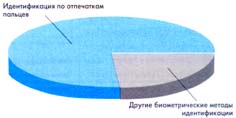
Fig. 1.
The undisputed leadership of fingerprint identification systems.
Firstly, it is one of the most accessible and inexpensive methods, which was widely used even before the advent of computers and television.
Today, the cost of some fingerprint identification systems has already exceeded the $100 mark, while the cost of devices based on other technologies fluctuates around $1,000.
Secondly, the fingerprint identification method is easy to use, convenient and free of psychological barriers, which exist, for example, in systems that require exposure of the eye to a light beam.
In addition, the fact that many later identification methods are protected by patents played a significant role. For example, the IriScan company is the owner of exclusive rights to the iris identification technology. And fingerprinting methods have been known to mankind since time immemorial and have been and are being used intensively in forensic science.
Three approaches to implementing fingerprint identification systems
Today, three main approaches to implementing fingerprint identification systems are known.
We will describe them in the order of their appearance. The earliest and most common method today is based on the use of prism optics and several lenses with a built-in light source. The structure of such a system is shown in Figure 2.
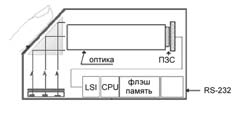
Fig. 2.
Functional diagram of the FIU system from SONY.
Light falling on the prism is reflected from the surface in contact with the user's finger and exits through the other side of the prism, hitting an optical sensor (usually a monochrome video camera based on a CCD matrix), where an image is formed.
In addition to the optical system, the SONY model in question has a built-in processor (Hitachi H8 with 4 MB flash memory for 1000 users), RAM for internal data processing and a DES encryption system.
The disadvantages of such a system are obvious. Reflection strongly depends on the parameters of the skin dryness, presence of oil, gasoline, other chemical elements. For example, people with dry skin experience a blurring effect of the image.
As a result, there is a high proportion of false positives.
An alternative method uses a technique for measuring the electric field of a finger using a semiconductor plate.
When the user places a finger in the sensor, it acts as one of the plates of a capacitor (Fig. 3).
The other capacitor plate is the sensor surface, which consists of a silicon chip containing 90,000 capacitor plates with a reading pitch of 500-dpi. The result is an 8-bit raster image of the ridges and valleys of the finger.

Fig. 3.
Identification system based on a semiconductor wafer.
Naturally, in this case, the skin's fat balance and the user's hand cleanliness do not play any role. In addition, in this case, a much more compact system is obtained.
If we talk about the disadvantages of the method, the silicon chip requires operation in a sealed shell, and additional coatings reduce the sensitivity of the system. In addition, strong external electromagnetic radiation can have some effect on the image.
There is another method of implementing systems. It was developed by the company “Who? Vision Systems”. Their TactileSense system is based on an electro-optical polymer.
This material is sensitive to the difference in the electric field between the ridges and depressions of the skin.
The electric field gradient is converted into a high-resolution optical image, which is then converted into a digital format, which in turn can be transmitted to a PC via a parallel port or USB interface.
The method is also insensitive to the condition of the skin and the degree of its contamination, including chemical contamination. At the same time, the reading device is miniature in size and can be built into, for example, a computer keyboard.
According to the manufacturers, the system has an extremely low cost price (at the level of several tens of dollars).
Table 1. Various technological implementations of fingerprint identification systems
| Properties | Optical system | Semiconductor technology | Electro-optical polymer |
| Small size | no | yes | yes |
| Susceptibility to dry skin | no | yes | yes |
| Surface strength | average | low | high |
| Energy consumption | average | low | low |
| Price | medium | high | low |
The analog video signal obtained by one of the described methods is processed by a verification unit, which reduces noise in the image, is converted into digital form, after which a set of characteristics unique to this fingerprint is extracted from it.
This data uniquely identifies the person. The data is saved and becomes a unique fingerprint template for a specific person. When reading the new fingerprints, they are compared with those stored in the database.
In the simplest case, when processing an image, characteristic points are highlighted on it (for example, the coordinates of the end or bifurcation of papillary lines, the junction of the turns).
It is possible to select up to 70 such points and characterize each of them by two, three or even more parameters. As a result, it is possible to obtain up to five hundred values of various characteristics from the fingerprint.
More complex processing algorithms connect characteristic points of the image with vectors and describe their properties and relative positions (see Fig. 4).
As a rule, the data set obtained from the fingerprint takes up to 1 KB.
 |
 |
Fig. 4a, b.
The processing algorithm allows storing not the image itself, but its “image” (a set of characteristic data).
An interesting question is why the archive does not store the fingerprint images themselves, but only certain parameters obtained using various image processing methods. The answer is limited resources.
The size of each photo is not so small and when we are talking about a user base of several thousand people, the time of loading and comparing the newly received fingerprint with those stored in the database can take too much time.
And the second reason is privacy. Users like anonymity, they do not want their fingerprints to be transferred to law enforcement agencies without their consent or simply stolen by intruders.
Therefore, manufacturers often specifically use non-standard methods of processing and storing the received data.
For security reasons, a number of manufacturers (SONY, Digital Persona, etc.) use encryption tools when transmitting data. For example, the U are U system from Digital Persona uses a 128-bit key, and, in addition, all transmitted packets have a time stamp, which eliminates the possibility of their retransmission.
Data storage and comparison during identification usually takes place in the computer. Almost every hardware manufacturer supplies unique software along with the system, most often adapted for Windows NT. Since most systems are designed to control access to computer information and are primarily aimed at the average user, the software is simple and does not require special configuration.
Typical solutions for protecting a PC from unauthorized access
There are many ways to connect fingerprint readers to a PC. Much depends on the manufacturer's approach and the cost of the systems. For example, the FIU (Fingerprint Identification Unit) system from SONY is a ready-made complex.
The remote unit contains not only a scanner, but also a device for primary information processing and encryption of transmitted data.
The FIU is connected directly to the serial port of the PC.
Less expensive readers usually require additional hardware. For example, the SACcat system from SAC technologes is connected to a PC via a video capture card with an ISA connector. The video capture module is inserted into the computer case.
A similar device from Key Tronic also uses a video capture card, but it is placed in a separate case, which allows the system to be used with laptops.
Readers can be made either as a separate device or built into a keyboard. Such products are manufactured by National Registry, Who? Vision Systems, Digital Persona, etc.
Almost all devices are powered by an external AC source.

