Все про видеонаблюдение
Все про умный дом
Все о пожарной безопасности
Сейчас читают
 Как ускорить и смотреть ютуб без тормозов и замедленияЕсли Вы на этой странице, то Вам, скорее всего, […]
Как ускорить и смотреть ютуб без тормозов и замедленияЕсли Вы на этой странице, то Вам, скорее всего, […] 10 лучших прогрессивных языков программирования для разработки мобильных приложенийЗнаете ли вы, что мобильные приложения — это не только […]
10 лучших прогрессивных языков программирования для разработки мобильных приложенийЗнаете ли вы, что мобильные приложения — это не только […] 6 важных особенностей, которые следует учитывать при строительстве нового домаСтроительство нового дома – это уникальная возможность […]
6 важных особенностей, которые следует учитывать при строительстве нового домаСтроительство нового дома – это уникальная возможность […]
Гороскоп на Сегодня
GOST R 51241 Access control and management means and systems.
GOST R 51241 Access control and management tools and systems. GOST R 51241 Access control and management tools and systems GOST R 51241 «Access control and management tools and systems» Work on the standard for access control means, as already noted, began in 1996. It involved the Research Center «Security» of the Ministry of Internal …
GOST R 51241 Access control and management means and systems.Далее …
IBIS — Integrated Ballistics Analysis System.
IBIS — integrated computer system for ballistic examination. IBIS — integrated computer system for ballistic examination Vadim Antoninovich Shelkov IBIS — INTEGRATED COMPUTER SYSTEM FOR BALLISTIC EXPERTISE Source: magazine «Special Equipment» At the MILIPOL exhibition held last fall in Paris, forensic equipment was presented rather sparingly. The French police and gendarmerie presented spectacular imitations of …
Vehicle under attack indicator.
Vehicle under fire indicator. Vehicle Fire Indicator VINITI, 1996 Vehicle Fire Indicator The companies MS Instrunients pie and Lyonje Brandfield Ltd. have developed a vehicle fire indicator, which is a completely passive system capable of detecting fire weapons such as small arms and artillery when fired at a distance of 25 to 100 m. It …
Personal protective equipment for personnel performing work on searching for and defusing explosive objects.
Individual protective equipment for personnel performing work on searching for and defusing explosive objects. Petrenko Evgeny Sergeevich INDIVIDUAL PROTECTIVE EQUIPMENT FOR PERSONNEL PERFORMING WORK ON SEARCHING FOR AND defusing explosive objects To ensure the protection of personnel involved in the search and disposal of explosive ordnance, it is advisable to use various types of personal …
Integrated protection of special shielded rooms.
Vyacheslav Sergeevich Barsukov, Candidate of Technical Sciences INTEGRATED PROTECTION OF SPECIAL SHIELDED ROOMS Source: «Special Equipment» magazine The basis of the modern approach to information protection is ensuring physical protection, which is implemented, first of all, by means of restricting access and blocking physical leakage channels. Moreover, the modern systemic approach to ensuring information protection …
Integrated security systems.
Integrated security systems. Integrated security systems Integrated security systems In recent years, in addition to traditional alarm, security and fire alarm systems, access control and management tools and closed-circuit television systems have been widely used to enhance the security of facilities. The practice of using such a combination by leading companies in the form of …
How to protect yourself from an explosion.
How to protect yourself from an explosion. How to protect yourself from an explosion. How to protect yourself from an explosion. A car is a favorite place for a criminal to hide explosive devices, unless it is being inspected, because a car provides the ability to use explosive devices with virtually any method of detonation, …
ALLEN company catalogue.
Received in April 1999. ALLEN Catalog (volume 1) Established in 1948 to develop and manufacture explosive ordnance disposal equipment and search equipment for the UK Ministry of Defence, Allenhas now expanded its product range and is ready to offer a wide selection of the latest equipment for the disposal of explosive devices, homemade explosive devices, …
Classification and characteristics of technical channels for leakage of information processed by TSPI and transmitted via communication channels. The article was updated in 2023.
Classification and characteristics of technical channels for leakage of information processed by TSPI and transmitted via communication channels Anatoly Anatolyevich Khorev, Candidate of Military Sciences Classification and characteristics of technical channels for leakage of information processed by TSPI and transmitted via communication channels The article is reprinted from the journal «Special Equipment» No. 2, 1998. …
Integrated systems for monitoring toxicological and environmental safety.
Integrated systems for monitoring toxicological and environmental safety. Integrated systems for monitoring toxicological and environmental safety. Ganshin Vladimir Mikhailovich, Candidate of Technical Sciences Chebyshev Alexander Vasilievich, Candidate of Chemical Sciences Fesenko Anatoly Vladimirovich, Doctor of Technical Sciences COMPLEX SYSTEMS FOR MONITORING TOXICOLOGICAL AND ECOLOGICAL SAFETY. Introduction It is well known that recently, cases of threats …
Integrated systems for monitoring toxicological and environmental safety.Далее …
Checking people and their hand luggage for the presence of sabotage and terrorist weapons.
#sabotage and terrorist means, #DTS Control of people and their hand luggage for the presence of sabotage and terrorist means. In recent years, due to significant geopolitical and economic changes, the activity of various kinds of extremist organizations has increased, which are increasingly resorting to terrorism to achieve their goals. Terrorist attacks, unfortunately, have become …
Checking people and their hand luggage for the presence of sabotage and terrorist weapons.Далее …
Checking incoming correspondence for the presence of explosive devices and radioactive substances.
Checking incoming correspondence for explosive devices and radioactive substances. CHECKING INCOMING CORRESPONDENCE (LETTERS, PARCELS) FOR EXPLOSIVE DEVICES AND RADIOACTIVE SUBSTANCES Source: Special Equipment magazine 1. INTRODUCTION One of the main channels for delivering sabotage and terrorist weapons worldwide is the postal channel. Special postal items equipped with explosive devices (ED) are manufactured for mailing. …
Forensic Science Textbook for Universities. Part 1. Read online.
#Forensics Forensics Consists of sections: Theoretical and methodological foundations of forensic science, Forensic technology, Forensic tactics, Forensic investigation methods. CHAPTER 1 FORENSIC SCIENCE AS A FIELD OF SCIENTIFIC KNOWLEDGE N 1. Concept, object, subject of forensic science N 2. Functions, sources, laws of development, methods of forensic science. N 3. The system of forensic science …
Forensic Science Textbook for Universities. Part 1. Read online.Далее …
On the issue of categorizing objects from the standpoint of security.
On the issue of categorizing objects from the standpoint of security. The article discusses the main provisions of the concept of ensuring comprehensive and security security of important objects of the Russian Federation. To determine the required level of security, it is proposed to categorize objects by the nature and scale of possible damage in …
On the issue of categorizing objects from the standpoint of security.Далее …
Small-sized night sights.
Small-sized night sights. VOLKOV Viktor Genrikhovich, Candidate of Technical Sciences, Associate Professor Currently, night vision devices have become widespread in special equipment [1]. Among them, night sights play a significant role, which are widely used for shooting from individual hunting, sporting and combat weapons. This article discusses various types of night sights made on the …
Metal detectors: installation, setup, operation.
Metal detectors: installation, setup, operation. Metal detectors: installation, setup, operation METAL DETECTORS: INSTALLATION, SETUP, OPERATION When choosing arch metal detectors (AMD), consumers are primarily interested in the technical and operational parameters of a particular model. This raises many questions — from the most general and elementary to quite complex ones, concerning very specific areas of …
Metal detectors. Issues of standardization of requirements.
Metal detectors. Issues of standardization of requirements. Metal detectors. Issues of standardization of requirements. Berezansky David Pavlovich, Candidate of Technical Sciences Metal detectors — inspection devices. Issues of standardization of requirements. The article is reprinted from the journal «Special Equipment» No. 2, 1998. For a wide range of readers of the magazine, a number of …
Metal detectors. Issues of standardization of requirements.Далее …
Methodology for detecting traces of firearms and explosives.
