List of articles
Wireless networks: current status and prospects.
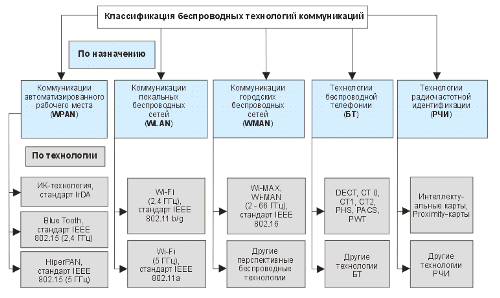
Wireless Networks: CURRENT STATE AND PROSPECTS RadioEthernet wireless network equipment is becoming increasingly widespread in Russia and the CIS countries for organizing local networks, connecting to the Internet and connecting remote networks and individual computers over long distances. Currently, the bulk of radio equipment is manufactured in accordance with the IEEE 802.11 «Wireless LAN Medium …
Wireless communications
The world is so arranged that any technical invention of the human mind that expands our capabilities and creates additional comfort for us inevitably contains negative aspects that can pose a potential danger to the user. Modern means of wireless personal communication are no exception in this regard. Yes, they have expanded our freedom immeasurably, …
The latest in wireless technology.
Wireless technologies of the last inch. UKOV Vyacheslav Sergeevich, Candidate of Technical Sciences PONOMAREV Andrey Alekseevich The problem of the so-called “last mile” in information transmission systems has long attracted the attention of specialists: how to reliably deliver information to the user at the last, usually most difficult stage of delivery. With the active development …
Local Area Network Security
It is extremely important to understand that security is not a product that you can buy in a store and be confident in your own protection. «Security» is a special combination of both technical and administrative measures. Administrative measures also include not only papers, recommendations, instructions, but also people. It is impossible to consider your …
Security of fiber optic cable systems.
When network system providers are asked about possible solutions, they briskly answer: «If you need security, use fiber optics.» At first glance, everything is obvious. Fiber optics are ordinary glass that transmits electromagnetic energy in the form of infrared light. There is practically no radiation to the outside. The message can only be intercepted by …
Cell phone blocker RS Jammer.
RS jammer cell phone blocker. RS jammer cell phone blocker RS jammer cell phone blocker Potentially, a cell phone is a ready-made eavesdropping device that transmits information via a cellular system traffic channel. Special technical means are also produced that use the transmission of information in a GSM standard traffic channel. These eavesdropping devices …
Bulletproof vests. Protection classes. GOST, DIN, NIJ, CEN..
Body armor. Protection classes. GOST, DIN, NIJ, CEN. Source: NPO Special Materials GOST, DIN, NIJ, CEN Ballistic requirements for body armor for the armed forces and police are mainly established by state standards (for example, the standard of the German Police Department, the National Institute of Justice, etc.). In Russia, they were developed with the …
Bulletproof vests. Protection classes. GOST, DIN, NIJ, CEN..Далее …
Bulletproof vest, its purpose and capabilities.
Body armor, its purpose and capabilities. This popular product has saved more than one thousand human lives, but it has also killed many people who believed in the miraculous invulnerability of body armor. Today, dozens of their manufacturers and hundreds of sellers promise you complete comfort and protection from all types of weapons, frankly lying, …
Paper for secret documents with security marks and the method of its production.
Paper for secret documents with security marks and the method of its manufacture. Paper for secret documents with security marks and the method of its manufacture. Patent. 2705107 France, IPC D21H 21/48. — Published. 11/18/94. Paper for secret documents with security marks and the method of its manufacture. There are various methods of protecting secret …
Paper for secret documents with security marks and the method of its production.Далее …
CDMA without secrets.
CDMA without secrets. CDMA without secrets CDMA without secrets There is an opinion among communications specialists that the «era of great radio engineering discoveries» ended happily a hundred years ago. The first and only discovery was the very fact of the invention of radio in 1895. All subsequent achievements are associated exclusively with progress in …
Prices, availability and purchasing procedures for Kaiser products.
Prices, availability and procedure for purchasing Kaiser products. Kaiser Product Pricing, Availability, and Purchase Procedures Seller Granit Island Group, Manufacturer Martin L. Keiser, Inc. James M. Atkinson, Granite Island Group Kaiser Product Pricing and Purchase Procedures Basic Countermeasure Equipment. Product Number Product Description Estimated delivery time after payment (in months) Product price in US$ (net) …
Prices, availability and purchasing procedures for Kaiser products.Далее …
Frequency distribution for Moscow.
Frequency distribution in Moscow. 1. RADIO STATIONS AND TELEVISION
What is a vocoder and lipreader?
What is a vocoder and a lipreader? What is a vocoder and a lipreader? What is a vocoder and a lipreader? Proceedings of the 2nd All-Russian Conference «Theory and Practice of Speech Research» In modern digital systems for recording, transmitting and storing speech information, various speech compression methods are used to reduce the volume occupied …
Digital processing of images of dynamic spectrograms of audio signals in problems of voice communication security.
Digital processing of images of dynamic spectrograms of audio signals in the problems of voice communication security.. Digital processing of images of dynamic spectrograms of audio signals in the problems of voice communication security. Dvoryankin Sergey Vladimirovich, Candidate of Technical Sciences DIGITAL PROCESSING OF IMAGES OF DYNAMIC SPECTROGRAMS OF AUDIO SIGNALS IN VOICE COMMUNICATION SECURITY …
Computer equipment. Protection from unauthorized access to information.
Computer equipment. Protection against unauthorized access to information. Indicators of protection against unauthorized access to information. Guidance document. This Guidance document establishes the classification of computer equipment by the level of protection against unauthorized access to information based on a list of security indicators and a set of requirements describing them. Computer equipment is understood …
Computer equipment. Protection from unauthorized access to information.Далее …
Further development of technologies for searching for explosives and explosive objects in open areas, transport facilities and transport infrastructure.
Further development of technologies for searching explosives and explosive objects in open areas, transport facilities and transport infrastructure. Further development of technologies for searching explosives and explosive objects in open areas, transport facilities and transport infrastructure. Further development of technologies for searching for explosives and explosive objects in open areas, transport facilities and transport infrastructure …
Security alarm sensors
#alarm Sensors are the main component of the security alarm system and largely determine the reliability of the entire system. An analysis of the range of security alarm sensors offered by the largest manufacturers of security alarm systems, as well as those presented at recent exhibitions, shows that the most popular sensors for protecting premises …
Delta Telecom has implemented SIS.
Delta Telecom has implemented SIS. Delta Telecom has implemented SIS «Delta Telecom» has implemented SIS Delta Telecom is the first cellular company in the world operating according to the NMT 450 standard, which has fully implemented the cellular authentication system (SIS) to protect against unauthorized connection to the network. Delta Telecom began its operations in …
Explosives Detectors. Summary Table..
Explosives detectors. Summary table.. Explosives detectors. Summary table. Explosives detectors. Summary table. Item No. Name, manufacturer Detectable substances, sensitivity Note 1 EVD-3000, IDS Most military and civilian explosives (C-4, TNT (dynamite), PETN, Semtex, EGDN, DMNB, RDX (RDX and nitrates), EGMN and nitroglycerin) Sensitivity: in the range of 2-20 ng. (powder and vapor) Advantages: Fully …
The lie detector is not about technology.
A lie detector is not about technology. A lie detector is not about technology. A lie detector is not about technology. Alexander Strunin Nowadays, not only the level of professional training, but also the moral and psychological characteristics, ethical standards, and cultural values of a person play an important role in assessing the compliance …
Itemiser Contraband Detector Explosives and Drugs Detector.
Itemiser Contraband Detector, an explosive and drug detector. Itemiser Contraband Detector, an explosive and drug detector. Aviation Week & Space Technology.- 1996 .- 145, No. 5 — P. 66. Itemiser Contraband Detector Ion Track Intruments (USA) has developed an improved detector of explosives, drugs and other contraband goodsItemiser Contraband Detector. It can search a passenger …
Itemiser Contraband Detector Explosives and Drugs Detector.Далее …
DMR is a new radio communication standard.
DMR is a new radio communication standard. DMR is a new radio communication standard. CHIVILEV Sergey Vladimirovich, Candidate of Technical Sciences DMR is a new radio communication standard. Source: «Special Equipment» magazine. No. 2 2008 The main consumers of DMR-based systems, as well as conventional (analog) radio communication systems, are enterprises of the lower and …
US Dollars..
US dollars.. US dollars. US dollars. Shaposhnikov Yu.I. Source: US dollars are the currency of the United States of America and are non-convertible US treasury notes. The first US bank notes (UNITED STATES NOTE) were issued during the Civil War (1861-1865) to finance military expenses. They received their slang names «greens», «bucks» and «greenbacks» because …
Inspection system for detection of explosives and narcotics.
Inspection system for detecting explosives and narcotics. In recent years, there has been a continuous increase in the use of explosives (HE) and drug smuggling by terrorists and other criminal elements. It is almost impossible to detect and prevent such illegal actions. However, there are areas of increased control taking into account vulnerable places where …
Inspection system for detection of explosives and narcotics.Далее …
Soul in computer networks.
Soul in computer networks. Soul in computer networks «Soul in computer networks» Komsomolskaya Pravda, No. 182 10/06/1995 For the first time in the history of mankind, it has become possible to penetrate the subconscious with the help of a computer. A group of Moscow scientists has developed and is already practicing a new method that …
Economic security — in the hands of professionals.
Put economic security in the hands of professionals. Put economic security in the hands of professionals Put economic security in the hands of professionals The 1990s have shown that force methods have become a permanent and necessary element of economic life in the Russian economy. Over the past 10 years, professional law enforcement agencies have …
Shielding of electromagnetic waves.
Shielding of electromagnetic waves. Shielding of electromagnetic waves Shielding of electromagnetic waves Shielding of electromagnetic waves is the basis of environmental safety and one of the most effective means of protecting an object from information leakage through technical channels. In the absence of the necessary literature on the issue under consideration, this article and the …
Expert practice..
Expert practice.. Expert practice. Expert practice Forensic examination of sound recordings. Experts: Ivanov I.L., Popova A.R. Characteristic questions of the examination: 1. Was the phonogram presented for examination recorded on a Panasonic…..» voice recorder? (which was also presented for examination) 2. Is the magnetic phonogram presented for examination an original? 3.Are there …
Expert study of the GSM format.
Expert examination of the GSM format. Expert examination of the GSM format. Expert examination of the GSM format. Examination of phonograms for the presence/absence of signs of editing or changes made during or after recording is one of the main diagnostic tasks of forensic phonography. For example, we will use a simple scheme for presenting …
Expert study of the parameters of the distribution of the CHOT.
Expert study of the parameters of the distribution of the NFC. Expert study of the parameters of the distribution of the NFC Expert study of the parameters of the distribution of the NFC Ivanov I.L. Orel (Manual for experts of the system of expert institutions of the Ministry of Justice of the Russian Federation (SEI …
Expert study of the parameters of the distribution of the CHOT.Далее …
Express analysis of the authenticity of special and excise stamps of the 2006 model.
Express analysis of the authenticity of special and excise stamps of the 2006 model. Express analysis of the authenticity of special and excise stamps of the 2006 model. Express analysis of the authenticity of special and excise stamps of the 2006 model. Source: Ultramag-S6VM Ul Tramag-A14M Ultramag-A36 This reference and methodological manual on express analysis …
Express analysis of the authenticity of special and excise stamps of the 2006 model.Далее …
Electronic identification methods.
Electronic identification methods. Electronic identification methods. Electronic identification methods. Electronic methods of human identification, used in systems for ensuring authorized access to protected areas of the territory, as well as to material and information resources, are currently widespread. The article discusses the design features of various identification methods, information about which was obtained from various …
The Era of Night Warfare. Review of the International Market of Night Vision Devices.
The era of night warfare. Review of the international market of night vision devices.. The era of night warfare. Review of the international market of night vision devices. Salikov Vyacheslav Lvovich THE ERA OF NIGHT WAR. Review of the international market of night vision devices. Source: magazine «Special Equipment» In the article devoted to the …
The Era of Night Warfare. Review of the International Market of Night Vision Devices.Далее …
More about the eight-story microphone.
More about the eight-story microphone. More about the eight-story microphone More about the «eight-story microphone». The article «The story of the «eight-story microphone». Fiction or reality» contains a number of controversial points, which may have been a consequence of the limited volume of the publication and the authors' attempt to popularize the material presented. Thus, …
Once again about “steganography” – the most modern of the ancient sciences.
Once again about “steganography” – the most modern of the ancient sciences.. Once again about “steganography” – the most modern of the ancient sciences. UKOV Vyacheslav Sergeevich, Candidate of Technical Sciences Shuvalov Aleksey Viktorovich ONCE AGAIN ABOUT “STEGANOGRAPHY THE MOST MODERN OF THE ANCIENT SCIENCES Some modern possibilities of using computer steganography to solve …
Once again about “steganography” – the most modern of the ancient sciences.Далее …
Federal Law on Operational Investigative Activities No. 144-F3.