Photo 1.
The SACcat system allows you to control access to computer information.
Table 2. Comparative characteristics of a number of devices for protecting against unauthorized access to computer information using fingerprint identification methods
| Characteristic * | U.are.U from “Digital Persona” | FIO from SONY and I/O Software | BioMouse from ABC |
| Type I error ** | 3% | 1% | — |
| Type II error *** | 0.01% | 0.1% | 0.2% |
| Registration time | — | <1 sec | 20 — 30 sec |
| Identification time | <1 sec | 0.3 sec | <1 sec |
| External capture device | no | no | no |
| Encryption | yes | yes | yes |
| Storage Capacity | No | Yes | No |
| Power Source | USB | External | External |
| Connectivity | USB | Serial Port | parallel port |
| Price with software | 200 | 650 | 300 |
* Unfortunately, today there is a real problem of obtaining completely objective information about various products. The world community has not yet developed uniform methods for testing biometric systems.
Each manufacturer conducts independent research, the degree of truthfulness of which is impossible to assess. For example, no one, indicating the probability of error, indicates the sample size, and, at the same time, even a schoolchild can see that the probability of rejections depends very much on the sample size. Therefore, any comparisons are still quite subjective.
** False reject rate is the probability that a registered user will be denied access.
*** Type II error (false acceptance rate) is the probability with which the system allows access to an unregistered user.
Typical solutions for protecting premises from unauthorized access
Access control devices are more cumbersome than computer readers. Firstly, there is no need to save space on the desktop. Secondly, readers must be autonomous, so in addition to the scanner, a decision-making and information storage device, a keyboard (to increase the level of security) and a liquid crystal display (for ease of setup and operation) are placed in one case. If necessary, a card reader (smart, magnetic, etc.) can be connected to the system. There are also more exotic models. For example, SONY placed a speaker in the device case, and Mytec believes that the future lies in the integration of biometrics and iButton tablets.
In addition, devices for protecting premises from unauthorized access should ensure simple connection of electric locks and alarm sensors. They should be easily networked (RS-485 interfaces). For example, if an object has several entrances, all devices should be networked to create a single database. The number of system users in this case increases sharply (up to 50,000 in the Finger Scan system).
All devices present in this market segment use only optics. New technologies are extremely slowly being introduced into security systems.
All the presented devices are designed for indoor use only. The scanner surface must be clean, so dusty warehouses, gas stations, etc. are a priori excluded.
The most common applications are banking systems (access to safes, valuables storage facilities), access control to various clubs and country residences, e-commerce systems.

Photo 2.
The Veriprint 2000 system allows you to control access to premises.
Table 3. Comparative characteristics of a number of devices for protecting against unauthorized access to premises using fingerprint identification methods.
| Characteristics | Finger Scan by “Identix” | Veriprint 2100 by “Biometric ID” |
| Type I error | 1% | 0.01% |
| Type II error | 0.0001% | 0.01% |
| Registration time | 25 sec | <5 sec |
| Identification time | 1 sec | 1 sec |
| Interface | RS232, RS485, TTL, alarm input/output | RS232, RS485, TTL |
| Max. number of users | 50,000 (network version) | 8,000 |
| Flash memory | 512 kV or 1.5 MW | 2 MW or 8 MW |
| Add-on | LCD display, keyboard | LCD display, keyboard |
Fingerprint identification prospects
In the very near future, we can expect fingerprint identification systems to become cheaper and, as a result, more widespread.
Most likely, it is precisely due to their already relatively low cost, availability and ease of use that such systems will be included with computer equipment.
Biometric readers are ideal for building fast and convenient systems for restricting access to information, for e-commerce systems and Internet sites.
And although modern equipment does not fully meet all the requirements, the price is still quite high, and the reliability does not always correspond to the declared one (this, for example, is shown in a test study by the Network Computing magazine), a number of computer equipment manufacturers are already integrating biometrics into their systems.
For example, this was announced at the recent CeBIT-99 exhibition by Compaq.
Experience shows that a sharp surge of interest from computer companies, as a rule, leads to an increase in investment in scientific research and, as a result, to the emergence of new, more universal technical solutions.

Добавить комментарий