Journal of Forensic Science Society. — 1994. — April. — No. 2- P. 107-116. Methodology for detecting traces of firearms and explosives The Journal of Forensic Science Society has published an article describing a method for detecting traces of firearms and explosives ( BB). The above technique is an important aspect of the work of …
Methodology for detecting traces of firearms and explosives.Далее …
Multi-level systems of aviation and fire safety during ground handling of aircraft.
Multi-level aviation and fire safety systems for ground handling of aircraft.. Multi-level aviation and fire safety systems for ground handling of aircraft. Zubkov Boris Vasilievich, Doctor of Technical Sciences, Professor Bochkarev Alexander Nikolaevich, Associate Professor Department of Flight Safety and Life Support, Moscow State Technical University of Civil Aviation, Multi-level systems of aviation and fire …
Multi-level systems of aviation and fire safety during ground handling of aircraft.Далее …
Head-mounted night vision devices.
Head-mounted night vision devices. VOLKOV Viktor Genrikhovich, Candidate of Technical Sciences, Associate Professor Efficient night vision devices (NVD) are required for special operations [1]. They provide observation at dusk, at night, and in some cases also in low atmospheric transparency (haze, fog, rain, snowfall, etc.). At the same time, situations often arise when the operator's …
SOME FEATURES OF SEARCHING FOR EXPLOSIVES AND EXPLOSIVE OBJECTS USING DOGS, GAS ANALYTICAL INSTRUMENTS AND CHEMICAL RAPID TESTS. Article updated in 2023.
SOME FEATURES OF SEARCHING FOR EXPLOSIVES AND EXPLOSIVE OBJECTS WITH THE HELP OF DOGS, GAS ANALYTICAL INSTRUMENTS AND CHEMICAL RAPID TESTS. PETRENKO Evgeny Sergeevich SOME FEATURES OF SEARCHING FOR EXPLOSIVES AND EXPLOSIVE OBJECTS WITH THE HELP OF DOGS, GAS ANALYTICAL INSTRUMENTS AND CHEMICAL RAPID TESTS. The problem of the rapid search for explosives, explosive devices …
Some features of the implementation of passive protection measures in vibroacoustic channels of speech information leakage.
Some features of the implementation of passive protection measures in vibroacoustic channels of speech information leakage. Part 1 The necessity and importance of carrying out measures to protect premises from leakage of speech information via vibroacoustic channels is extremely relevant not only when fulfilling regulated requirements for the protection of designated premises in which information …
Some tips on how to behave in the event of a bomb threat.
Some tips on behavior during an explosion threat.. Some tips on behavior during an explosion threat. Petrenko Evgeny Sergeevich SOME TIPS ON BEHAVIOR DURING AN EXPLOSION THREAT Explosive terrorism has unfortunately become a reality today. There is no hope that this nightmare will end in the near future. It is also not yet possible to …
Some tips on how to behave in the event of a bomb threat.Далее …
Some technical features of the solution to the problem of humanitarian demining.
#humanitarian demining Some technical features of solving the problem of humanitarian demining. PETRENKO Evgeny Sergeevich Mankind, although not today and not suddenly, has faced another rather serious problem — the problem of humanitarian demining. The essence of this problem is that in various regions of the world after the end of military conflicts there are …
Some technical features of the solution to the problem of humanitarian demining.Далее …
New channels for leakage of confidential speech information through fiber-optic subsystems of structured cabling systems.
New channels for leakage of confidential speech information through fiber-optic subsystems of SCS. New channels for leakage of confidential speech information through fiber-optic subsystems of SCS 1Grishachev Vladimir Vasilievich, candidate of physical and mathematical sciences, associate professor 1Khalyapin Dmitry Borisovich, candidate of technical sciences, professor 1Shevchenko Natalia Andreevna, 2Merzlikin Vladimir Gavrilovich, candidate of technical sciences, …
GENERAL PROVISIONS FOR PRESERVING THE SURVIVABILITY AND PROTECTION OF RADIOELECTRONIC EQUIPMENT FROM THE EFFECTS OF ELECTROMAGNETIC WEAPONS AND ELECTRONIC TERRORISM.
GENERAL PROVISIONS FOR PRESERVING THE SURVIVABILITY AND ENSURING THE PROTECTION OF RADIOELECTRONIC EQUIPMENT FROM THE EFFECTS OF ELECTROMAGNETIC WEAPONS AND ELECTRONIC TERRORISM.. GENERAL PROVISIONS FOR PRESERVING THE SURVIVABILITY AND ENSURING THE PROTECTION OF RADIOELECTRONIC EQUIPMENT FROM EFFECTS OF ELECTROMAGNETIC WEAPONS AND ELECTRONIC TERRORISM. RYABOV Yuri Georgievich, Candidate of Technical Sciences, Senior Researcher GENERAL PROVISIONS FOR …
Review of the market of night vision devices of Russian production.
Read the beginning of the article — «Overview of the market of night vision devices of Russian production.» Continued: A similar development of «ROMZ» — the NZT-P sight, has repeatedly been awarded gold medals at exhibitions (photo 13). A similar model is also produced by the Krasnogorsk plant under the brand name NV-300P(export version — …
Review of the market of night vision devices of Russian production.Далее …
Estimation of the maximum detection depth of ferromagnetic objects of artificial origin in the thickness of a semiconducting medium.
Estimation of the maximum detection depth of artificial ferromagnetic objects in the thickness of a semiconducting medium.. Estimation of the maximum detection depth of artificial ferromagnetic objects in the thickness of a semiconducting medium. SHCHERBAKOV Grigory Nikolaevich, professor, doctor of technical sciences ANTSELEVICH Mikhail Aleksandrovich, doctor of technical sciences UDINTSEV Dmitry Nikolaevich, candidate of technical …
Polygraph examination and polygraph examiner competence.
Polygraph survey and polygraph examiner competence. Yuri Ivanovich Kholodny, Doctor of Law, Candidate of Psychological Sciences, Professor of the Department of Bauman Moscow State Technical University Source: Scientific and practical journal «THEORY AND PRACTICE OF FORENSIC EXAMINATION» No. 1 (13) 2009 The author considers the «method of the OIP» (interview using a polygraph) as «an …
Polygraph examination and polygraph examiner competence.Далее …
Organization of work with confidential documents.
Organization of work with confidential documents.. Organization of work with confidential documents. Organization of work with confidential documents. Source — users.g.ua Establishing the procedure for classified office work. When working to protect commercial secrets, it is necessary to pay special attention to the company's documents, since most commercial structures in our country store the main …
ORGANIZING INFORMATION PROTECTION FROM LEAKAGE VIA TECHNICAL CHANNELS.
ORGANIZING INFORMATION PROTECTION FROM LEAKAGE VIA TECHNICAL CHANNELS. KHOREV Anatoly Anatolyevich, Doctor of Technical Sciences, Professor General Provisions Protected information refers to information that is the subject of ownership and is subject to protection in accordance with the requirements of legal documents or requirements established by the owner of the information. This is, as a …
ORGANIZING INFORMATION PROTECTION FROM LEAKAGE VIA TECHNICAL CHANNELS.Далее …
Organization of protection of commercial secrets at the enterprise.
Organization of protection of commercial secrets at the enterprise. Organization of protection of commercial secrets at the enterprise. Organization of protection of commercial secrets at the enterprise. Source— pps.ru To ensure the protection of intellectual property at enterprises, a certain procedure for working with information and access to it is introduced, including a set of …
Organization of protection of commercial secrets at the enterprise.Далее …
Smell detection using dogs.
Smell training with dogs. Smell training with dogs Smell training with dogs Practice shows that dogs can be successfully used to recognize various odors in concentrations significantly lower than a person can distinguish. The options for using dogs and, accordingly, the skills developed for this purpose are very diverse. They are always based on one …
From Olfactory Models to Electronic Nose. New Possibilities of Parallel Analytics.