Federal Law on Operational — Investigative Activities N 144-F3. Federal Law on Operational — Investigative Activities N 144-F3 RUSSIAN FEDERATION FEDERAL LAW ON OPERATIONAL — SEARCH ACTIVITIES» N 144-FZ Adopted by the State Duma July 5, 1995 (as amended by Federal Law of July 18, 1997 N 101-FZ) This Federal Law defines the content of …
Federal Law on Operational Investigative Activities No. 144-F3.Далее …
Federal Law of 10.01.96 N 5-FZ On Foreign Intelligence.
Federal Law of 10.01.96 N 5-FZ On Foreign Intelligence. Federal Law of 10.01.96 N 5-FZ On Foreign Intelligence FEDERAL LAW OF 10.01.96 N 5-FZ » ON FOREIGN INTELLIGENCE « Article 6. Powers of the Foreign Intelligence Agencies of the Russian Federation In order to achieve the goals of intelligence activities, the foreign intelligence agencies of …
Federal Law of 10.01.96 N 5-FZ On Foreign Intelligence.Далее …
Federal Law of February 20, 1995 N 24-FZ On information, informatization and information protection.
Federal Law of February 20, 1995 N 24-FZ On information, informatization and information protection. Federal Law of February 20, 1995 N 24-FZ On Information, Informatization, and Information Protection Federal Law of February 20, 1995 N 24-FZ «On Information, Informatization, and Information Protection» Adopted by the State Duma on January 25, 1995 Chapter 1. General Provisions …
Federal Law of the Russian Federation «On Communications». Part 1
Federal Law of the Russian Federation «On Communications». RUSSIAN FEDERATION FEDERAL LAW N 15-FZ «On Communications» Adopted by the State Duma on January 20, 1995 This Federal Law establishes the legal basis for activities in the field of communications carried out under the jurisdiction of the Russian Federation (federal communications, hereinafter referred to as …
Federal Law of the Russian Federation «On Communications». Part 1Далее …
Photo camera of the rolling of Alycha.
Camera rolling Cherry plum. Camera rolling cherry plum Camera rolling «Cherry plum& #187; 1959 — 60 In the 50s, one of the most original Soviet cameras, the «Alycha», was developed and released for copying documents using contact scanning or optical scanning across the frame — this is what this type of photography was called in …
Functional capabilities of the FPSU-IP complexes.
Functional capabilities of the FPSU-IP complexes. Functional capabilities of the FPSU-IP complexes Functional capabilities of the FPSU-IP complexes The main functional capabilities of the FPSU-1R complexes are: • filtering IP packets based on the criteria of compliance with the main «RFC Recommendations for IP Networks»: address validity, size correlation, checksum correctness, etc.; • IP packet …
Minotaur is a flexible, scalable security system for personal computers.
Flexible scalable Minotaur security system for personal computers. Flexible scalable Minotaur security system for personal computers. Signal- 1995 .-50, №2-P. 29-31 Flexible scalable Minotaur security system for personal computers Developed by Lockheed Martin (USA) new security system for personal computers Minotaur(«Minotaur») performs a wide range of functions — from boot protection to highly reprogrammable cryptographic …
Minotaur is a flexible, scalable security system for personal computers.Далее …
ANTHEM OF THE EXPLOSIVE EXPERTS.
ANTHEM OF EXPLOSIVE EXPERTS. EXPLOSION EXPERTS' ANTHEM Words by A.Yu. Semenov EXPLOSION EXPERTS' ANTHEM Here's a grenade lying on the table, We need to disassemble it, But we want to live so much, guys, However, we must begin. The fuse has worked, that's the concern, There are about three seconds left to live, That will …
State Standard of the Russian Federation. GOST No. 34.11-94
State Standard of the Russian Federation. GOST No. 34.11-94 Information technology. Cryptographic protection of information. Caching function. STATE STANDARD OF THE RUSSIAN FEDERATION GOST No. 34.11-94 Information technology. Cryptographic protection of information. Caching function. Date of introduction 01/01/95 KGS code P85 Code OKSTU 5002 GRNTI rubricator index 5041 OKS Code 35.040, 35.060, 35.080, 35.100, 35.140, …
State Standard of the Russian Federation. GOST No. 34.11-94Далее …
State Standard of the Russian Federation. GOST No. 50739-95 Computer equipment.
State Standard of the Russian Federation. GOST No. 50739-95 Computer equipment. Protection against unauthorized access to information. General technical requirements. Date of introduction 01/01/96 KGS code P85 OKSTU code 4002 GRNTI rubricator index 500105 OKS code 35.020 Type of standard. Type of requirements Document is marked * Preface 1 Developed and submitted by the Research …
State Standard of the Russian Federation. GOST No. 50739-95 Computer equipment.Далее …
State Standard of the USSR GOST 28147-89
USSR State Standard GOST 28147-89 Information processing systems. Cryptographic protection. Cryptographic transformation algorithm. Date of entry into force 07/01/90 KGS code: П85 OKSTU code: 5017 GRNTI rubricator index: 500509 OKS code: 35.040, 35.060, 35.080, 35.100, 35.140, 35.240 Type of standard: Fundamental standards Type of requirements: The document is marked * The indicators of this ND …
State Standard of the USSR GOST No. 3410-94
USSR State Standard GOST No. 3410-94. Information technology. Cryptographic protection of information. Procedures for generating and verifying an electronic digital signature based on an asymmetric cryptographic algorithm. STATE STANDARD OF THE RUSSIAN FEDERATION GOST No. 3410-94 Information technology. Cryptographic protection of information. Procedures for generating and verifying an electronic digital signature based on an asymmetric …
GSM: the security of your information.
GSM: the security of your information. GSM: the security of your information GSM: the security of your information Customers can rest assured that the security mechanisms adopted in the GSM standard ensure the confidentiality of conversations and subscriber authentication and prevent unauthorized access to the network. Radio communication is inherently more vulnerable to wiretapping and …
State Customs Committee under the President of the Russian Federation. Regulations on the state system of information protection in the Russian Federation from foreign technical intelligence services and from its leakage through technical channels.
State Customs Committee under the President of the Russian Federation. Regulations On the state system of information protection in the Russian Federation from foreign technical intelligence services and from its leakage through technical channels. State Customs Committee under the President of the Russian Federation. Regulations On the state system of information protection in the Russian …
IDENTIFICATION, AUTHENTICATION…LOYALTY!..
IDENTIFICATION, AUTHENTICATION…LOYALTY!.. IDENTIFICATION, AUTHENTICATION…LOYALTY!. IVANOV Vitaly Viktorovich IDENTIFICATION, AUTHENTICATION…LOYALTY! The work examines one of the promising areas of development of access control systems, related to checking the loyalty of enterprise personnel. In the modern world, there is a constant increase in threats to enterprise security. In the broadest sense, threats can be divided into external, …
Identification of users of computing systems.
Identification of users of computing systems. Identification of users of computing systems Identification of users of computing systems based on modern speech technologies In connection with the increased informatization of modern society and the increase in the number of objects and information flows that need to be protected from unauthorized access, as well as the …
Means of indicating narcotic substances.
Narcotic substance indicator devices. The fight against illegal drug trafficking (sometimes abbreviated as «NV») has recently rapidly transformed from a social and public problem into a problem of ensuring the national security of the Russian Federation. The reduction in the cost of a dose of heroin to the price of a bottle of vodka has …
Inductive devices for organizing hidden radio communications.
Inductive devices for organizing covert radio communications.. Inductive devices for organizing covert radio communications. Ovchinnikov Andrey Mikhailovich, Archagov Oleg Igorevich INDUCTIVE DEVICES FOR ORGANIZING COVERT RADIO COMMUNICATION In the practice of security services and various security structures, it is often necessary to use radio communications in an unnoticeable manner for others (ensuring visual and acoustic …
Inductive devices for organizing hidden radio communications.Далее …
Information letter on conducting psycho-physiological examinations.
Information letter On conducting psycho-physiological examinations. Information letter On conducting psycho-physiological examinations. Moscow City Prosecutor's Office INFORMATION LETTER “On conducting psycho-physiological examinations” The intensification of the fight against crime, as well as the protection of the interests of law-abiding citizens involved in criminal proceedings, against the background of a decrease in the value of evidentiary …
Information letter on conducting psycho-physiological examinations.Далее …
Infrared laser spotlights.
Infrared laser projectors. ARKHUTIK Stepan Trofimovich, VOLKOV Viktor Genrikhovich, Candidate of Technical Sciences, Associate Professor KOZLOV Konstantin Valerievich SALIKOV Vyacheslav Lvovich UKRAINSKY Sergey Alekseevich INFRARED LASER PROJECTORS The night vision device (NVD) must operate not only in passive mode, but also in active mode with floodlight illumination to ensure the required range in particularly dark …
Tools for carrying out attacks on Microsoft OS.
Tools for carrying out attacks on Microsoft OS. Tools for carrying out attacks on Microsoft OS Tools for carrying out attacks on Microsoft OS This work is an attempt to analyze the vulnerabilities of network operating systems Windows 95/98 NT from Microsoft. The article discusses the main methods and some common tools of influence that …
Internet telephony.
Internet telephony. Internet telephony Internet telephony Over the past few years, the world has seen a rapid increase in the number of Internet users. Its popularity is due to a wide range of services and capabilities: e-mail (E-mail), the World Wide Web (WWW), network conferences (NNTP), voice mail, Internet Telephony (IT), and others. This article …
USE OF WIRELESS COMMUNICATION IN GEOGRAPHICALLY DISTRIBUTED SYSTEMS FOR COLLECTING AND PROCESSING INFORMATION.
USE OF WIRELESS COMMUNICATION IN GEOGRAPHICALLY DISTRIBUTED SYSTEMS OF INFORMATION COLLECTION AND PROCESSING.. USE OF WIRELESS COMMUNICATION IN GEOGRAPHICALLY DISTRIBUTED SYSTEMS OF INFORMATION COLLECTION AND PROCESSING. IVANOV Vitaly Viktorovich USE OF WIRELESS COMMUNICATION IN TERRITORIALLY DISTRIBUTED SYSTEMS OF INFORMATION COLLECTION AND PROCESSING The article considers the issue of using modern wireless communication technologies to build …
Using digital watermarks to combat insiders.
Using digital watermarks to combat insiders. Using digital watermarks to combat insiders TERENIN Aleksey Alekseevich, Candidate of Technical Sciences MELNIKOV Yury Nikolaevich, Doctor of Technical Sciences, Professor POGULYAYEV Vadim Vladimirovich Using digital watermarks to combat insiders Source: magazine «Special Equipment» No. 1 2008 Information technologies are becoming increasingly important for successful business. After all, with …
Using a mobile NQR detector with a mini-helicopter.
Using a mobile NQR detector with a mini-helicopter.. Using a mobile NQR detector with a mini-helicopter. GRECHISHKIN Vadim Sergeevich, Doctor of Physical and Mathematical Sciences, Professor USE OF A MOBILE NQR DETECTOR USING A MINI-HELICOPTER The article discusses an improved NQR mine detection system, characterized by increased phase stability and designed to detect NQR …
Using backscattered ionizing radiation to control objects.
Using backscattered ionizing radiation to monitor objects. Boris Aleksandrovich Vandyshev, Candidate of Technical Sciences USE OF BACKSCATTERED IONIZING RADIATION TO MONITOR OBJECTS The article discusses some types of inspection equipment, the operating principle of which is based on the use of ionizing radiation reflected from contraband items, called backscattered ionizing radiation. This principle allows you …
Using backscattered ionizing radiation to control objects.Далее …
Use of the polygraph in the interests of the state and commercial security.
Using a polygraph in the interests of the state and commercial security. (based on publications by Yu.I.Kholodny, V.V.Korovina, V.A.Varlamov, O.V.Belyushina, A.A.Stepanov and others) Polygraph (lie detector). History and modern times. With this article we would like to begin a series of publications on the problem of the polygraph, or in common parlance, the «lie detector». …
Use of the polygraph in the interests of the state and commercial security.Далее …
The Use of the Polygraph in the Interests of U.S. Commercial Security.
#Polygraph Using the Polygraph in the Interests of US Commercial Security. Michael Allenson Lafayette Inst. I would like to briefly discuss how the polygraph has been used for commercial security purposes in the past, what has changed since the introduction of the Employee Polygraph Protection Act (EPPA), and how the polygraph is currently used in …
The Use of the Polygraph in the Interests of U.S. Commercial Security.Далее …
Use of the polygraph in Russia.
#Polygraph Use of polygraph in Russia. V. M. Gladyshev, Head of the Federal Center of the FSB of Russia for Licensing and Protection of State Secrets A. V. Fesenko, Doctor of Technical Sciences, Professor K. I. Kholodny, Chairman of the Qualification and Methodological Commission of the Russian Association «Polygraph», Candidate of Psychological Sciences The Government …
Using radio monitoring to identify threats.
Using radio monitoring to identify threats. Vorobyov Sergey Viktorovich USE OF RADIO MONITORING TO IDENTIFY THREAT The article discusses the use of radio monitoring to detect the preparation of a threat. The characteristics of its effectiveness are assessed, recommendations for practical application are given. It is known that any major legal or illegal actions are …
Using radio-absorbing materials to protect ground penetrating radar from electromagnetic interference.
Using radio-absorbing materials to protect ground penetrating radar from electromagnetic interference.. Using radio-absorbing materials to protect ground penetrating radar from electromagnetic interference. GORBATENKO Olga Nikolaevna, BIBIKOV Sergey Borisovich, Candidate of Physical and Mathematical Sciences USE OF RADIO-ABSORBING — RADIO-SCATTERING MATERIALS FOR PROTECTING GEORADAR FROM ELECTROMAGNETIC INTERFERENCE The problem of shielding the OKO-M1 type georadar in …
Examination of phonograms for the presence/absence of signs of editing as a task of expert diagnostics.
Examination of phonograms for the presence/absence of signs of editing as a task of expert diagnostics. Examination of phonograms for the presence/absence of signs of editing as a task of expert diagnostics. Examination of phonograms for the presence/absence of signs of editing as a task of expert diagnostics The examination of phonograms for the presence/absence …
Study of the continuity of the harmonic phase at the Nyquist frequency, search for stable features of digital voice recorders.
Study of the continuity of the phase of harmonics at the Nyquist frequency, search for stable features of digital voice recorders.. Study of the continuity of the phase of harmonics at the Nyquist frequency, search for stable features of digital voice recorders. Ivanov I.L. Orel Study of the continuity of the harmonic phase at the …
Study of the tactical and technical characteristics of the walk-through multi-zone metal detector Intelliscan 12000.
Study of the tactical and technical characteristics of the Intelliscan 12000 walk-through multi-zone metal detector. Study of the tactical and technical characteristics of the Intelliscan 12000 walk-through multi-zone metal detector. Material received in April 1999. STUDY OF THE TACTICAL AND TECHNICAL CHARACTERISTICS of a walk-through multi-zone metal detector «Intelliscan 12000» The purpose of this study …
Study of the tactical and technical characteristics of the programmable metal detector PMD 1.
Study of the tactical and technical characteristics of the programmable metal detector PMD 1. Study of the tactical and technical characteristics of the programmable metal detector PMD 1 Material received in April 1999. STUDY OF TACTICAL AND TECHNICAL CHARACTERISTICSprogrammable metal detector «PMD 1» The purpose of this study was to determine the probabilistic characteristics of …
Study of the tactical and technical characteristics of the programmable metal detector PMD 1.Далее …
Study of tactical and technical characteristics of the Metor-200 walk-through multi-zone metal detector.
Study of the tactical and technical characteristics of the Metor-200 walk-through multi-zone metal detector. Study of the tactical and technical characteristics of the Metor-200 walk-through multi-zone metal detector Material received in April 1999. STUDY OF THE TACTICAL AND TECHNICAL CHARACTERISTICS of the Metor-200 walk-through multi-zone metal detector The purpose of this study was to determine …
Study of the tactical and technical characteristics of the Shakhta-U selective weapon detector.
Study of the tactical and technical characteristics of the Shakhta-U selective weapon detector. Study of the tactical and technical characteristics of the Shakhta-U selective weapon detector Material received in April 1999. STUDY OF THE TACTICAL AND TECHNICAL CHARACTERISTICS of the Shakhta-U selective weapon detector The aim of the present research was to determine the probabilistic …
Power supplies for radio monitoring equipment.
Power supplies for radio monitoring equipment.. Power supplies for radio monitoring equipment. BELYAKOV Andrey Leonidovich, GLADKIKH Aleksandr Viktorovich POWER SUPPLIES FOR RADIO CONTROL EQUIPMENT The options for power supply of radio monitoring equipment, its features in terms of meeting the requirements of electromagnetic compatibility with power sources, as well as the possibility and necessity …
History of microdot
#microdot Vadim Antonovich Shelkov HISTORY OF «MICRODOTS» I would like to express my sincere gratitude to Keith Melton, the creator and curator of the “Museum of the History of Spy Equipment” (H. Keith Melton, Нistorical Espionage Equipment, Jupiter, Florida, USA) for kindly providing the reference materials used in this publication. Last time, speaking about the important …
Results of the 15th anniversary of the legalization of the polygraph in Russia and current tasks for the near future.
Results of the 15th anniversary of the legalization of the polygraph in Russia and urgent tasks for the near future. Kholodny Yu.I., Doctor of Law, Candidate of Psychological Sciences, Professor, Bauman Moscow State Technical University, Moscow Proceedings of the scientific and practical conference «Current status and development prospects of the instrumental method»lie detection» in the …
Products of JSC Krasnogorsk Plant named after A.S. Zverev
Products of OJSC Krasnogorsk Plant named after A.S. Zvereva NIGHT SIGHTS «ZENIT NV-100», «ZENIT -100-1», «ZENIT NV-100-3» SET «ZENIT NV-100 -Z-FS» NIGHT SIGHT «ZENIT NV-500» NIGHT SIGHT «ZENIT NV-1000» ILLUMINATION UNIT NIGHT SIGHT NP-75LC SPORT SIGHT OPTICAL SUPER-POWERFUL PHOTOSCOPE PS 4X43 SPORTS OPTICAL SUPER-PHOTOSCOPE PS 4X38 OPTICAL SIGHT OP4X 20SHU BINOCULAR OBSERVATION DEVICE WITH IMAGE …
Products of JSC Krasnogorsk Plant named after A.S. ZverevДалее …
CHANGING THE NATURE OF TERRORISM AND THE PROBLEMS OF LAW ENFORCEMENT MANAGEMENT IN THE FIGHT AGAINST ILLEGAL ARMED GROUPS IN THE CHECHEN REPUBLIC.
CHANGING THE NATURE OF TERRORISM AND PROBLEMS OF LAW ENFORCEMENT MANAGEMENT IN THE FIGHT AGAINST ILLEGAL ARMED FORMATIONS IN THE CHECHEN REPUBLIC. CHANGING THE NATURE OF TERRORISM AND PROBLEMS OF LAW ENFORCEMENT MANAGEMENT IN THE FIGHT AGAINST ILLEGAL ARMED FORMATIONS IN THE CHECHEN REPUBLIC Chesnokov V.F., professor of the Academy of the FSB of Russia, …
How to identify counterfeit dollars.
How to identify counterfeit dollars. There are special detectors in exchange offices and banks that use infrared and magnetic radiation to determine the authenticity of American currency. But those who do not have tricky bank detectors should not be upset. «The most perfect mechanism for checking the authenticity of the dollar is a person, » …
How to organize a business intelligence service.
How to organize a business intelligence service. How to organize a business intelligence service HOW TO ORGANIZE A BUSINESS INTELLIGENCE SERVICE Boris Liflyandchik, Nikolay Likhodeyev candidates of physical and mathematical sciences We appeal first of all to those entrepreneurs and managers who, having realized the importance of business intelligence (see our previous article in «MB» …
How to behave if you suspect that you have been bookmarked.
How to behave if you suspect that you have been bookmarked. How to behave if you suspect that you have been bookmarked James M. Atkinson, Granite Island Group How to behave if you suspect that you have been bookmarked Keep calm Contact an ASAP TSCM Specialist Use email to communicate, but be discreet You …
How to behave if you suspect that you have been bookmarked.Далее …
How to order TSCM inspection.
How to order a TSCM inspection. How to order a TSCM inspection. James M. Atkinson, Granite Island Group How to order a TSCM inspection. Remember that there are only six legitimate and competent TSCM specialist firms in the US private sector (twelve worldwide), be patient in finding one that can help you. TSCM, Bug Clearing, …
Catalogue of the company AUDIOTEL.
AUDIOTEL company catalog. AUDIOTEL company catalog Received in May 1998. AUDIOTEL company catalog Search equipment for detecting technical control devices Detection of radio bugs Scanlock ECM Plus 201-360 Described by leading US publications as “an essential part of the counter-monitoring device suite,” the Scanlock provides complete protection against radio bugs from 10 kHz to 4 …
Catalogue of Audiotel International.
Audiotel International catalog. Audiotel International catalog
Catalogue of the company IKMC.
Catalog of the IKMC company. Catalog of the company IKMC Hardware and software complex for conducting vibroacoustic measurements VNK-012GL Vibroacoustic protection equipment VNG-012GL Device for protecting premises from speech information leakage VNG-006D NR-µ Nonlinear Transition Detector NR900EM Professional Nonlinear Transition Detector LBD-50 Wired Communications Analyzer SMD-100 and SMD-300 Metal Detectors Electromagnetic radiation control complex RCC-2000 …
Catalog of technical equipment from Shearwater ECM.
Shearwater ECM technical equipment catalog. . Company History Products Antennae Bloodhound Hunter Locator XD Merlin NEW Product Spectrum ECM6 NEW Product Training
Keith Melton and his spy museum. Listening devices.
Keith Melton and his spy equipment museum. Vadim Antonovich Shelkov Keith Melton and his spy equipment museum. Eavesdropping devices It seems to me that the desire to learn someone's secrets is inherent in human nature itself. Whatever they say, but eavesdropping on other people's conversations, despite all the reprehensibility of this activity, has always been …
Classifications, features and information-measuring models of detection equipment.
Classifications, features and information-measuring models of detection equipment. Classifications, features and information-measuring models of detection equipment. Classifications, features and information-measuring models of detection equipment. ZVEZHINSKY Stanislav Sigismundovich, Doctor of Technical Sciences, Associate Professor,IVANOV Vladimir Anatolyevich, Candidate of Technical Sciences, Associate Professor, RUDNICHENKO Valery Aleksandrovich One of the current areas of development of technical security means …
Classifications, features and information-measuring models of detection equipment.Далее …
Classification of electronic devices for interception of information.
Classification of electronic devices for intercepting information. Classification of electronic devices for intercepting information ХОРЕВ Анатолий Анатольевич,профессор, док& #1090;ор технических наук, Московский государствен&# 1085;ый институт электронной техники (Технический у& #1085;иверситет) КЛАССИФИКАЦ ИЯ ЭЛЕКТРОННЫХ УСТРОЙСТВ ПЕРЕХВАТА ИНФОРМАЦИИ Источник: Науч& #1085;о-технически&# 1081; журнал «Спецтехника и связь» В статье систематизир&# 1086;ваны показатели классификаци&# 1080; и классификаци&# 1086;нные признаки …
Classification of electronic devices for interception of information.Далее …
When will the limit be reached?
When will the limit be reached?. When will the limit be reached? When will the limit be reached? The proposed article once again returns us to the question of the necessary key length for symmetric encryption algorithms. Despite the fact that this topic has already been widely covered in the press, the author of this …
When it's time to pick up the keys.
When it's time to pick keys. When it's time to pick keys When it's time to pick keys Is it always necessary to start cryptanalysis immediately after receiving the ciphertext? Perhaps if you wait a little, the final result will be obtained faster? A group of well-known cryptographers, created under the auspices of the Alliance …
Integrated application of various technologies to improve airport security.
Integrated application of various technologies to improve airport safety. Integrated application of various technologies to improve airport safety. Aviation Week & Space Technology.- 1996 .- 145, №15-P. 50-52. Integrated application of various technologies to improve airport safety. The use of modern explosive detection systems and installations can significantly improve airport security, but even a perfect …
Integrated application of various technologies to improve airport security.Далее …
Compromise of active and passive methods of vibroacoustic information protection.
Compromise of active and passive methods of vibroacoustic information protection. Compromise of active and passive methods of vibroacoustic information protection. Compromise of active and passive methods of vibroacoustic information protection. A.Kondratyev, O.Klyanchin Catalog «Security Systems-2005» Protection of speech data from possible leakage via technical channels is one of the most important tasks of ensuring information …
Compromise of active and passive methods of vibroacoustic information protection.Далее …
Computer crime in Russia. Current state.
Computer crime in Russia. Current state. Computer crime in Russia. Current state Computer crime in Russia. Current state Banking information systems containing commercial information are actively subject to external intrusion by organized groups of hackers. The banks that have suffered from such crimes try not to attract public attention for fear of losing their credibility. …
Computer steganography yesterday, today, tomorrow..
Computer steganography yesterday, today, tomorrow. Vyacheslav Sergeevich Ukov, PhD in Engineering Andrey Petrovich Romantsov COMPUTER STEGANOGRAPHY YESTERDAY, TODAY, TOMORROW. Information security technologies of the 21st century. The task of reliable protection of information from unauthorized access is one of the oldest and still unsolved problems. Methods and techniques for hiding secret messages have been known …
Who can listen to your cell phone?
Who can listen in on your cell phone?. Who can listen in on your cell phone? Who can listen in on your cell phone? ‘Everyone has the right to privacy of correspondence, telephone conversations, postal, telegraph and other messages. Restriction of this right is allowed only on the basis of a court decision’. Constitution of …
CONCEPT OF SECURE ADMINISTRATION OF WINDOWS NT.
WINDOWS NT SECURE ADMINISTRATION CONCEPT. WINDOWS NT SECURE ADMINISTRATION CONCEPT WINDOWS NT SECURE ADMINISTRATION CONCEPT Most concepts of secure administration of the Microsoft Windows MT OS assign a special role to numerous inconsistent parameters of the OS, paying insufficient attention to the issues of defining the roles of the administrator and other privileged users of …
Security concept: mathematical analysis of efficiency.