From olfactory models to an electronic nose. New possibilities of parallel analytics. From olfactory models to an electronic nose. New possibilities of parallel analytics GANSHIN Vladimir Mikhailovich, Candidate of Technical Sciences FESENKO Anatoly Vladimirovich, Doctor of Technical Sciences CHEBYSHEV Alexander Vasilievich, Candidate of Chemical Sciences FROM OLFACIAL MODELS TO THE “ELECTRONIC NOSE”. NEW POSSIBILITIES OF …
From Olfactory Models to Electronic Nose. New Possibilities of Parallel Analytics.Далее …
On the evidentiary value of log files.
On the evidentiary value of log files. On the evidentiary value of log files. On the evidentiary value of log files. I. Sobetsky Currently, the fight against crime in the high-tech sphere is gaining momentum. Since the adoption of the new Criminal Code of the Russian Federation, which included Articles 272-274 on liability for crimes …
Resolution of the Government of the Russian Federation of July 1, 1996 No. 770.
Resolution of the Government of the Russian Federation of July 1, 1996 N 770. Resolution of the Government of the Russian Federation of July 1, 1996 N 770 Resolution of the Government of the Russian Federation of July 1, 1996 N 770 «On approval of the regulation on licensing the activities of individuals and legal …
Resolution of the Government of the Russian Federation of July 1, 1996 No. 770.Далее …
Actions of private security company employees upon detection of explosive devices
#detection of explosive devices Practical actions of private security company employees upon detection of explosive devices. KS GUVD «Practical recommendations» As experience shows, an explosive device (ED) or a suspicious object is detected either by employees or visitors of the facility, who inform the nearest security guard about the find or call the duty officer …
Actions of private security company employees upon detection of explosive devicesДалее …
Entrepreneurship and crime.
Entrepreneurship and crime. Entrepreneurship and crime Entrepreneurship and crime. PREFACE. With the development of market relations and the formation of commercial structures, millions of citizens discover entrepreneurship as a way of life. With the first successes and failures in business, sooner or later comes the understanding of the need to protect their rights and interests. …
Application of magnetic tomography in walk-through metal detectors.
Application of magnetic tomography in walk-through metal detectors.. Application of magnetic tomography in walk-through metal detectors. Application of magnetic tomography in walk-through metal detectors Grigory Nikolaevich Shcherbakov, Professor, Doctor of Technical Sciences,Antselevich Mikhail Aleksandrovich, professor, doctor of technical sciences, Udintsev Dmitry Nikolaevich, doctor of technical sciences, Shlykov Yuri Aleksandrovich, candidate of technical sciences, Brovin Andrey …
Application of magnetic tomography in walk-through metal detectors.Далее …
Problems of ensuring safety in civil aviation.
Problems of ensuring safety in civil aviation. Problems of ensuring safety in civil aviation. Aviation Week & Space Technology.- 1996 .— 145, No. 4 — P.23-27. New Security Issues in Civil Aviation The explosion of TWA Flight 800 of TRANS World Airlines on July 17, 1996 raised new security issues in civil aviation, as it …
PROBLEMS OF APPLICATION OF DIGITAL VIDEO RECORDING TECHNOLOGIES IN FORENSIC SCIENCE.
PROBLEMS OF APPLICATION OF DIGITAL VIDEO RECORDING TECHNOLOGIES IN FORENSIC SCIENCE. A.V. Kholopov, postgraduate student of the Department of Forensic Science, St. Petersburg Law Institute of the Prosecutor General's Office of the Russian Federation Information Security. Confidential No. 1, 2003 Modern digital technologies in the field of recording audiovisual information have reached such a level …
PROBLEMS OF APPLICATION OF DIGITAL VIDEO RECORDING TECHNOLOGIES IN FORENSIC SCIENCE.Далее …
Contradictory trends in the implementation of the Russian Federation Law on State Secrets.
Contradictory trends in the implementation of the Russian Federation Law On State Secrets. Contradictory trends in the implementation of the Russian Federation Law On State Secrets Contradictory trends in the implementation of the Russian Federation Law «On State Secrets» What is an «object» of a state secret? In modern Russian business, recently they have been …
Contradictory trends in the implementation of the Russian Federation Law on State Secrets.Далее …
Ways to improve the noise immunity of magnetometric search equipment and their practical implementation.
Ways to improve noise immunity of magnetometric search tools and their practical implementation.. Ways to improve noise immunity of magnetometric search tools and their practical implementation. SHCHERBAKOV Grigory Nikolaevich, professor, doctor of technical sciences, ANTSELEVICH Mikhail Aleksandrovich, professor, doctor of technical sciences, UDINTSEV Dmitry Nikolaevich, candidate of technical sciences, FILIN Vladimir Grigorievich, VOLOSHKO Vitaly Sergeevich. …
Order of the President of the Russian Federation of May 30, 1997 No. 226-rp On approval of the list of officials of state authorities vested with the authority to classify information as a state secret.
Order of the President of the Russian Federation of May 30, 1997 N 226-rp On approval of the list of officials of state authorities vested with the authority to classify information as a state secret.. Order of the President of the Russian Federation of May 30, 1997 N 226-rp On approval of the list of …
DEVELOPMENT, PRODUCTION AND SUPPLY OF INTELLIGENCE TECHNICAL MEANS.
DEVELOPMENT, PRODUCTION AND SUPPLY OF TECHNICAL RECONNAISSANCE MEANS. The US Department of Defense continues to focus on tactical laser weapons. At a 1996 symposium of representatives of the US defense industry, many of the presentations by its participants reflected the continuing interest of military circles in expanding the applications of tactical lasers, not limiting them …
DEVELOPMENT, PRODUCTION AND SUPPLY OF INTELLIGENCE TECHNICAL MEANS.Далее …
Destroyers of explosive devices and other explosive objects.
Destroyers of explosive devices and other explosive objects. PETRENKO Evgeny Sergeevich DESTROYERS OF EXPLOSIVE DEVICES AND OTHER EXPLOSIVE OBJECTS The problem of searching for and defusing explosive devices and other explosive objects (ED), unfortunately, continues to be relevant throughout the world due to the increasing attempts to use these devices to carry out terrorist acts …
Destroyers of explosive devices and other explosive objects.Далее …
Rocket-propelled anti-tank grenades.
Rocket-propelled anti-tank grenades. Rocket-propelled anti-tank grenades Rocket-propelled anti-tank grenades WORK on the creation of rocket-propelled anti-tank grenades in the USSR began at the turn of the 1970s. Their main developers were the Bazalt Design Bureau and the TsKIB SOO Tula. In the 1970s and 1980s, these design bureaus developed several highly effective systems that successfully …
Advertising must be legal.
Advertising must be legal. Advertising must be legal Advertising must be LEGAL According to the current legislation (Articles 24 and 32 of the Federal Law «On Fire Safety», Resolution of the Government of the Russian Federation of August 23, 1993 No. 849), activities (works, services) in the field of fire safety are subject to mandatory …
X-ray television installations.
X-ray television installations. X-ray television installations X-ray television installations In the journal «Systems of Security, Communications and Communications», 1998, No. 2 (20) an article by Yu. I. Olshansky «Nuclear-Physical Methods of Detecting Explosives» was published. Neither the author nor the editors planned to continue this topic in the near future. However, due to its relevance …
Decision of the State Technical Commission of Russia.
Decision of the State Technical Commission of Russia.. Decision of the State Technical Commission of Russia. Decision of the State Technical Commission of Russia. At a meeting of the State Technical Commission under the President of the Russian Federation, the issue of «On the protection of information when Russia enters the international information system Internet» …
Decision of the State Technical Commission of Russia.Далее …
System of training and testing of operators of X-ray systems and installations LINESCAN TnT.
Training and testing system for operators of X-ray systems and LINESCAN TnT installations. Training and testing system for operators of X-ray systems and installations LINESCAN TnT Prospectuses of the company EG SeG Astrophysics. — 1995. Training and testing system for operators of X-ray systems and installations LINESCAN TnT. The LINESCAN TnT system was developed by …
System of training and testing of operators of X-ray systems and installations LINESCAN TnT.Далее …
INTELLIGENT SYSTEMS FOR BLOCKING CELLULAR TELEPHONY, COMMUNICATION CHANNELS AND CONTROL.
#blocking cellular communications SYSTEMS OF INTELLIGENT BLOCKING OF CELLULAR TELEPHONY, COMMUNICATION AND CONTROL CHANNELS VASILIEV Oleg Aleksandrovich, Candidate of Technical Sciences, EGOROV Dmitry Olegovich, KADYKOV Aleksey Nikolaevich. The article briefly examines the strategy for constructing systems for suppressing radio communication and control channels using panoramic reception to detect short signals and block the subscriber's receiver …
INTELLIGENT SYSTEMS FOR BLOCKING CELLULAR TELEPHONY, COMMUNICATION CHANNELS AND CONTROL.Далее …
Access control systems-2000.
Access control systems-2000. This review includes some companies that, in the author's opinion, have been most active in recent years in the Russian market of access control and management tools and systems. In 2000, GOST R 51241-98 «Access control and management tools and systems. Classification. General technical requirements. Test methods» came into force. This standard …
State and development trends of the security market in 2000.
Security market status and development trends in 2000. Security market status and development trends in 2000. Security market status and development trends in 2000. Vladimir Aleksandrovich Minaev, Technical Director of the Alternative-M holding, spoke at the seminar with an analysis of the Russian market of technical security equipment in 1999-2000. We are publishing the main …
State and development trends of the security market in 2000.Далее …
Tips for securing wireless networks.
Tips for securing wireless networks. Tips for securing wireless networks. Tips for securing wireless networks. Michael Otey, Senior Technical Editor for Windows & .NET Magazine and President of TECA. Source— Wireless is the fastest growing area of LAN technology, and for good reason. The ability to move around your work environment while still having access …
MODERN DATA TRANSMISSION RADIO MODEMS..
MODERN DATA TRANSMISSION RADIO MODEMS.. MODERN DATA TRANSMISSION RADIO MODEMS. SERDYUKOV Petr Nikolaevich, Doctor of Technical Sciences ZORIN Vasily Ivanovich, Doctor of Electrical Engineering BELCHIKOV Anatoly Vladimirovich, Candidate of Technical Sciences LAVRENTYEV Alexey Igorevich MODERN DATA TRANSMISSION RADIO MODEMS. BRIEF OVERVIEW Currently, radio modems have been developed and manufactured that are used to transmit digital …
Modern methods of intercepting information.
Modern methods of intercepting information. Modern methods of intercepting information MODERN METHODS OF INTERCEPTING INFORMATION Victor Iksar “Information (from the Latin informatio — explanation, presentation) is data transmitted by some people to other people orally, in writing or in some other way (for example, with the help of conventional signals, using technical means, etc.), …
CURRENT STATE AND PROSPECTS FOR DEVELOPMENT OF BULLET TRAPS FOR SHOOTING RIFLED FIREARMS.
CURRENT STATE AND PROSPECTS FOR THE DEVELOPMENT OF BULLET TRAPPERS FOR SHOOTING RIFLED FIREARMS.. CURRENT STATE AND PROSPECTS FOR THE DEVELOPMENT OF BULLET TRAPPERS FOR SHOOTING RIFLED FIREARMS. Petrenko Evgeny Sergeevich CURRENT STATE AND PROSPECTS FOR THE DEVELOPMENT OF BULLET TRAPPERS FOR SHOOTING RIFLED FIREARMS. Source: Magazine «Special Equipment», 2000, No. 6. Conducting ballistic examinations …
CURRENT STATE AND PROSPECTS FOR DEVELOPMENT OF BULLET TRAPS FOR SHOOTING RIFLED FIREARMS.Далее …
Specifics of constructing perimeter security systems.
#perimeter alarm Specifics of building perimeter security systems. Specifics of building perimeter security systems Specifics of building perimeter security systems The article offered to your attention opens a series of publications devoted to the effective use of modern technical security means (TSM), primarily perimeter ones, in security systems of various objects. Since the price …
Specifics of constructing perimeter security systems.Далее …
Acoustic reconnaissance equipment: wired microphone systems and electronic stethoscopes.
Acoustic reconnaissance equipment: wired microphone systems and electronic stethoscopes. Acoustic reconnaissance equipment: wired microphone systems and electronic stethoscopes KHOREV Anatoly Anatolyevich, professor, doctor of technical sciences ACOUSTIC RECONNAISSANCE MEANS: WIRED MICROPHONE SYSTEMS AND ELECTRONIC STETHOSCOPES Source: Magazine «Special Equipment and Communications» Wired Microphone Systems Acoustic reconnaissance equipment is actively used to intercept speech information from …
Acoustic reconnaissance equipment: wired microphone systems and electronic stethoscopes.Далее …
Means of information flow analysis.
Information flow analysis tools. Information flow analysis tools Information flow analysis tools The use of data flow inspection methods to protect the information resources of an organization's network allows identifying information impacts at the earliest stages. Since overcoming the vulnerabilities of the basic TCP/IP protocols by making changes to the software implementations of network services …
Means and systems for protecting the perimeters of objects.
Means and systems for protecting the perimeters of objects. Means and systems for protecting the perimeters of objects Means and systems for protecting the perimeters of objects There is no universal detection system (DS) that would be optimal for the entire territory of Russia and a variety of operating conditions, and it is unlikely that …
Means and systems for protecting the perimeters of objects.Далее …
Means and methods for localizing the damaging effects of an explosion.
Means and methods for localizing the damaging effect of an explosion. Petrenko Evgeny Sergeevich MEANS AND METHODS FOR LOCALIZING THE DAMAGING EFFECT OF AN EXPLOSION At present, domestic and foreign industry produces means of localizing the damaging effects of an explosion, which include anti-fragmentation blankets and mats and containers for temporary storage, carrying and …
Means and methods for localizing the damaging effects of an explosion.Далее …
Means for searching for explosive objects by indirect signs.
Means of searching for explosive objects by indirect signs. Petrenko Evgeny Sergeevich MEANS OF SEARCHING FOR EXPLOSIVE OBJECTS BY INDIRECT SIGNS At present, both in Russia and abroad, a number of means of searching for explosive charges (HE) and explosive objects (EO) have been developed and produced, both by direct and indirect signs. A direct …
Means for searching for explosive objects by indirect signs.Далее …
Computer equipment. Firewalls.
Computer equipment. Firewalls. Protection against unauthorized access to information. Indicators of protection against unauthorized access to information. This guideline establishes a classification of firewalls (FW) by the level of protection against unauthorized access (UA) to information based on a list of security indicators and a set of requirements describing them. In this document, computer networks …
Forensic psychophysiological examination using a polygraph: the period of formation.
Forensic psychophysiological examination using a polygraph: the formation period. Yu. I. Kholodny Doctor of Law, Candidate of Psychological Sciences (Bauman Moscow State Technical University) Source: Bulletin of Criminalistics (issue 25.29) Fifteen years ago, in March 1993, polygraph interviews (hereinafter referred to as OIP) were approved for use in operational-investigative activities (hereinafter referred to as OIA) …
Forensic psychophysiological examination using a polygraph: the period of formation.Далее …
Terrorism is a threat to modern society and the individual.
Terrorism is a threat to modern society and individuals. V. Shelkov. Terrorism has become a true scourge of modern society. Before our very eyes, the fight against it has become the main task of the world's leading intelligence agencies. It seems that the roots of terrorism are eternal and inherent in human nature itself, since …
Terrorism is a threat to modern society and the individual.Далее …
Technical means for rapid penetration into closed spaces.
Technical means of rapid penetration into enclosed spaces. Technical means of rapid penetration into enclosed spaces. Technical means of rapid penetration into enclosed spaces. The Canadian company MREL (Mining Resource Engineering Ltd) has developed the Breachcase Mkll shield., which can form openings in the walls of premises with dimensions that allow a person to pass …
Technical means for rapid penetration into closed spaces.Далее …
Equipment for emergency rescue operations.