Security concept: mathematical analysis of efficiency. Security concept: mathematical analysis of efficiency . Security concept: mathematical analysis of efficiency In modern conditions, threats are constant companions of business, sadly enough. Therefore, it is unthinkable without reliable protection of its interests. But how to organize it correctly? How to develop an optimal strategy and tactics of …
Security concept: mathematical analysis of efficiency.Далее …
The concept of protecting computing equipment and automated systems from unauthorized access to information.
Concept of protecting computing equipment and automated systems from unauthorized access to information.. Concept of protecting computing equipment and automated systems from unauthorized access to information. GUIDELINES CONCEPT OF PROTECTION OF COMPUTER EQUIPMENT AND AUTOMATED SYSTEMS FROM UNAUTHORIZED ACCESS TO INFORMATION Accepted abbreviations AS — automated system KSZ — complex of security tools NSD — …
Briefly about the radioactive gas radon. Article updated in 2023.
Briefly about the radioactive gas radon. Briefly about the radioactive gas radon. Radon is an inert gas that has no color, taste, or odor. Of the three isotopes of radon (radon, thoron, and actinon), which are radioactive gases, radon-222 poses the greatest radiation hazard to the population. This radioactive gas is formed as a result …
Briefly about the radioactive gas radon. Article updated in 2023.Далее …
A brief history of the development of the psychophysiological instrumental method of lie detection.
A brief history of the development of the psychophysiological hardware method of lie detection. A Brief History of the Development of the Psychophysiological Instrumental Method of Lie Detection Kholodny Yu. I., Doctor of Law, Candidate of Psychological Sciences, Head of Department, Institute of Criminalistics of the FSB of Russia A Brief History of the Development …
Short messages.
Brief messages. Brief messages Brief messages According to the Moscow Times, a graduate of the University of California, Yakov Goldberg, reported that he managed to crack the strongest cipher allowed by U.S. law for unrestricted export. It took only 3.5 hours to decrypt it. This demonstrated the weakness of export restrictions that stipulate the length …
Forensic polygraphology and its application in law enforcement practice.
Forensic polygraph science and its application in law enforcement practice. Kholodny Yu. I, Doctor of Law, Candidate of Psychological Sciences, Head of Department, Institute of Forensic Science of the FSB of Russia Information bulletin No. 21 based on materials of forensic readings «Practical requests are the driving force behind the development of forensic science and …
Forensic polygraphology and its application in law enforcement practice.Далее …
FORENSIC SYSTEM FOR DETERMINING CONTRADICTIONS IN WITNESS TESTIMONY.
CRIMINALISTIC SYSTEM FOR DETERMINING CONTRADICTIONS IN WITNESS TESTIMONY. RATKIN Leonid Sergeevich, Candidate of Technical Sciences In forensic science, a situation often arises when the testimonies of defendants, witnesses and other persons are confusing, contradictory and difficult to reconcile with other testimonies. Currently, special automated systems can be used to determine contradictions and “inconsistencies”, the essence …
FORENSIC SYSTEM FOR DETERMINING CONTRADICTIONS IN WITNESS TESTIMONY.Далее …
Forensic investigations using a polygraph and forensic psychophysiological examination.
Forensic examinations using a polygraph and forensic psychophysiological examination. Yu.I. Kholodny Doctor of Law, Candidate of Psychological Sciences, Bauman Moscow State Technical University In the spring of 1993, polygraph interrogations (OIP) were approved for use in operational-search activities (ORD) on the territory of Russia. Over the past years, the use of the polygraph in law …
Forensic investigations using a polygraph and forensic psychophysiological examination.Далее …
Cryptographic algorithms.
Cryptographic algorithms. Cryptographic algorithms Cryptographic algorithms A chain is only as secure as its weakest link: the stronger the link, the stronger the chain. A good cryptosystem must have its algorithm, protocol, keys, and everything else thoroughly tested. If a cryptographic algorithm is strong enough, but the random number generator used to create the keys …
Cryptographic logic unit for encoders.
#Cryptographic logical device, #encoder Cryptographic logical device for encoders. Pat. 5365591 USA, IPC N 04 K 1/00.- Publ. 11/15/94. The US patent described below notes that modern encoders implement complex cryptographic algorithms and contain a number of microprocessors that perform various functions in the process of encrypting information. Due to the high complexity of cryptographic …
Who is listening to your cell phone
Is your cell phone being tapped? The world is so arranged that any technical invention of the human mind that expands our capabilities and creates additional comfort for us inevitably contains negative aspects, a potential danger for the user. Modern means of wireless personal communication (radio telephone, pager and cell phone) are no exception. Yes, …
For discussion of the draft Law on Electronic Digital Signature.
To discuss the draft Law on Electronic Digital Signature. To discuss the draft Law on Electronic Digital Signature To discuss the draft Law on Electronic Digital Signature From December 22 to 25, 1999 and from February 3 to 5, 2000, two international conferences, «RusCrypto-99» and «RusCrypto-2000», were held in the Moscow region settlement of Nepetsino. …
For discussion of the draft Law on Electronic Digital Signature.Далее …
On the issue of increasing the level of information protection from leakage from technical means.
On the issue of increasing the level of information protection from leakage from technical means. On the issue of increasing the level of information protection from leakage from technical means On the issue of increasing the level of information protection from leakage from technical means. Dorokhov Stanislav Vasilyevich Source: magazine «Special Equipment» When discussing …
Laser microphones — a universal means of reconnaissance or another fashion fad?
Laser microphones — a universal reconnaissance tool or another fashion fad?. Laser microphones — a universal reconnaissance tool or another fashion fad? Laser microphones — a universal reconnaissance tool or another fashion fad? A. V. LYSOV “PPSh LABORATORY” In recent years, information has emerged that intelligence agencies in various countries and unfairly competing firms are …
Laser microphones — a universal means of reconnaissance or another fashion fad?Далее …
Licensing of activities in the field of technical protection of confidential information.
Licensing of activities in the field of technical protection of confidential information.. Licensing of activities in the field of technical protection of confidential information. Licensing of activities in the field of technical protection of confidential information Confidential information— information that does not contain information constituting a State secret, but with limited access to it Technical …
Licensing of activities in the field of technical protection of confidential information.Далее …
Lumens, candelas, watts and photons.
#Special Equipment Lumens, candelas, watts and photons. KRUTIK Mikhail Ilyich, MAYOROV Viktor Petrovich LUMENS, CANDELAS, WATTS AND PHOTONS. DIFFERENT UNITS – DIFFERENT RESULTS OF MEASURING THE SENSITIVITY OF TELEVISION CAMERAS BASED ON IMAGE TUBE AND CCD (Source — «Special Technology» magazine, No. 5, 2002) ) The authors of this article, due to the nature of …
Luminescent fingerprint scanners.
Luminescent devices for taking fingerprints. Luminescent devices for taking fingerprints Law Enforcement Technology.- 1995 .- March.- P. 50-51. Luminescent devices for taking fingerprints When the possibility of detecting latent fingerprints was first discovered in the late 1800s, the main tool used by the investigator using this opportunity was a brush and black fine-grained powder. In …
Models of explosive devices.
Models of explosive devices. Models of explosive devices MODELS OF EXPLOSIVE DEVICES Source: magazine «Special Equipment» Model of an explosive device in an electric razor. General view of the model. X-ray of the model. Model composition: 1. Explosive charge. 2. Electric detonator. Operating principle. When the electric razor is plugged into the electrical network, the …
Little tricks of counterfeiters..
Little tricks of counterfeiters.. Little tricks of counterfeiters. Little tricks of counterfeiters. Shaposhnikov Yu.I. Source: When talking about counterfeit banknotes, we can't help but mention how counterfeiters imitate watermarks. There aren't many ways, but some of them are quite exotic. Once we got our hands on a banknote that was made rather poorly, but when …
Masking of information emissions from computer equipment.
Masking of information radiation from computing equipment. Masking of information radiation from computing equipment Masking of information radiation from computing equipment In recent years, much attention has been paid to the protection of commercial and secret information processed using computer technology. Information leakage can occur both through unauthorized access to computer databases and through the …
Masking of information emissions from computer equipment.Далее …
The place of forensic psychophysiological examination using a polygraph in the system of forensic examinations.
The place of forensic psychophysiological examination using a polygraph in the forensic examination system. Kholopova E.N. Doctor of Law, Candidate of Psychological Sciences, Expert Psychologist of the State Institution KLSE MJ RF Kaliningrad Kravtsova G.K. Polygraph Specialist «Kaliningrad Center for Forensicexamination and assessment» Kaliningrad Source: Proceedings of the international scientific and practical conference «Current status …
Metal detectors — weapon detectors.
Metal detectors — weapon detectors. David Pavlovich Berezansky, Candidate of Technical Sciences Source: magazine «Special Equipment» ; Currently, devices that use magnetic methods to solve problems of detecting conductive objects in a non-conductive environment have become widespread in various areas of human activity. Metal detectors (metal detectors, metal detectors) are used today in flaw detection …
Metal detectors and metal detectors from Institute Dr. Forster.
Metal detectors and metal detectors by Institute Dr. Forster. Metal detectors and metal detectors by Institute Dr. Forster Securitech.- 1995 .- Reference index 37. Metal detectors and metal detectors by Institute Dr. Forster Firm Institute Dr. Forster (Germany), with branches in the USA, Brazil, Japan, Singapore, Great Britain, Italy and France, with 40 years of …
Metal detectors and metal detectors from Institute Dr. Forster.Далее …
Metal detectors and ferromagnetic material detectors from Vallon.
Vallon metal detectors and ferromagnetic material detectors. Vallon metal detectors and ferromagnetic material detectors. Securitech. — 1995 .- Reference indexes 66,67. Vallon metal detectors and ferromagnetic material detectors. Vallon (Germany) has 30 years of experience in the development and production of metal detectors and ferromagnetic material detectors. The high quality of this company's products meets …
Metal detectors and ferromagnetic material detectors from Vallon.Далее …
Methodology for examining premises using the CPM-700 device.
Methodology for examining premises with the CPM-700 device. Methodology for examining premises with the CPM-700 device. Methodology for examining premises with the CPM-700 device. Position 1: Unauthorized devices use transmission channels that create physical fields of a certain intensity that can be measured instrumentally. Position 2: The field intensity of physical fields increases as it …
Methodology for examining premises using the CPM-700 device.Далее …
Methodology for constructing a corporate information security system.
Methodology for building a corporate information security system. Methodology for building a corporate information security system. Methodology for building a corporate information security system. Sergey Petrenko Source — Most of the directors of automation services (CIO) and information security (CISO) of Russian companies have probably asked themselves the question: «How to assess the level of …
Methodology for constructing a corporate information security system.Далее …
Methods and equipment for adaptive filtering of speech signal.
Methods and equipment for adaptive filtering of speech signal. Methods and equipment for adaptive filtering of speech signal. Methods and equipment for adaptive filtering of speech signal. V. I. Zolotarev, Ph.D., senior researcher. General information on interference and adaptive filtering. Recording, analysis and processing of audio information are one of the most important factors in …
Methods and equipment for adaptive filtering of speech signal.Далее …
Methods and equipment for adaptive sound filtering.
Methods and equipment for adaptive sound filtering. Methods and equipment for adaptive sound filtering Methods and equipment for adaptive sound filtering V. I. Zolotarev, Head of Department «Business Security», PhD, Senior Researcher General information about interference and adaptive filtering Recording, analysis and processing of audio information are one of the most important factors in …
Methods and techniques of counterfeiting.
Methods and techniques of counterfeiting.. Methods and techniques of counterfeiting. Methods and techniques of counterfeiting. Shaposhnikov Yu.I. Having familiarized ourselves with the main features of production and «secrets» of genuine banknotes, let us consider the most popular methods of counterfeiting. First, we will consider the methods of obtaining the main motifs of the image, and …
Methods and means of protecting telephone sets and telephone lines.
Methods and means of protecting telephone sets and telephone lines. Methods and means of protecting telephone sets and telephone lines Khorev Anatoly Anatolyevich Methods and means of protecting telephone sets and telephone lines Source: magazine «Special Equipment» When protecting telephone sets and telephone lines, several aspects must be taken into account: telephones (even when the …
Methods and means of protecting telephone sets and telephone lines.Далее …
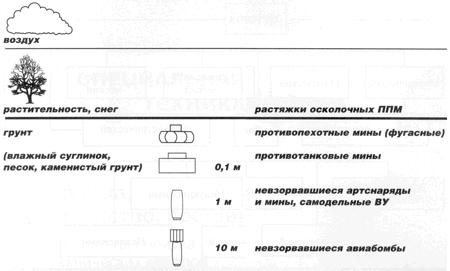
Mine Detection Methods – Applied to the Problem of Humanitarian Demining
SHCHERBAKOV Grigory Nikolaevich, Doctor of Technical Sciences, Professor METHODS OF MINE DETECTION — AS APPLIED TO THE PROBLEM OF HUMANITARIAN DEMINING RELEVANCE OF THE PROBLEM One of the unsolved problems with which humanity entered the third millennium is the problem of “humanitarian demining”. After the end of World War II, numerous military conflicts continued …
Mine Detection Methods – Applied to the Problem of Humanitarian DeminingДалее …
Methods of dead reckoning in systems for determining the location of moving objects.