Equipment for emergency rescue operations. Equipment for emergency rescue operations. Design News.- 1995 .-9, №11.-P. 44. Equipment for emergency rescue operations. As noted in Design News magazine, an important task of emergency rescue services and teams is to search for survivors under the rubble of destroyed buildings after earthquakes and other natural disasters, as well …
Technical and forensic support for investigations.
Technical and forensic support for investigation. Ministry of Education and Science of the Russian Federation State educational institution of higher professional education «Tambov State Technical University» Chernyshov V.N., Sysoev E.V., Seleznev A.V., Terekhov A.V. Study manual for full-time and part-time students of the specialty 030501 «Jurisprudence»Approved by the Academic Council of TSTU as a textbook …
Trojan programs.
Trojan programs. Trojan programs . Trojan programs A Trojan is any program that secretly performs some unwanted actions for the user. These actions can take any form — from determining the registration numbers of software installed on the computer to compiling a list of directories on its hard drive. A Trojan can disguise itself as …
Decree of the President of the Russian Federation of June 23, 1995 N 633 On priority measures for the implementation of the Federal Law On the Federal Security Service Bodies in the Russian Federation.
Decree of the President of the Russian Federation of June 23, 1995 N 633 On priority measures for the implementation of the Federal Law On the Federal Security Service Bodies in the Russian Federation. Decree of the President of the Russian Federation of June 23, 1995 N 633 On priority measures to implement the Federal …
Decree of the President of the Russian Federation of November 30, 1995 No. 1203 On approval of the list of information classified as a state secret.
Decree of the President of the Russian Federation of November 30, 1995 N 1203 On approval of the list of information classified as a state secret. Decree of the President of the Russian Federation of November 30, 1995 N 1203 «On approval of the list of information classified as a state secret» Decree of the …
Information security management in enterprise networks.
Information security management in enterprise networks. Information security management in enterprise networks Information security management in enterprise networks Internet technologies have changed not only the approaches of organizations to doing business, but also their attitude to ensuring network security. The boundaries of corporate networks are no longer defined by the installed equipment. Now these boundaries …
Information security management in enterprise networks.Далее …
Selective protection for cars of S MacNeillie & Son Ltd.
Selective protection for cars of the company S MacNeillie & Son Ltd.. Selective protection for cars of the company S MacNeillie & Son Ltd. VINITI, 1996 Selective protection for cars of the company S MacNeillie & Son Ltd. The company has been building bodywork for special vehicles since 1912 and has been producing comfortable, functional …
Selective protection for cars of S MacNeillie & Son Ltd.Далее …
Computing and theft.
Computer equipment and theft. Computer equipment and theft Computer equipment and theft If you value not only the information stored on your computer's hard drive, but also the computer itself, look for a means of protecting yourself from theft of its components. In one of the previous issues of the magazine, an article was published …
Types of shooting from short-barreled weapons.
Types of shooting from short-barreled weapons. Types of shooting from short-barreled weapons Types of shooting from short-barreled weapons In fiction or specialized literature, in the jargon of professionals dealing with firearms, you can hear terms that denote various types of shooting («fire», as they often say). This implies a classification of these types. If we …
Internal deflagration explosions.
Internal deflagration explosions. Internal deflagration explosions Internal deflagration explosions Characteristics of an internal deflagration explosion The most common explosions are deflagration explosions that occur indoors. They are characterized by a variety of manifestations, since the layouts of residential, office and industrial premises are different. A deflagration explosion requires the presence of flammable gas or vapor …
Issues of ensuring security of corporate wireless networks.
Security issues for corporate wireless networks. Security issues for corporate wireless networks. Security issues for corporate wireless networks. Maxim Filippov, project manager of the company OJSC «Elvis-Plus» Source — This article is an attempt to review the current state of wireless network security in order to answer the question: is it possible today to build a …
Issues of ensuring security of corporate wireless networks.Далее …
Chemical traps as a means of combating petty theft.
Chemical traps — as a means of combating petty theft.. Chemical traps — as a means of combating petty theft. Chemical traps — as a means of combating petty theft. Dubik Stanislav Nikolaevich, leading specialist of the KTC «Security Systems» Security Systems, No. 21, 2001 The problem of petty theft has existed since time immemorial …
COLD WEAPONS WITH IMPACT-CRUSHING EFFECT.
COLD WEAPONS OF IMPACT-CRUSHING EFFECT Dyakonov P.A., lecturer Moscow Academy of the Ministry of Internal Affairs of Russia Forensic examination of bladed weapons has received sufficient attention over the past forty years. At present, we can probably already speak of an independent forensic doctrine of bladed weapons as a branch of forensic technology. The greatest …
Law of the Russian Federation of June 10, 1993 N 5151-1 On certification of products and services.
Law of the Russian Federation of June 10, 1993 N 5151-1 On Certification of Products and Services. Law of the Russian Federation of June 10, 1993 N 5151-1 On Certification of Products and Services. Law of the Russian Federation of June 10, 1993 N 5151-1 «On Certification of Products and Services» (as amended by Federal …
Secure client/server interaction.
Secure client/server interaction. Secure client/server interaction Secure client/server interaction Information security issues are far from limited to individual issues of access control and firewalling, which are most often considered by the authors of publications. In this article we have tried to correct this shortcoming Multi-level client/server architecture In modern information systems built in the client/server …
Protection of information resources in a corporate network using firewalls.
Protection of information resources in a corporate network using firewalls. Protection of information resources in a corporate network using firewalls Protection of information resources in a corporate network using firewalls Issues of information security on the Internet remain among the most pressing today. In this regard, the authors of the article introduce readers to an …
Protection of information resources in a corporate network using firewalls.Далее …
Protection against attacks on basic functions of Windows NT OS.
Protection against attacks on basic Windows NT OS functions. As stated earlier, attacks on data availability are becoming increasingly common on the Internet. The possibility of their successful implementation follows from the vulnerability of basic information exchange protocols on the Internet. In addition, there are typical weaknesses in the implementation of TCP/IP protocols inherited by …
Protection against attacks on basic functions of Windows NT OS.Далее …
Table 6. Mobile phone blocking tools.
Table 6. Mobile phone blocking tools. Name Brief description Developer (supplier) Purpose Note “RS jammer” Intelligent cell phone jammer. Range – 15 m NPF “Radioservice” Blocking information leakage via GSM 900/1800, NMT-450, CDMA, AMPS/DAMPS cellular communication channels Composition: 1. Jammer; 2. Antennas;3. Amplifiers for 1, 2, 4 and 20 W (for operational search and …
Systems for intelligent blocking of cellular telephony, communication channels and control.
Systems for intelligent blocking of cellular telephony, communication channels and control.. Systems for intelligent blocking of cellular telephony, communication channels and control. VASILIEV Oleg Aleksandrovich, Candidate of Technical Sciences, EGOROV Dmitry Olegovich, KADYKOV Aleksey Nikolaevich. INTELLIGENT BLOCKING SYSTEMS OF CELLULAR TELEPHONY, COMMUNICATION AND CONTROL CHANNELS The article briefly examines the strategy for constructing systems …
Systems for intelligent blocking of cellular telephony, communication channels and control.Далее …
Counteracting postal terrorism.
Counteracting postal terrorism.. Counteracting postal terrorism. SHELKOV Vadim Antoninovich COUNTERACTING POSTAL TERRORISM С It is regrettable to note that terrorism has become an integral attribute of the modern world. The range of means used by terrorists remains exceptionally wide. But the most common is the use of explosive devices. With some sadistic passion, news sites …
From olfactory models to the “electronic nose”.
From olfactory models to the “electronic nose”.. From olfactory models to the “electronic nose”. GANSHIN Vladimir Mikhailovich, Candidate of Technical Sciences FESENKO Anatoly Vladimirovich, Doctor of Technical Sciences CHEBYSHEV Alexander Vasilievich, Candidate of Chemical Sciences FROM OLMAR MODELS TO THE “ELECTRONIC NOSE”. NEW POSSIBILITIES OF PARALLEL ANALYTICS Rapid progress in the field of electronic vision …
General provisions for maintaining survivability and ensuring protection of electronic equipment from the effects of electromagnetic weapons and electronic terrorism.
General provisions for maintaining survivability and ensuring protection of electronic equipment from the effects of electromagnetic weapons and electronic terrorism.. General provisions for maintaining survivability and ensuring protection of electronic equipment from the effects of electromagnetic weapons and electronic terrorism. RYABOV Yuri Georgievich, candidate of technical sciences, senior researcher GENERAL PROVISIONS FOR PRESERVING THE SURVIVABILITY …
Features of searching for explosives and explosive objects using dogs, gas analysis devices and chemical express tests.
Some features of the search for explosives and explosive objects using dogs, gas analysis devices and chemical rapid tests. PETRENKO Evgeny Sergeevich SOME FEATURES OF THE SEARCH FOR EXPLOSIVES AND EXPLOSIVE OBJECTS USING DOGS, GAS ANALYTICAL DEVICES AND CHEMICAL RAPID TESTS. The problem of rapid search for explosives (HE), explosive devices and other explosive objects …
Metal detectors — inspection devices. Issues of standardization of requirements.
Metal detectors — inspection devices. Issues of standardization of requirements. Berezansky David Pavlovich, Candidate of Technical Sciences METAL DETECTORS — INSPECTION DEVICES ISSUES OF STANDARDIZATION OF REQUIREMENTS For a wide range of readers of the magazine, a number of problems on standardization of requirements for metal detectors, as one of the important types of inspection …
Metal detectors — inspection devices. Issues of standardization of requirements.Далее …
Day-night sight technology.
Day-night sight technology.. Day-night sight technology. VOLKOV Viktor Genrikhovich, Candidate of Technical Sciences, Associate Professor DAY-NIGHT SIGHT TECHNOLOGY”. Modern anti-terrorist and special operations are highly dynamic and place strict demands on sights for individual weapons. One of the main requirements is to ensure round-the-clock operation. In this regard, this review examines the technology of …
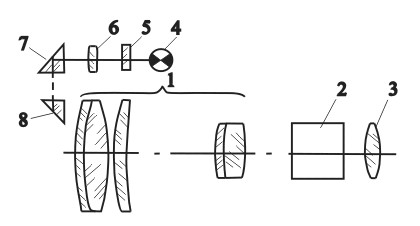
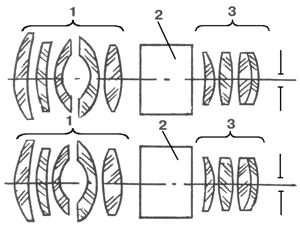
SHIP'S NIGHT VISION DEVICES.. Article updated in 2023.
SHIP'S NIGHT VISION DEVICES. VOLKOV Viktor Genrikhovich, Candidate of Technical Sciences, Associate Professor SHIP'S NIGHT VISION DEVICES (Part 2) End. Beginning in No. 1, 2006 Multichannel ship NVD systems most often include a daytime TV system, a NTFS, a TVP, as well as a laser rangefinder and a target tracking radar. Such an instrument complex …
SHIP'S NIGHT VISION DEVICES.. Article updated in 2023.Далее …
What is a biometric gun safe and how can it help make your home safer?
What is a biometric gun safe and how can it help make your home safer? What is a biometric gun safe and how can it help make your home safer? What is a biometric gun safe and how can it help make your home safer? This type of safe operates in the same way as …
What is a biometric gun safe and how can it help make your home safer?Далее …
Why is it necessary to draw up a fire safety protocol?
Why do you need to draw up a fire safety protocol. Why do you need to draw up a fire safety protocol? Why do you need to draw up a fire safety protocol? Fire safety protocol When passing the initial inspection of a new premises or building for compliance with fire safety requirements, a fire …
Why is it necessary to draw up a fire safety protocol?Далее …
Complexity categories and types of fires. Overview.
Complexity categories and types of fires. Overview. Complexity categories and types of fires. Overview Complexity categories and types of fires. Overview There are several parameters by which the degree of complexity of a fire is assessed, from the point of view of the fire fighting process itself. These parameters include: levels of complexity, types of …
Classification of personal protective equipment, their storage and testing.
Classification of personal protective equipment, their storage and testing. Classification of personal protective equipment, their storage and testing. Classification of personal protective equipment, their storage and testing. Personal protective equipment is a device designed to protect the skin and respiratory system from exposure to toxic substances and other harmful impurities in the air that are …
Classification of personal protective equipment, their storage and testing.Далее …
Security alarm system made easy. Part I.
Security alarm system is simple. Part I. Security alarm system is simple. Part I Security alarm system is simple. Part I You open the door, the microswitch closes the power circuit of the bell. Everything is ringing, crackling, you are frantically looking for the secret power switch of the siren If you have strong nerves, …
Fire alarm voice warning systems.
Voice warning systems for fires. Fire alarm systems Fire alarm systems The effectiveness of civil defense training, as well as the activities of those responsible for the premises appointed in the pre-fire period, is low. Especially in public buildings, where in addition to the permanently working personnel there is a significant number of the public …
Foam fire extinguishing systems and other types of systems: characteristics and application.
Foam fire extinguishing installations and other types of installations: characteristics and application. Foam fire extinguishing systems and other types of systems: characteristics and application Foam fire extinguishing systems and other types of systems: characteristics and application Foam fire extinguishing systemsFoam fire extinguishing systemsare used primarily to extinguish flammable liquids and combustible liquids in tanks, flammable …
Foam fire extinguishing systems and other types of systems: characteristics and application.Далее …
Engineering monitoring.
Engineering monitoring. Engineering monitoring Engineering monitoring Engineering monitoring is the protection of various real estate objects from gas leaks, water leaks, temperature violations, monitoring the technical condition of infrastructure facilities, engineering systems. The service is provided in cooperation with emergency services, to which information about a particular emergency at the monitoring facility is transmitted. Timely …
Mechanical and electric locks in access control and management systems: Some issues of developing technical requirements.
Mechanical and electric locks in access control and management systems: Some issues of developing technical requirements. Mechanical and electric locks in access control and management systems: Some issues of developing technical requirements Mechanical and electric locks in access control and management systems: Some issues of developing technical requirements The magazine continues publishing a series of …
Fire extinguishing systems: Technical regulations on fire safety requirements.
Fire extinguishing systems: Technical regulations on fire safety requirements. Fire extinguishing systems: Technical regulations on fire safety requirements In the summer of 2009, a seminar-conference entitled «Technical Regulations on Fire Safety Requirements. Comments on Selected Provisions and the Advantages of Using Wireless Alarm Systems» was held in Moscow. The event was organized by the Main …
Fire extinguishing systems: Technical regulations on fire safety requirements.Далее …
TZ Magazine — Design of anti-terrorist protection systems: features of the regulatory framework.
Journal TZ — Design of anti-terrorist protection systems: features of the regulatory framework. Design of anti-terrorist protection systems: features of the regulatory framework Author: Alexander MALTSEV, Technical Director of Intel Tectum, PhD in Engineering When designing a facility intended for permanent or temporary stay of a large number of people, design solutions must provide technical …
Some issues of construction of fire protection systems.
Some issues of constructing fire protection systems. Some issues of constructing fire protection systems. The type of fire protection equipment used and their technical characteristics are determined by the relevant regulatory documents, GOST, NPB, etc. Specific recommendations for the use of various types of detectors for various premises are given in the Code of Practice …
Some issues of construction of fire protection systems.Далее …
Recommendations for customers.
Recommendations for customers. Recommendations for customers Recommendations for customers Author:Viktor Ilyin, Chief Engineer M+V Zander Facility Management CIS Development of optimal functional automation schemes Functional diagrams of automation are included in the executive documentation of the ACS and are the main document defining the volume and functions of the system. Functional diagrams display the technological …
New vector of the TSB market?