Dead reckoning methods in positioning systems for moving objects.. Dead reckoning methods in positioning systems for moving objects. Petrov Nikolay Nikolaevich, Candidate of Technical Sciences DAY REPORTING METHODS IN POSITIONING SYSTEMS FOR MOBILE OBJECTS This article is a continuation of a series of articles on vehicle positioning systems (AVL systems) and is devoted to the …
Methods of dead reckoning in systems for determining the location of moving objects.Далее …
Method of magnetometric detection of explosive objects.
Method of magnetometric detection of explosive objects. ZVEZHINSKY Stanislav Sigismundovich, Doctor of Technical Sciences PARFENTSEV Igor Valerievich, Candidate of Technical Sciences METHOD OF MAGNETOMETRIC DETECTION OF EXPLOSIVE OBJECTS Source: Magazine «Special Equipment and Communications» The problem of humanitarian demining, as well as the search for unexploded ordnance (UXO) are currently very pressing. On the territory …
Method of magnetometric detection of explosive objects.Далее …
A method for protecting information on floppy disks from unauthorized copying.
Method of protecting information on floppy disks from unauthorized copying. Method of protecting information on floppy disks from unauthorized copying Method of protecting information on floppy disks from unauthorized copying When ensuring the safety of information resources of personal computers, much depends on the choice of methods for protecting information on floppy disks (floppy disks) …
A method for protecting information on floppy disks from unauthorized copying.Далее …
METOR — the choice of professionals.
METOR — the choice of professionals. METOR — the choice of professionals METOR — the choice of professionals Anyone who has ever flown on an airplane is familiar with an arched metal detector. They are installed at security checkpoints in every airport. But few people know that metal detectors in almost all airports of the …
Instant erasure of information..
Instant erasure of information.. Instant erasure of information. Instant erasure of information. Today, magnetic media occupy the leading positions among storage media. These include audio, video, streamer cassettes, floppy disks, hard drives, etc. It is known from the theory of magnetic recording that information is recorded by successive action of an external magnetic field, changing …
Micro camera Zodchiy.
Microphoto camera Zodchiy. Microphoto camera Zodchiy Microphoto camera «Zodchiy» In the early 80s, the micro-miniature camera «Zodchiy» was created, which is rightfully considered one of the best Soviet special cameras of the second half of the 20th century. Designed for a standard «Minox» cassette, «Zodchiy» was a new design, intended primarily for photographing A4 documents …
Multi-channel telephone conversation recording system PHANTOM.
Multi-channel system for recording telephone conversations PHANTOM. Multi-channel system for recording telephone conversations PHANTOM Multi-channel system for recording telephone conversations PHANTOM There have been many publications on multi-channel telephone call recording systems recently. The range of equipment options offered on the market is quite wide. The choice of a specific solution is determined by such …
Multi-channel telephone conversation recording system PHANTOM.Далее …
Multichannel software-controlled electron-optical complexes for high-speed recording of a series of images of a fast-moving process.
Multichannel software-controlled electron-optical complexes for high-speed recording of a series of images of a fast-moving process. Mikhail Ilyich Krutik The article presents the principles of constructing software-controlled complexes for ultra-high-speed shooting of fast-moving processes. The basis of such devices are electron-optical converters (EOC) with nanosecond shutter control modules, providing recording of a sequence of frames …
Multichannel registration systems.
Multi-channel recording systems. General Provisions Recently, thanks to the improvement of computer technology (increased processor performance, the emergence of high-capacity “hard” drives, magneto-optical drives, etc.), as well as advances in the development of analog-to-digital converters (ADCs), a large number of multi-channel recording systems (MCS) have begun to appear on the special equipment market) audio information …
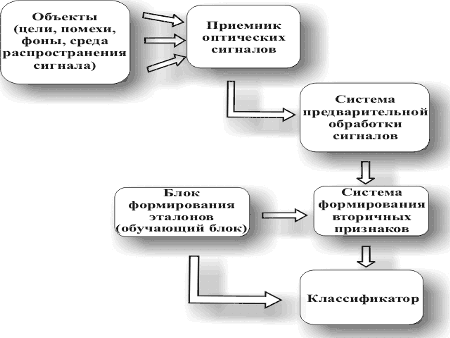
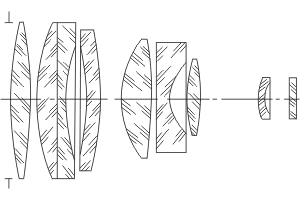
Multispectral optical-electronic systems.
Multispectral optoelectronic systems. TARASOV Viktor Vasilievich, Doctor of Technical Sciences YAKUSHENKOV Yuri Grigorievich, Doctor of Technical Sciences In this article, after considering some terminological issues, an attempt is made to assess the feasibility of using optical spectral methods in solving the most important problem facing many optoelectronic systems, namely, isolating a useful signal from a …
Multifunctional monitoring system for mobile and stationary objects Almaz.
MULTIFUNCTIONAL SYSTEM FOR DISPATCHING AND MONITORING MOBILE AND STATIONARY OBJECTS “ALMAZ” INTRODUCTION The basis of any complex of technical means for determining the location of moving objects is, first of all, the actual system for determining the location of moving objects. There are many different methods and systems for determining the location. A fairly …
Multifunctional monitoring system for mobile and stationary objects Almaz.Далее …
Mobile metal detectors.
Mobile metal detectors. Mobile metal detectors Mobile metal detectors The increasing number of aircraft hijackings in the late 1960s and early 1970s prompted the development of weapons detection equipment, particularly stationary metal detectors. Since then, metal detectors have evolved from simple metal detectors to sophisticated modern models equipped with «intelligence» that can distinguish non-ferrous metal …
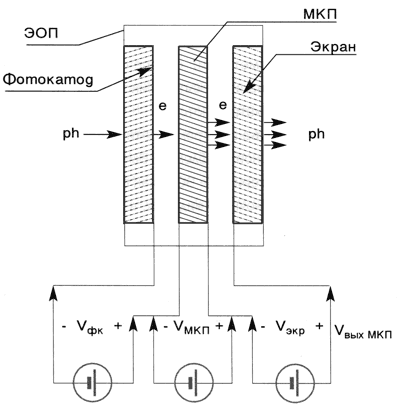
Modernization of night vision devices.
Modernization of night vision devices. ARKHUTIK Stepan Trofimovich, VOLKOV Viktor Genrikhovich, Candidate of Technical Sciences, Associate Professor, ZAYTSEVA Elena Ivanovna, SALIKOV Vyacheslav Lvovich, UKRAINSKY Sergey Alekseevich Night vision devices (NVD) are widely used in special equipment to ensure observation and aiming at dusk and at night. At the same time, there is a problem of …
Monograph. Methods of document protection.
Monograph. Methods of document protection. Contents INTRODUCTION Chapter 1. TECHNOLOGICAL PROTECTION Watermarks Methods of imitation of watermarks Security threads Imitation of security threads Security fibers Imitation of security fibers Optically variable inks Imitations of optically variable inks Holographic protection Composition of paper and its optical properties Imitation of paper properties Chapter 2. PHYSICO-CHEMICAL PROTECTION Luminescent …
Chipset for building Spread Spectrum devices.
Chipsets for building Spread Spectrum devices. Chipsets for building Spread Spectrum devices Chipsets for building Spread Spectrum devices Broadband data transmission systems, or Spread Spectrum, produced by various foreign companies differ from each other primarily in the method and speed of data transmission, type of modulation, transmission range, service capabilities, etc. This review examines chipsets …
Cash EURO. How to identify counterfeit euros.
Cash EURO. How to identify counterfeit euros. Cash EURO. How to identify counterfeit euros. Cash EURO. How to spot counterfeit euros Cash EURO: BANKNOTES Denomination: 500 euros Size: 160*82 mm Color: Purple Architectural period: Art Nouveau of the 20th century Denomination: 200 euros Size: 153*82 mm Color: Yellow-brown Architectural period: Iron and Glass Architecture Denomination: …
Directional microphones — myths and reality. Abalmazov E.I.
Directional microphones — myths and reality. Abalmazov E.I. Directional microphones — myths and reality. Abalmazov E.I. Directional microphones: myths and reality. Abalmazov Eduard Ivanovich, Doctor of Technical Sciences, Professor The article is reprinted from the journal «Security Systems» No. 4, 1996. There are all sorts of rumors about the capabilities of directional microphones. Some sincerely …
Directional microphones — myths and reality. Abalmazov E.I.Далее …
DRUG ANALYSIS — science or art?
DRUG ANALYSIS — science or art?. DRUG ANALYSIS — science or art? DRUG ANALYSIS — science or art? In the practice of investigation, there are often cases when the only thread that can be seized upon to reach the criminal is the testimony of victims or eyewitnesses. And there are also frequent cases when victims …
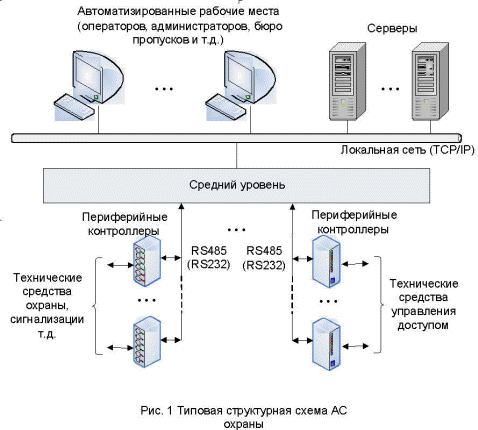
Some aspects of building integrated security systems. Architecture of automated systems.
Some aspects of building integrated security systems. architecture of automated systems.. Some aspects of building integrated security systems. architecture of automated systems. KOROLEV Vladimir Sergeevich Some aspects of building integrated security systems. architecture of automated systems Source: magazine «Special Equipment» No. 4 2007 Sooner or later, officials responsible for the security of the entrusted …
Some aspects of building integrated security systems. Architecture of automated systems.Далее …
Some features of post-test behavior of respondents.
Some features of the post-test behavior of respondents.. Some features of the post-test behavior of respondents. Molchanov A.Yu. Leading teacher of the polygraph examiner training school of the Ministry of Internal Affairs of Russia Moscow Some features of the post-test behavior of respondents. Source: Proceedings of the international scientific and practical conference«Current status and development …
Some ways to improve thermal imaging systems.
TARASOV Viktor Vasilievich, Doctor of Technical Sciences YAKUSHENKOV Yuri Grigorievich, Doctor of Technical Sciences, Professor SOME WAYS TO IMPROVE THERMAL IMAGING SYSTEMS The ever-increasing need for new optoelectronic systems used in a wide variety of fields of science and technology provides their developers with ample opportunities for creativity. This also applies to infrared (IR) technology …
SOME ISSUES OF LEGAL REGULATION OF THE ORGANIZATION OF COUNTER-TERRORIST OPERATIONS.
SOME ISSUES OF LEGAL REGULATION OF ORGANIZING COUNTER-TERRORIST OPERATIONS. SOME ISSUES OF LEGAL REGULATION OF ORGANIZING COUNTER-TERRORIST OPERATIONS Bondarenko A.E., professor of the FSB Academy of Russia, candidate of legal sciences, associate professor SOME ISSUES OF LEGAL REGULATION OF ORGANIZING COUNTER-TERRORIST OPERATIONS The adoption of the Federal Law “On Combating Terrorism” in 1998, according to …
SOME ISSUES OF LEGAL REGULATION OF THE ORGANIZATION OF COUNTER-TERRORIST OPERATIONS.Далее …
Some issues of computer crime investigation.
Some issues of computer crime investigation. Some issues of computer crime investigation. Some issues of computer crime investigation. V. Golubev Speech on February 26, 2003 at the Southeast Cybercrime Summit in Atlanta, USA Investigation of computer crimes differs significantly from investigations of other «traditional» crimes. In these criminal cases, errors are most often made, …
Non-linear radar: the “NR” concept.
Nonlinear radar: the “NR” concept. Dmitry Vladimirovich Semenov, postgraduate student at Bauman Moscow State Technical University Dmitry Viktorovich Tkachev NONLINEAR RADAR: THE “NR” CONCEPT. Over the last 6-7 years, Russia has experienced a real boom in the development of non-linear radars (NRL). During this time, more than ten (!) different models have been presented to …
NONLINEAR RADAR AND FEATURES OF THEIR APPLICATION FOR SEARCHING FOR BUGS.
NONLINEAR RADAR AND FEATURES OF THEIR APPLICATION FOR SEARCHING FOR BUGS.. NONLINEAR RADAR AND FEATURES OF THEIR APPLICATION FOR SEARCHING FOR BUGS. LOBASHEV Aleksey Konstantinovich, Candidate of Technical Sciences, Associate Professor NONLINEAR RADAR AND FEATURES OF THEIR APPLICATION FOR SEARCHING FOR BUGS Source: Magazine «Special Equipment» No. 6 2006 Non-linear radar (NLR) is probably the …
NONLINEAR RADAR AND FEATURES OF THEIR APPLICATION FOR SEARCHING FOR BUGS.Далее …
Nonlinear locator is an effective means of ensuring security in the field of information leakage.
Non-linear locator is an effective means of ensuring security in the field of information leakage. Non-linear locator is an effective means of ensuring security in the field of information leakage. Non-linear locator is an effective means of ensuring security in the field of information leakage. Dr.Sc. N.S. Vernigorov Director of NPP «Vikhr» The rapid development …
Don't be afraid: It IS.
Do not be afraid: It IS. Do not be afraid: It IS Do not be afraid: It IS Doctor of Psychology V.N. Pushkin writes: «The entire history of mankind testifies to the fact that this area was carefully encrypted at all stages and in all branches of human development. Such an encryption strategy was certainly …
Nickel-containing thin-film coatings on fibrous materials.
Nickel-containing thin-film coatings on fibrous materials.. Nickel-containing thin-film coatings on fibrous materials. Nickel-containing thin-film coatings on fibrous materials © L.M. Lynkov, V.A. Bogush, E.A. Senkovets, S.M. Zavadsky Belarusian State University of Informatics and Radioelectronics, Minsk E-mail: aleks@gw.bsuir.unibel.by A promising method for creating electromagnetic screens is vacuum deposition of thin films on fibrous materials. To study …
Nickel-containing thin-film coatings on fibrous materials.Далее …
Mink and sea otter are not only valuable fur.
Mink and Sea Otter are not only valuable fur. Mink and Sea Otter are not only valuable fur. MINK AND SEASPERD ARE NOT ONLY VALUABLE FUR V. Shelkov By a strange coincidence, at the beginning of the 21st century, nature, blind chance, and evil intent seemed to conspire to destroy the human race. Natural disasters, …
New information technology: “steganographic fingerprinting”.
New information technology: “steganographic fingerprinting”.. New information technology: “steganographic fingerprinting”. UKOV Vyacheslav Sergeevich, Candidate of Technical Sciences NEW INFORMATION TECHNOLOGY: “STEGANOGRAPHIC FINGERPRINTING” The article is a continuation of a series of publications on the problems of steganographic protection [1-3]. Based on the results of a comparative analysis of software products offered by the market …
New information technology: “steganographic fingerprinting”.Далее …
New development.
New development. New development New development The universal digital linear path (UDLP) equipment and the primary multiplexer BUS-ZO are new products in the field of telecommunications equipment from Izhevsk Radio Plant OJSC, a developer and manufacturer of equipment for space objects. The digitalization of communication networks that is currently taking place is primarily due to …
New horizons in wireless telephony.
New horizons in wireless telephony. New horizons in wireless telephony New horizons in wireless telephony How to organize communication in cases when it is necessary to maintain constant contact with employees who do not have a stationary workplace? The Kirk DECT-z 1500 system is both personal mobile communication equipment implemented in the DECT standard and …
New radio stations for secure communication.
New radio stations for secure communication. New radio stations for secure communication New radio stations for secure communication Since the end of the Cold War, the Department of Defense and other U.S. federal agencies have not relaxed their COMSBC requirements, but have made them even more stringent. In implementing the COMSBC policy, they proceed from …
Does a bank need a lie detector?
Does the bank need a “Lie Detector”?. Does the bank need a «Lie Detector»? Gamza V.A., candidate of legal and economic sciences, Chairman of the Board of Directors of Agrokhimbank OJSC, Kholodny Yu. I., Doctor of Law, Candidate of Psychological Sciences, Head of Department of the Institute of Criminalistics of the FSB of Russia Does …
Detection of metal objects in building structures.
Detection of metal objects in building structures. Detection of metal objects in building structures Kargashin Viktor Leonidovich Candidate of Technical Sciences Kolyada Sergey EgorovichMitrokhin Sergey Ivanovich Detection of metal objects in building structures When searching for hidden metal objects in building structures, microwave flaw detectors are used, for example /3/, which allow analyzing the internal …
Detection of explosives by analysis of their vapors and particles.
Detection of explosives by analyzing their vapors and particles. Vandyshev Boris Alekseevich, Candidate of Technical Sciences DETECTION OF EXPLOSIVES BY ANALYZING THEIR VAPORS AND PARTICLES Terrorism using explosives (HE) has become widespread throughout the world in recent years, the fight against this illegal phenomenon has been elevated to the rank of an international problem. The …
Detection of explosives by analysis of their vapors and particles.Далее …
Detection of explosive objects: hardware for anti-terrorist services.
Detection of explosive objects: hardware for anti-terrorist services. Detection of explosive objects: hardware for anti-terrorist services. Detection of explosive objects: hardware for anti-terrorist services. A. V. Kikhtenko, K. V. Eliseev ANDREY VLADIMIROVICH KIHTENKO — Candidate of Chemical Sciences, Head of Sector of the Siberian Branch of the State Institution Scientific and Production Association «Special Equipment …
Detection of explosive objects: hardware for anti-terrorist services.Далее …
Generalization of the practice of using the capabilities of the polygraph in the investigation of crimes.
Summary of the practice of using the capabilities of a polygraph in investigating crimes. Appendix to the letter of the Prosecutor General's Office of Russia (outgoing No. 28-15-05 dated 02/14/2006) Law enforcement agencies are constantly working to introduce forensic tools into investigative practice, which facilitate the timely detection of crimes and the formation of an …
Equipment, tools and devices for manual demining.
Equipment, tools and devices for manual demining. Petrenko Evgeny Sergeevich EQUIPMENT, TOOLS AND DEVICES FOR MANUAL DEMINING Various tools, devices and improvised materials can be used to perform work on searching for and rendering harmless explosive objects (EOD). Demining kits have become quite widespread, the most famous of which are KR-I, KR-O, KR-95, KR-97 “Blesna”. …
Justification of tactical and technical requirements for radio signal detection systems.
Justification of tactical and technical requirements for radio signal detection systems. Justification of tactical and technical requirements for radio signal detection systems. Kargashin Viktor Leonidovich Candidate of Technical Sciences Justification of tactical and technical requirements for radio signal detection systems The stability over time of the established indicators of protection of the allocated premises requires …
Justification of tactical and technical requirements for radio signal detection systems.Далее …
PROCESSING OF IMAGES OF LUMINESCENT OBJECTS IN FORENSIC TECHNICAL EXAMINATION OF DOCUMENTS.
PROCESSING IMAGES OF LUMINESCENT OBJECTS IN FORENSIC EXAMINATION OF DOCUMENTS. KORNYSHEV Nikolay Petrovich, Candidate of Technical Sciences, Associate Professor Source: Magazine «Special Equipment» № 1 2007 In technical and forensic examination of documents [1], a fairly wide range of methods is used, including luminescent analysis. When documents are illuminated in various spectral ranges, the luminescence …
PROCESSING OF IMAGES OF LUMINESCENT OBJECTS IN FORENSIC TECHNICAL EXAMINATION OF DOCUMENTS.Далее …
Review of several implementations of information destruction from magnetic media.
Review of several implementations of information destruction from magnetic media.. Review of several implementations of information destruction from magnetic media. A review of several implementations of information destruction from magnetic media. In this popular science study, we will try to evaluate the potential capabilities and effectiveness of several approaches to erasing information from magnetic media, …
Review of several implementations of information destruction from magnetic media.Далее …
Review of the Russian market of devices that detect wiretapping of telephone conversations.
Overview of the Russian market of devices that detect wiretapping of telephone conversations. Overview of the Russian market of devices that detect wiretapping of telephone conversations. Overview of the Russian market of devices that detect wiretapping of telephone conversations. The relevance of protecting telephone conversations has set the users of special equipment the task of …
Review of the Russian market of devices that detect wiretapping of telephone conversations.Далее …
Overview of nonlinear location technology.
Overview of nonlinear location technology.. Thomas JONES OVERVIEW OF NONLINEAR LOCATION TECHNOLOGY Currently, there is a serious discussion among information security experts about the optimal characteristics of nonlinear locators. The wide range of these devices available on the market sometimes causes difficulties for consumers in choosing equipment. We hope that this article will help answer …
On the use of relative prosodic and spectral characteristics in the task of forensic identification of a person by spoken speech.
On the use of relative prosodic and spectral characteristics in the task of forensic identification of a person by spoken speech. Kaganov A.Sh. Russian Federal Center for Forensic Examinations (the article has been submitted for publication in the collection of the Philological Faculty of Moscow State University) Forensic identification is the establishment of the presence …
On the use of X-rays to detect fingerprints.
On the use of X-rays to detect fingerprints. On the use of X-rays to detect fingerprints Vadim Antoninovich Shelkov On the use of X-rays to detect fingerprints Source: magazine «Special Technology» No. 2 2007. There are almost no references in the specialized literature to the use of X-rays to identify fingerprints, with the exception of …
On the study of the law of decrease of the electromagnetic field in real operating conditions.
On the study of the law of decrease of the electromagnetic field in real operating conditions.. On the study of the law of decrease of the electromagnetic field in real operating conditions. Goryachev Sergey Vyacheslavovich ON THE RESEARCH OF THE LAW OF DECAY OF THE ELECTROMAGNETIC FIELD IN REAL OPERATING CONDITIONS The article is interesting …
ASSESSMENT OF THE POSSIBILITY OF CREATING MEANS OF ACTIVE PROTECTION OF WATER AREAS BASED ON THE USE OF THE ELECTROHYDRAULIC EFFECT.
ASSESSMENT OF THE POSSIBILITY OF CREATING MEANS OF ACTIVE PROTECTION OF WATER AREAS BASED ON THE USE OF THE ELECTROHYDRAULIC EFFECT. ASSESSMENT OF THE POSSIBILITY OF CREATING MEANS OF ACTIVE PROTECTION OF WATER AREAS BASED ON THE USE OF ELECTROHYDRAULIC EFFECT ANTSELEVICH Mikhail Aleksandrovich, Doctor of Technical Sciences UDINTSEV Dmitry Nikolaevich, Candidate of Technical Sciences …
Operational psychodiagnostics of personality during psychophysiological research using a polygraph.
#Operational psychodiagnostics Operational psychodiagnostics of personality during a psychophysiological study using a polygraph. The need to quickly navigate the psychological characteristics of a person is one of the most difficult aspects of the work of a polygraph examiner. In a short period of time, he needs to understand how to interact with the subject in …
Operational sound recording..
Quick sound recording.. Quick sound recording. Quick sound recording. A TAPE RECORDER IS A TOOL FOR EVERYDAY USE. The activities of a modern employee of state law enforcement agencies or commercial security services are unthinkable without various means of office equipment or electronic equipment: allowing to significantly increase its information content, give it a comfortable …
Description of the experiment on testing the device for destroying information on magnetic media “Stek.
Description of the experiment to test the device for destroying information on magnetic media “Stek. Description of the experiment to test the device for destroying information on magnetic media “Stek. Description of the experiment for testing the device for destroying information on magnetic media “Stek” in the testing laboratory of the FSB of the Russian …
Description of the signs of authenticity of the 2004 modification of the Bank of Russia banknotes
Description of the authenticity features of the Bank of Russia banknotes of the 2004 modification. Description of the authenticity features of the Bank of Russia banknotes of the 2004 modification. Description of the authenticity features of the Bank of Russia banknotes of the 2004 modification. Source: The Bank of Russia puts into circulation modified banknotes …
Detection of illegal connections to networks.
Detection of illegal connections to networks. Detection of illegal connections to networks Detection of illegal connections to networks In the previous issue of our magazine we already wrote about methods of protection against unauthorized data retrieval devices (UDRD). In this article we continue this topic, but we suggest paying attention to the fact that a …
Determination of parameters of vibroacoustic noise reduction systems.
Determination of parameters of vibroacoustic noise suppression systems. Determination of parameters of vibroacoustic noise suppression systems. Tests were carried out by the Engineering and Commercial Multidisciplinary Center (ECMC-1) 1. Purpose of the tests. Determination of parameters of vibroacoustic noise reduction systems ANG-2000, VNG-1020, GSh-01, STENA, VAG-66, VNG-006 when installing their vibration exciters on various elements …
Determination of parameters of vibroacoustic noise reduction systems.Далее …
Determination of the maximum value of a dangerous signal induced by a personal computer and a local area network into the power supply network.
Determination of the maximum value of a dangerous signal induced by a personal computer and a local area network into the power supply network. Determination of the maximum value of a dangerous signal induced by a personal computer and a local area network into the power supply network Determination of the maximum value of a …
Polygraph testing and its scientific basis.
#Polygraph Polygraph survey and its natural scientific foundations. Polygraph survey and its natural scientific foundations Kholodny Yu. I.., Doctor of Law, Candidate of Psychological Sciences, Head of Department, Institute of Forensic Science of the FSB of Russia Polygraph survey and its natural scientific foundations Source: Journal «VESTNIK KRIMINALISTIKI» 2005. Issue 1 (13), pp. 39-48. After …
Organization of confidential office work.
Organization of confidential office work. Organization of confidential office work. Organization of confidential office work. V. Pankratyev Source — As a rule, the least attention is paid to the organization of confidential office work in information security, although obtaining confidential information through gaps in office work is the simplest and most cost-effective way to obtain …
PRINCIPLES OF TAKING INTO ACCOUNT THE KEY CHARACTERISTICS OF RADIATION MONITORING DEVICES WHEN DECISION-MAKING ON THE POSSIBILITY OF THEIR USE FOR DETECTING RADIOACTIVE MATERIALS AT THE STATE BORDER.