New vector of the TSB market?. New vector of the TSB market? Ekaterina GURYANOVA, director of the company «Protection Technologies», owner of the TZ magazine: This was not an interview in the classic sense. Slava and I have known each other for a long time, almost as long ago we switched to «you». In a …
SHAMEFUL AND SCARY.
SHAMEFUL AND SCARY. SHAMEFUL AND SCARY SHAMEFUL AND SCARY Authors: Alexander Krasnoperov, Antonina Filonenko , «Security UA» The situation in which the domestic security market has found itself can figuratively be called «revolutionary»: both the state regulator (which is also the dominant player in the market) and private security companies are almost every day are …
Question and answer. Roman Poleshchuk answers the reader's question.
Question and Answer «Tell me, are there smoke detectors that respond to cigarette smoke with a separate message, so as not to receive a fire signal on the central device, but to find out that someone is smoking in the room? — Nikolay PERMINOV, St. Petersburg» Roman POLESHCHUK, Product Manager for Bosch Security Systems, answers …
Question and answer. Roman Poleshchuk answers the reader's question.Далее …
The reader's question is answered by the general director of the company EKSOL, Stanislav ZARZHETSKY.
Stanislav ZARZHETSKY, CEO of EXOL, answers the reader's question. «In our country, a program for building data processing centers is being actively implemented in many government agencies and within large Russian corporations. Are there uniform requirements and standards for building data centers under state control? – Alexander POPOV, Khabarovsk» The reader's question is answered by …
BACnet Protocol Frequently Asked Questions.
BACnet Protocol. Frequently Asked Questions. BACnet Protocol. Frequently Asked Questions BACnet Protocol. Frequently Asked Questions BACnet Protocol. Frequently Asked QuestionsDavid FisherPolarSoft® Inc.The author of this article teaches BACnet courses in the US and is a member of the ASHRAEBACnet SSPC-135 committee What is BACnet? BACnet stands for Building Automation Control network and is a communication …
The housing and utilities reform should change attitudes towards safety.
Housing and communal services reform should change the attitude towards safety. Housing and communal services reform should change the attitude towards safety. Reforming the housing and utilities sector cannot but affect the development of technologies that ensure the safety of residential buildings. But for this to happen, the consciousness of people – end consumers – …
The housing and utilities reform should change attitudes towards safety.Далее …
Table 3. Key features of VPN tools and solutions.
Table 3. Key features of VPN tools and solutions.. Table 3. Key features of VPN tools and solutions. Table 3. Key features of VPN tools and solutions Protection tool Developer company Security Functions or Services Standards, Protocols, Formats Composition of the security system Notes IP Stream Encoder “SHIP” MO PNIEI Centralized Key Management, Authentication, Confidentiality …
Table 1. Main parameters of multichannel instrument systems for surface ships.
Table 1. Main parameters of multichannel instrument systems for surface ships. Table 1. Main parameters of multichannel instrument systems for surface ships Table 1. Main parameters of multichannel instrument systems for surface ships Country, company Model D, km 2w, deg. 2W, deg. Dl, µm FPU type, number of pixels Weight, kg Dimensions, mm U, B …
Table 1. Main parameters of multichannel instrument systems for surface ships.Далее …
Publications of the journal Special Equipment. The article was updated on 15.04 in 2023.
Publications of the journal Special Equipment. Table 1. Possibility of using technical devices generating jets of finely atomized water for fire extinguishing in the nuclear industry Name of protected premises and units Fire situation Possibility of using systems generating finely atomized liquid jets Machine room, turbogenerators, oil tanks and building structures Rapid development of fire …
Publications of the journal Special Equipment. The article was updated on 15.04 in 2023.Далее …
Features of the application of rapidly deployable security systems.
Features of using rapidly deployable security systems. Alexander Ivanovich Larin, Candidate of Technical Sciences FEATURES OF USING RAPIDLY DEPLOYABLE SECURITY SYSTEMS. The material presented to the readers' judgment is to some extent a continuation of the conversation started in the 4th issue of the magazine and is devoted to a special class of security …
Features of the application of rapidly deployable security systems.Далее …
OSCOR-5000 | Features of detection and identification of bugs using “OSCOR-5000”.
#OSCOR-5000 OSCOR-5000 BUZOV Gennady Alekseevich, Candidate of Military Sciences, Associate Professor LOBASHEV Aleksey Konstantinovich, Candidate of Technical Sciences, Associate Professor SHCHERBAKOV Dmitry Aleksandrovich FEATURES OF DETECTION AND IDENTIFICATION OF EMBED DEVICES USING OSCOR-5000” Combating unauthorized interception devices installed at protected facilities is one of the important areas of information security. Currently, the domestic market …
OSCOR-5000 | Features of detection and identification of bugs using “OSCOR-5000”.Далее …
Experience of using the nonlinear radar Nr900EK “Korshun” for searching for explosive devices.
Experience of using the nr900EK “Korshun” non-linear radar to search for explosive devices.. Experience of using the nr900EK “Korshun” non-linear radar to search for explosive devices. KALABUKHOV Viktor Anatolyevich, SHCHERBAKOV Grigory Nikolaevich, Doctor of Technical Sciences, Professor EXPERIENCE OF USING THE NR 900EK “KORSHUN” NON-LINEAR RADAR FOR SEARCHING FOR EXPLOSIVE DEVICES Introduction Currently, the …
NEW CABLE TRANSDUCER FOR SEISMOMAGNETOMETRIC DETECTION. Article updated 05.04 in 2023.
NEW CABLE CONVERTER FOR SEISMOMAGNETOMETRIC DETECTION. KHOREV Anatoly Anatolyevich, Doctor of Technical Sciences, Professor ORGANIZING INFORMATION PROTECTION FROM LEAKAGE VIA TECHNICAL CHANNELS General Provisions To the protected information refers to information that is the subject of property and is subject to protection in accordance with the requirements of legal documents or requirements established by the …
NEW CABLE TRANSDUCER FOR SEISMOMAGNETOMETRIC DETECTION. Article updated 05.04 in 2023.Далее …
Keith Melton and his spy museum. Continued. Beginning 4-5, 1998; № 1-2, 1999
Vadim Antoninovich Shelkov KIT MELTON AND HIS MUSEUM OF «SPY EQUIPMENT» (Continued. Beginning 4-5, 1998; No. 1-2, 1999) Source: «Special Equipment» magazine Assuming that our readers are exceptionally inquisitive people, we continue to introduce them to the fascinating book by American historian and collector Keith Melton “The Ultimate Spy Book” and the exhibits of his …
Keith Melton and his spy museum. Continued. Beginning 4-5, 1998; № 1-2, 1999Далее …
Device “BIOTOX-10”. Environmental control: problems and solutions.
ENVIRONMENTAL CONTROL: PROBLEMS AND SOLUTIONS. DEVICE “BIOTOX-10” Certificate of the State Committee of the Russian Federation for Standardization and Metrology (Gosstandart of Russia), No. 9842 Environmental problems caused by the negative impact of humans on the environment are increasingly taking first place in sociological surveys. These problems are associated with such factors as emissions …
Device “BIOTOX-10”. Environmental control: problems and solutions.Далее …
Past and thoughts.
Past and Thoughts. Past and Thoughts The title of the article is in no way a claim to the glory of Alexander Ivanovich Herzen — it is just a coincidence. «Protection Technologies» is the name of the magazine and the focus of the materials published in it. But there are not only technologies for protection …
ZigBee protects firefighters.
ZigBee protects firefighters. The system was developed at the University of Berkeley (California) at the request of fire departments after the events of September 11, 2001, when rescuers working in the Twin Towers were forced to use incompatible dual-channel radio systems that did not allow them to communicate with each other. The Fire Information and …
Wind power plants of NPP Enexis.
Wind power plants «NPP Eneksis». In 1993, specialists from the US Electric Power Research Institute assumed that in the next 10-12 years, wind would produce cheaper energy compared to any other resources». Today, this prediction is beginning to come true. A wind power plant is a wind power plant that converts the kinetic energy of …
TSU9600 – Designed by installers, manufactured by PHILIPS.