BASICS OF ACCOUNTING FOR KEY CHARACTERISTICS OF RADIATION MONITORING INSTRUMENTS WHEN DECISION-MAKING ON THE POSSIBILITY OF THEIR USE TO DETECT RADIOACTIVE MATERIALS AT THE STATE BORDER.. BASICS OF ACCOUNTING FOR KEY CHARACTERISTICS OF RADIATION MONITORING INSTRUMENTS WHEN DECISION-MAKING ON THE POSSIBILITY OF THEIR USE FOR DETECTING RADIOACTIVE MATERIALS AT THE STATE BORDER. Makhnev I.A., Lyamzenko …
Basic elements of protection of genuine banknotes.
Key security features of genuine banknotes.. Key security features of genuine banknotes. Key security features of genuine banknotes. Shaposhnikov Yu.I. Paper Banknotes are printed on high-quality durable paper specially designed for printing banknotes. As an example, let's briefly consider the process of making paper used to print US dollars. The raw material used for its …
The main signs of authenticity of US dollars.
The main signs of authenticity of US dollars.. The main signs of authenticity of US dollars. The main signs of authenticity of US dollars. Source: Banknotes called dollars first appeared back in 1861, when the American government decided to issue paper means of payment. The leaders of that young American state did not suspect how …
The main difficulties and problems of using a polygraph in law enforcement and personnel work and recommended ways to overcome them.
The main difficulties and problems of using a polygraph in law enforcement and personnel work and recommended ways to overcome them. The use of a polygraph in law enforcement and personnel activities from the moment of initiation of the procedure to the final decision and its implementation is a multi-level process, during the execution of …
FEATURES OF CONSTRUCTION OF PEDESTRIAN RADIATION MONITORS..
FEATURES OF CONSTRUCTION OF PEDESTRIAN RADIATION MONITORS.. FEATURES OF CONSTRUCTION OF PEDESTRIAN RADIATION MONITORS. RUDNICHENKO Valery Alexandrovich FEATURES OF CONSTRUCTION OF PEDESTRIAN RADIATION MONITORS Currently, many areas of human practical activity use sources of ionizing radiation. Any area of activity associated with such sources is potentially dangerous, since it leads to the risk of radiological …
FEATURES OF CONSTRUCTION OF PEDESTRIAN RADIATION MONITORS..Далее …
Features of the selection of measuring instruments for automated software and hardware complexes for the study of PEMIN.
Features of choosing a measuring instrument for automated hardware and software complexes for studying PEMIN.. Features of choosing a measuring instrument for automated hardware and software complexes for studying PEMIN. KONDRATIEV Andrey Valerianovich, NAGORNY Sergey Ivanovich, DONTSOV Vadim Vladimirovich, Candidate of Technical Sciences, Senior Researcher LOBASHEV Aleksey Konstantinovich, Candidate of Technical Sciences, Associate Professor Features …
Security features of the 1996 $100 bills.
Security features of 100-dollar bills of 1996. Security features of 100-dollar bills of 1996. Protection features of the 100-dollar bills of the 1996 model Source: Bills of 100 US dollars are the most common in Russia, so it is worth looking at them in more detail, especially since the new banknotes of the 1996 model …
Caution! Radiation! Basic concepts, units of measurement, impact on humans..
Beware! Radiation! Basic concepts, units of measurement, impact on humans.. Beware! Radiation! Basic concepts, units of measurement, impact on humans. Beware! Radiation! Basic concepts, units of measurement, impact on humans. A guide for citizens V. KHIZHNYAK The publication was carried out with the financial support of the Russian Regional Ecological Center. CAUTION! RADIATION: Project Manager …
Caution! Radiation! Basic concepts, units of measurement, impact on humans..Далее …
Domestic encryption standard.
Domestic encryption standard. Domestic encryption standard Domestic encryption standard S. Panasenko, &nb sp; &nb sp; &nb sp; &nb sp; Source: Peace and Security, No. 5, 2003 Despite the fact that GOST 28147-89 was adopted back in 1989, nowadays it is widely used both in Russia and in the world as …
Security television system with expanded dynamic range in computer image recording mode.
Security television system with expanded dynamic range in computer image recording mode.. Security television system with expanded dynamic range in computer image recording mode. Security television system with dynamic range expansion in computer image recording mode SMELKOV Vyacheslav Mikhailovich, Candidate of Technical Sciences, Associate Professor Source: Magazine «Special Equipment» No. 6 2007 In [1], an …
Security television system with expanded dynamic range in computer image recording mode.Далее …
A captured militant reported about impending explosions in Moscow.
A captured militant reported impending explosions in Moscow.. A captured militant reported impending explosions in Moscow. A captured militant reported impending explosions in Moscow Source — «Komsomolskaya Pravda», May 11, 2007 Umar Batukaev has been arrested on charges of preparing a terrorist attack and storing weapons and ammunition. Three Caucasians detained on suspicion of involvement …
A captured militant reported about impending explosions in Moscow.Далее …
ABOUT HIDDEN, SECRET, SIDE CHANNELS. AND NOT ONLY..
ABOUT HIDDEN, SECRET, SIDE CHANNELS. AND NOT ONLY.. ABOUT HIDDEN, SECRET, SIDE CHANNELS. AND NOT ONLY. ABOUT HIDDEN, SECRET, SIDE CHANNELS. AND NOT ONLY V.A. Galatenko (Doctor of Physical and Mathematical Sciences) About hidden channels This is not the first time that Jet Info has addressed the topic of covert channels. In 2002, a separate …
On licensing of certain types of activities in the field of information security by the Federal Agency for Government Communications and Information under the President of the Russian Federation (memo for applicant enterprises).
On licensing of certain types of activities in the field of information security by the Federal Agency for Government Communications and Information under the President of the Russian Federation (memo for enterprises — applicants).. On licensing of certain types of activities in the field of information security by the Federal Agency for Government Communications and …
About metal detectors.
About metal detectors. About metal detectors About metal detectors Metal detectors are electronic induction devices that allow you to detect metal objects in a neutral or weakly conductive environment, i.e. in soil, water, walls, wood, under clothing and in luggage, in food products, in the human and animal body, etc. The rapid development of microelectronics …
On rule-making in the field of technical protection of information and ensuring the uniformity of measurements.
On rule-making in the field of technical protection of information and ensuring the uniformity of measurements.. On rule-making in the field of technical protection of information and ensuring the uniformity of measurements. On rule-making in the field of technical protection of information and ensuring the uniformity of measurements. Nagorny S.I. Dontsov V.V. Ph.D., Senior Researcher …
On the results of testing X-ray inspection equipment.
On the results of testing X-ray inspection equipment. On the results of testing X-ray inspection equipment On the results of testing X-ray inspection equipment (XIE) 13.10.2006 On the results of testing XIE In pursuance of paragraph 6.1 of the decision of the meeting with the Head of the Department dated 26.07.2006 on the issue …
On the results of testing X-ray inspection equipment.Далее …
On the probability of breaking stream ciphers using the overlap method.
On the probability of breaking stream ciphers by the overlap method. On the probability of breaking stream ciphers by the overlap method On the probability of breaking stream ciphers by the overlap method Let there be a hoop or circle with a circumference of L centimeters. A strip of paper of length l1 is glued …
On the probability of breaking stream ciphers using the overlap method.Далее …
On amendments and additions to the special conditions for the acquisition of radio-electronic equipment and high-frequency devices.
On Amendments and Supplements to the Special Conditions for the Acquisition of Radio-Electronic Equipment and High-Frequency Devices. On Amendments and Supplements to the Special Conditions for the Acquisition of Radio-Electronic Equipment and High-Frequency Devices. Government of the Russian Federation Resolution dated February 25, 2000, No. 157 «On Amendments and Supplements to the Special Conditions for …
On the possibility of using an adaptive filter in an interference-type security system when detecting a moving underwater object.
On the possibility of using an adaptive filter in an interference-type security system when detecting a moving underwater object. On the possibility of using an adaptive filter in an interference-type security system when detecting a moving underwater object. KOLMOGOROV Vladimir Stepanovich, Candidate of Technical Sciences, Associate Professor KALASHNIKOV Ivan Ivanovich SENCHENKO Aleksey Georgievich, candidate of …
On the possibility of using nuclear magnetic resonance to detect explosives on the human body.
On the possibility of using NQR to detect explosives on the human body. GRECHISHKIN Vadim Sergeevich, Doctor of Physical and Mathematical Sciences, Professor SHPILEVOI Andrey Alekseevich, Candidate of Physical and Mathematical Sciences, Associate Professor BURMISTROV Valery Ivanovich ON THE POSSIBILITY OF USING NQR TO DETECT EXPLOSIVES ON THE HUMAN BODY In the last decade, …
about protective films.
about protective films. about protective films And again about protective films The most economical solution When choosing the type of glazing, one of the main factors for the user, in addition to reliability, quality and others, is the price he must pay for new, more durable and beautiful glass. Of the many possible options, the …
Panoramic frequency range receivers.
Panoramic frequency range receivers. Panoramic frequency range receivers Panoramic frequency range receivers The most important tasks of ensuring the security of communications and telecommunications:— search for and detection of electromagnetic signals with unknown parameters and radio interference; — identification of the type and parameters of modulation of electromagnetic oscillations, demodulation of the information contained in …
Password crackers.
Password crackers. Password crackers Password crackers User account database One of the main components of the Windows NT security system is the User Account Manager. It ensures interaction between other components of the Windows NT security system, applications, and services with the user account database (Security Account Management Database, or SAM for short). This database …
PEMIN.
PEMIN. author: Arkady Veits Why PEMIN? PEMIN— these are side electromagnetic radiation and interference The tasks of information security are so diverse, and their solution raises so many problems that managers and technical specialists in information security departments sometimes find it difficult to set priorities. It is necessary to deal with organizational issues of office …
List of licensing centers in the field of information security as of April 1998.
List of licensing centers in the field of information security as of April 1998. List of licensing centers in the field of information security as of April 1998. List of licensing centers in the field of information security As of April 1998. N p/p Name of the licensing center (departmental affiliation) Address , telephone …
List of licensing centers in the field of information security as of April 1998.Далее …
List of enterprises and organizations that received licenses for activities in the field of information security as of April 1998.
List of enterprises and organizations that received licenses for activities in the field of information security as of April 1998. List of enterprises and organizations that received licenses for activities in the field of information security as of April 1998. LIST of enterprises and organizations that received licenses for activities in the field of information …
List of types of activities in the field of information security subject to licensing by FAPSI.
List of activities in the field of information security subject to licensing by FAPSI. List of activities in the field of information security subject to licensing by FAPSI LIST OF ACTIVITIES IN THE FIELD OF INFORMATION SECURITY SUBJECT TO LICENSING BY FAPSI Development, production, certification testing, sale, installation, adjustment, installation and repair of encryption …
Polygraph and the law.
Recently, a large number of articles have appeared in the press about the use of a polygraph (lie detector) in commercial structures in Russia. The authors cite successful and entertaining cases from their own and other people's practice, and operate with numbers. This is interesting and attracts the attention of readers. Companies that produce such …
Polygraph and the law: it’s time to resolve issues of legal regulation.
Polygraph and the law: it's time to resolve issues of legal regulation. POLYGRAPH AND THE LAW: Olga Belyushina, All-Russian Research Institute of the Ministry of Internal Affairs of Russia Recently, a large number of articles have appeared in the press about the use of a polygraph (lie detector) in commercial structures in Russia. The authors …
Polygraph and the law: it’s time to resolve issues of legal regulation.Далее …
Purchase of night vision device.
Buying a night vision device. Buying a night vision device Buying a night vision device (some recommendations for the buyer) or «Looking into the darkness. Night vision devices» Magazine «Gun. Weapons and ammunition.» 4/1998 Introduction This is not an easy task (!), since dozens of models of night vision devices (NVD) from various manufacturers are …
Search for electronic devices for interception of information using electromagnetic field indicators.
Search for electronic devices for intercepting information using electromagnetic field indicators. Search for electronic devices for intercepting information using electromagnetic field indicators. Anatoly Anatolyevich KHOREV, Doctor of Technical Sciences, Professor Search for electronic devices for intercepting information using electromagnetic field indicators. Electromagnetic field indicators. Electromagnetic field indicators (detectors) allow detecting bugs (BD) installed in designated …
Search for stable features of digital voice recorders.
Search for stable features of digital voice recorders.. Search for stable features of digital voice recorders. Ivanov I.L. Search for stable features of digital voice recorders. The widespread use of digital audio recording devices in operational and investigative activities for experts conducting examinations with such source material imposes additional requirements for conducting research and answering …
Search for stable features of digital voice recorders.Далее …
Buying a Night Vision Device. Buyer's Guide..
Buying a night vision device. Recommendations for buyers.. Buying a night vision device. Recommendations for buyers. Buying a night vision device. Recommendations for buyers Source: http://nightvision.ru Choosing and purchasing a night vision device is not an easy task, since there are currently dozens of models of night vision devices (NVD) from various manufacturers available in …
US Cryptography Policy.