TSU9600 – Designed by installers, manufactured by PHILIPS. TSU9600 – Designed by installers, manufactured by PHILIPS TSU9600 – Designed by installers, manufactured by PHILIPS TSU9600 – Designed by installers, manufactured Everything a user could want… The original Philips Pronto single-handedly created a new class of programmable touchscreen remote controls with an intuitive interface. Today, the …
TSU9600 – Designed by installers, manufactured by PHILIPS.Далее …
Highly reliable fire-resistant insulating flange seals.
Highly reliable fire-resistant insulating flange seals. Highly reliable fire-resistant insulating flange seals Highly reliable fire-resistant insulating flange seals It can only be added that the more severe the conditions in which the seal operates, the greater the likelihood of its damage and the more serious the consequences. And in this context, in our opinion, of …
Highly reliable fire-resistant insulating flange seals.Далее …
With athletic steps.
With sporty steps. Sports steps Sports steps The World Ice Hockey Championships in Moscow, the run-up to the 2014 Olympics and the related development of sports infrastructure in Sochi – all these events confirm that the trend of building sports facilities in Russia will continue in the near future. We have tried to understand the …
Oleg Zimenkov: Intelligent systems account for up to 50% of construction costs.
Oleg Zimenkov: Intelligent systems account for up to 50% of construction costs. Oleg Zimenkov: Intelligent systems account for up to 50% of construction costs Oleg Zimenkov: Intelligent systems account for up to 50% of construction costs Oleg Zimenkov, First Deputy General Director of Optima-Integration, answers CNews questions. CNews: What trends characterize the Russian market of …
Oleg Zimenkov: Intelligent systems account for up to 50% of construction costs.Далее …
Nikolay Koshman: the way out of the current situation is self-regulation.
Nikolai Koshman: the way out of the current situation is self-regulation. Nikolay Koshman: the way out of the current situation is self-regulation Nikolay Koshman: the way out of the current situation is self-regulation The Association of Builders of Russia (ABR) will celebrate its 2nd anniversary in June 2007. ABR was formed by large and medium-sized …
Nikolay Koshman: the way out of the current situation is self-regulation.Далее …
Konstantin Pulikovsky: Supervision must be unified.
Konstantin Pulikovsky: Supervision must be unified. – Konstantin Borisovich, what powers in the field of construction of residential and commercial buildings are currently assigned to your department? – The government of the country instructed Rostekhnadzor to carry out state construction supervision from February 1, 2006. After the Urban Development Code of the Russian Federation came …
I.LON100e3 – The idea is taking over the world!
i.LON100e3 – The idea takes over the World!. i.LON100e3 – The idea is taking over the World! i.LON100e3 – The idea takes over the World! It all started with a new hardware platform and a brand new technology called XML Extended Markup Language. This technology was created by members of the W3C (World Wide Web …
GSM alarm system – for self-confident people.
Every happy owner of a cottage or a richly furnished apartment has probably thought about how to make their property protected from thieves and other criminals. Unfortunately, an ordinary alarm does not give the desired effect. Sometimes the alarm does not have any effect on intruders. As a result, the owners find themselves in a …
Investments. Construction. Real estate – 2007.
#exhibitions, #investments, #real estate, #construction Participation in the XII International Exhibition “Investments. Construction. Real Estate – 2007. For the first time, Konti presented to visitors of the exhibition a model of one of the lanehouse ensembles almost in life-size.Everyone was able to evaluate what the new project is and what its main advantages are compared …
TechnoLink wireless system.
TechnoLink wireless system. TechnoLink is an integrated wireless radio solution that complements the wide range of Kieback&Peter developments in the field of building automation. TechnoLink indoor and outdoor temperature telemetry sensors, humidity sensors and room control devices are based on solar-powered wireless technology. During the dark period, the devices are supplied with energy from built-in …
BAS
Network-based BAS provide easier remote access to control functions for various building systems for operators of these systems and building managers. Interview participants: Carl Lundstrom, Engineer, Certified Software Engineer, Vice President of Utility Systems at EMC Engineers, Atlanta, USA. Steve Tom, Director of Technical Information at Automated Logic Corporation, Kenneesaw, Georgia, USA. Bruce Westphal (Bruce …
On the standardization of information and communication systems of buildings and structures of educational institutions.
On the standardization of information and communication systems of buildings and structures of educational institutions. The current state and prospects for ensuring the development and safety of educational facilities based on the standardization of information and communication systems are considered. Issues of development and application of international and national standards are highlighted using the example …
Penthouse is a new lifestyle of the Russian elite.
Penthouse is a new lifestyle of the Russian elite. The ideal is unattainable, but we must strive for it. Whatever one may say, automation is an expensive business. Automation in all its glory, I mean, and not an attempt to build a super with a skinny wallet and stinginess of the customer, or, even worse, …
LON-LAN-WAN. Open control systems and convergence of data networks.
LON-LAN-WAN. Open control systems and convergence of data networks. Convergence of data networks can most effectively be achieved through open management systems; integration plays a key role in the process of information exchange. Before describing the convergence of LON, LAN and WAN technologies, it is worth defining the differences between closed and open systems. Closed …
LON-LAN-WAN. Open control systems and convergence of data networks.Далее …
Cisco EnergyWise improves the sustainability of all networked devices.
Cisco EnergyWise solution improves the environmental friendliness of all network devices. Cisco announced innovative Cisco EnergyWise technology for Cisco Catalyst® switches. This technology measures, monitors and reduces the power consumption of IP devices such as IP phones, mobile computers and wireless access points. Additionally, Cisco announced new partnerships and announced the acquisition of Richards-Zeta Building …
Cisco EnergyWise improves the sustainability of all networked devices.Далее …
Fiber-optic systems for technical monitoring of construction structures.
Fiber-optic systems for technical monitoring of construction structures. Authors: Egorov F.A., Ph.D. physics and mathematics sciences; Pospelov V.I., Ph.D. technical sciences; Bykovsky V.A.; Neugodnikov A.P. In parallel with the rapid growth of construction technologies, the business sector represented by companies that specialize in automation of building management is actively expanding. At the same time, the …
Fiber-optic systems for technical monitoring of construction structures.Далее …
Trends in the development of data transmission technologies and their practical application.
Trends in the development of data transmission technologies and their practical application. Like any system, a security system is a complex consisting of a set of both subsystems and the principles of their application. The main subsystems used are: Means of physical counteraction to intrusion into a security facility (lock, fence, door, etc.). Means of …
Trends in the development of data transmission technologies and their practical application.Далее …
The Security Technologies Forum is a world-famous brand.
Security Technologies Forum is a world-famous brand. From February 5 to 8, Crocus Expo will host the XIII Forum “Security Technologies” — a global international exhibition project that entered the network of world security exhibitions in 2007 g. This year the Security Technologies project turns 13 years old. All this time, it has been growing …
The Security Technologies Forum is a world-famous brand.Далее …
IFSEC-2009.
IFSEC-2009. I would like to start this detailed announcement with a very significant figure: IFSEC-2008, let us remind you that it was the 35th anniversary exhibition, we visited 30,257 people from 125 countries. This year, one of the most famous security exhibitions is again taking place at the exhibition center in Birmingham (UK). Dates: May …
Mips 2009: 15 years together.
Mips 2009: 15 years together. There is very little time left until one of the most anticipated annual industry events in Russia. Soon MIPS 2009 will hospitably open its doors. This year is special for everyone: the oldest Moscow security exhibition will be held for the 15th time. Already the first MIPS exhibition, which was …
IFSEC-2010 is the largest event in the global security industry.
IFSEC-2010 is the largest event in the global security industry. IFSEC-2010 — The largest event in the global security industry. The largest international exhibition dedicated to current security issues will be held from May 10 to 13 at the NEC exhibition center in Birmingham (UK). The exhibition will once again become not only a demonstration …
IFSEC-2010 is the largest event in the global security industry.Далее …