US Cryptography Policy. US Cryptography Policy International Security Review. — 1997 . — January/February. — P. 11-14. US Cryptography Policy Public key cryptography, which appeared in 1970, has radically changed and expanded the possibilities of using this information security technique. At the same time, the struggle has intensified between those who support the use of …
Suppression of voice recorders – possibilities and practical application.
#Suppression of voice recorders Suppression of voice recorders — possibilities and practical application. Iskhakov Boris Simukovich Kargashin Viktor Leonidovich, Candidate of Technical Sciences Yudin Leonid Mikhailovich, Candidate of Technical Sciences At present, despite the prohibitions in force in accordance with Russian legislation, the probability of leakage of confidential information organized by means of technical means …
Suppression of voice recorders – possibilities and practical application.Далее …
A promising dual-band antenna-feeder device for a mobile VHF radio communications radio center.
Promising dual-band antenna-feeder device for a radio center of mobile VHF radio communications.. Promising dual-band antenna-feeder device for a radio center of mobile VHF radio communications. KOSTYCHEV Alexander Nikolaevich, KRYUCHKOV Igor Borisovich, PUGACHEV Vladimir Anatolyevich. PROSPECTIVE DUAL-BAND ANTENNA-FEEDER DEVICE FOR A RADIO CENTER OF MOBILE VHF RADIO COMMUNICATION This article examines the general principles …
PEDESTRIAN RADIATION MONITORS.
PEDESTRIAN RADIATION MONITORS. PEDESTRIAN RADIATION MONITORS PEDESTRIAN RADIATION MONITORS V. Rudnichenko, S. Zvezhinsky Modern Security Technologies No. 3, 2007 Currently, radioactive substances (RS), which are sources of ionizing radiation, are used in many areas of human practical activity. Numerous studies of their effects on living organisms have shown that any activity associated with such sources …
Security subsystem in Windows NT.
Security subsystem in Windows NT. Security subsystem in Windows NT Security subsystem in Windows NT The article introduces readers to the possibilities of information protection in the Windows NT operating system from Microsoft. The author talks in detail about the features of working in a multi-user OS What happens if confidential information from your computer …
Subsurface location: new possibilities.
Subsurface location: new possibilities. Subsurface location: new possibilities. Skrebnev V.I. SUBSURFACE LOCATION: NEW POSSIBILITIES The article is reprinted from the journal «Special Equipment», No. 1, 1998. The human desire to look under an opaque surface is as old as the world. And all in order to gain additional knowledge and, accordingly, increase the safety of …
Search technical means based on introscopy methods. Acoustic search systems.
Search technical means based on introscopy methods. Acoustic search systems. Alexey Vasilyevich Kovalev, Doctor of Technical Sciences SEARCH TECHNICAL MEANS BASED ON INTROSCOPY METHODS.ACOUSTIC SEARCH SYSTEMS. The classical solution of a sufficiently wide range of search tasks carried out on the basis of introscopy and non-destructive testing methods involves, as a first and main …
Search technical means based on introscopy methods. Acoustic search systems.Далее …
Prospects for the application of nuclear methods for detecting explosives.
Prospects for the application of nuclear methods for detecting explosives. Prospects for the application of nuclear methods for detecting explosives. Aviation Week & Space Technology.- 1996 .- 145, No. 15 .- P. 46, 47, 49. Prospects for the application of nuclear methods for detecting explosives Despite the emerging unfavorable criticism of the method of detecting …
Prospects for the application of nuclear methods for detecting explosives.Далее …
Perimeter TSO: selection features.
Perimeter TSO. The variety of types and industrial samples of perimeter technical detection equipment poses the question of their correct selection to the facility management and security services based on the security requirements and conditions at a specific facility. Often, a contractor designing and installing security systems tends to offer only the types and samples …
Revision of US information security policy.
Revision of US Information Security Policy. Revision of US Information Security Policy. National Defense.- 1994 .- December.- P. 24, 25. Revision of US Information Security Policy. The Security Policy Board, chaired by the Deputy Secretary of Defense and the Director of the Central Intelligence Agency (CIA), prepares legislative and administrative recommendations to manage classified information …
Perimeter detection tools: specifics of quality assurance.
#Perimeter detection tools Perimeter detection tools: specifics of quality assurance Technical detection tools (TDS) are devices designed to detect the intrusion of a person or other unregulated object into a protected area. For these products, the environment with all the variety of its parameters and influencing factors is an integral part of their information channel, …
Perimeter detection tools: specifics of quality assurance.Далее …
F-5000 Perimeter Intrusion Detection System.
Perimeter intrusion detection system F-5000. Perimeter Intrusion Detection System F-5000 Securitech.— 1995 .— Reference Index 64. Perimeter Intrusion Detection System F-5000 The fiber-optic perimeter intrusion detection system F-5000 was developed by Trans Security Systems & Technology (Israel) for protecting high and medium risk facilities. This is a system with the best cost-effectiveness ratio in the …
School of Security.
Security School. «A specialist is like a gumboil: his completeness is one-sided.» Kozma Prutkov The security systems market, perhaps like no other, requires specialists to have knowledge from a wide variety of fields, such as electrical engineering, radio engineering, television, solid state physics, optics, mechanics, digital technology, chemistry, information technology, engineering psychology… The lack of …
Regulations on the certification of information technology objects according to information security requirements.
Regulations on the certification of information technology objects according to information security requirements. Regulations on the certification of information technology objects according to information security requirements. «APPROVED» By the Chairman of the State Technical Commission under the President of the Russian Federation Yu. Yashin » 25 » November 1994 REGULATION on certification of information technology …
Regulations on the accreditation of testing laboratories and bodies for certification of information security tools according to information security requirements.
Regulations on the accreditation of testing laboratories and bodies for certification of information security tools according to information security requirements. Regulations on the accreditation of testing laboratories and bodies for certification of information protection tools according to information security requirements APPROVED by the Chairman of the State Technical Commission under the President of the Russian …
Regulation on state licensing of activities in the field of information security. Part 2
Regulations on state licensing of activities in the field of information security. Part 1 Appendix 1 LIST TYPES OF ACTIVITIES OF ENTERPRISES IN THE FIELD OF INFORMATION SECURITY SUBJECT TO LICENSING BY THE STATE TECHNICAL COMMISSION OF RUSSIA Certification, certification testing of protected TSOI, technical means of information protection, technical means of monitoring the effectiveness …
Regulation on state licensing of activities in the field of information security. Part 2Далее …
Regulation on State Licensing of Activities in the Field of Information Security. Part 1
Regulations on State Licensing of Activities in the Field of Information Security. Approved by the Decision of the State Technical Commission under the President of the Russian Federation and the Federal Agency for Government Communications and Information under the President of the Russian Federation dated April 27, 1994 N 10 1. General Provisions.1.1. These Regulations …
Regulation on State Licensing of Activities in the Field of Information Security. Part 1Далее …
Regulation on the Interdepartmental Commission of the Security Council of the Russian Federation on Information Security.
Regulations on the Interdepartmental Commission of the Security Council of the Russian Federation on Information Security. Regulations on the Interdepartmental Commission of the Security Council of the Russian Federation on Information Security. APPROVED by Decree of the President of the Russian Federation dated September 19, 1997 N 1037 REGULATION «On the Interdepartmental Commission of …
Regulation on the Interdepartmental Commission of the Security Council of the Russian Federation for the Protection of Citizens' Rights and Public Safety, the Fight against Crime and Corruption.
Regulations on the Interdepartmental Commission of the Security Council of the Russian Federation for the Protection of Citizens' Rights and Public Safety, the Fight against Crime and Corruption. Regulations on the Interdepartmental Commission of the Security Council of the Russian Federation for the Protection of Citizens' Rights and Public Safety, the Fight against Crime and …
Regulations on the procedure for the manufacture, import into the Russian Federation and use on the territory of the Russian Federation of radio-electronic equipment (high-frequency devices) (approved by RF Government Resolution No. 643 of June 5, 1994).
Regulations on the procedure for the manufacture, import into the Russian Federation and use on the territory of the Russian Federation of radio-electronic means (high-frequency devices) (approved by RF Government Resolution No. 643 of June 5, 1994). Regulations on the procedure for the manufacture, import into the Russian Federation and use on the territory of …
Regulation on certification of information security tools according to information security requirements.
Regulation on the certification of information security tools according to information security requirements.. Regulation on the certification of information security tools according to information security requirements. Put into effect by order of the Chairman of the State Technical Commission of Russia dated October 27, 1995 No. 199 Registered by Gosstandart of Russia in the State …
REGULATIONS on the import into the Russian Federation and export from the Russian Federation of special technical means intended for the covert acquisition of information.
REGULATION on the import into the Russian Federation and export from the Russian Federation of special technical means intended for covert acquisition of information. REGULATION on the import into the Russian Federation and export from the Russian Federation of special technical means intended for covert acquisition of information APPROVEDby the Decree of the Government of …
Regulations on certification of information technology objects according to requirements.
Regulations on certification of informatization objects according to requirements. Regulations on certification of informatization objects according to requirements. APPROVED BY Chairman of the State Technical Commission under the President of the Russian Federation Yu. Yashin » November 25, 1994 REGULATION for certification of information technology objects according to the requirements ofinformation security Moscow 1994 …
Regulations on certification of information technology objects according to requirements.Далее …
Interference suppression products. Recommendations for selection and use.
Noise suppression products. recommendations for selection and use. Noise suppression products. recommendations for selection and use. Blandova Ekaterina Sergeevna, Doctor of Technical Sciences NOISE SUPPRESSION PRODUCTS. RECOMMENDATIONS FOR SELECTION AND USE. The most important condition for protecting information in technical means is the creation of a specialized base of technological components of interference suppression products, …
Interference suppression products. Recommendations for selection and use.Далее …
The last argument.
The last argument. The last argument. The last «argument». A sedative by force. A police baton cannot be clearly classified. Its use does not involve causing significant harm to a person. Apparently, this is why batons are vaguely called «special means». In fact, the term «police baton» is accepted in the West. Our police pacify …
The last chance to prove innocence. Psychophysiological examination using a polygraph has the right to exist.
The last chance to prove innocence. Psychophysiological examination using a polygraph has the right to exist. In modern investigative and judicial practice, forensic psychophysiological examination using a polygraph has been formed and is used in criminal and civil cases, as well as in cases of administrative offenses. Such an examination is appointed in the presence …
Resolution of the Government of the Russian Federation of July 17, 1996 No. 832 On approval of special conditions for the acquisition of radio-electronic equipment and high-frequency devices.
RF Government Resolution of July 17, 1996 No. 832 On Approval of Special Conditions for the Acquisition of Radio-Electronic Equipment and High-Frequency Devices. RF Government Resolution of July 17, 1996 No. 832 On Approval of Special Conditions for the Acquisition of Radio-Electronic Equipment and High-Frequency Devices. RF Government Resolution of July 17, 1996 No. 832 …
Resolution of the Government of the Russian Federation of December 24, 1994 No. 1418 On licensing of certain types of activities.
Resolution of the Government of the Russian Federation of December 24, 1994 N 1418 On licensing of certain types of activities. RF Government Resolution of December 24, 1994 N 1418 On Licensing of Certain Types of Activities RF Government Resolution of December 24, 1994 N 1418 «On Licensing of Certain Types of Activities» (as amended …
Resolution of the Government of the Russian Federation of August 2, 1997 No. 973 On approval of the Regulation on preparation for the transfer of information constituting a state secret to other states.
Resolution of the Government of the Russian Federation of August 2, 1997 N 973 On approval of the Regulation on preparation for the transfer of information constituting a state secret to other states. RF Government Resolution of August 2, 1997 N 973 On Approval of the Regulation on Preparation for Transfer of Information Constituting a …
Resolution of the Government of the Russian Federation of September 4, 1995 No. 870 On approval of the Rules for classifying information constituting a state secret as belonging to various levels of secrecy.
Resolution of the Government of the Russian Federation of September 4, 1995 N 870 On approval of the Rules for classifying information constituting a state secret to various degrees of secrecy. RF Government Resolution of September 4, 1995 N 870 On Approval of the Rules for Classifying Information Constituting a State Secret to Various Classification …
Resolution of the Government of the Russian Federation On licensing the activities of enterprises, institutions and organizations in carrying out work related to the use of information constituting a state secret, the creation of means of information protection…..
Resolution of the Government of the Russian Federation On licensing the activities of enterprises, institutions and organizations to carry out work related to the use of information constituting a state secret, the creation of information protection tools….. Resolution of the Government of the Russian Federation On licensing the activities of enterprises, institutions and organizations to …
Resolution of the Supreme Court of the Russian Federation of March 13, 1992 No. 2507-1 On the procedure for introducing the Law of the Russian Federation On operational-search activities in the Russian Federation.
Resolution of the Supreme Court of the Russian Federation of March 13, 1992 N 2507-1 On the procedure for introducing the law of the Russian Federation On operational-search activities in the Russian Federation. Resolution of the Supreme Court of the Russian Federation of March 13, 1992 N 2507-1 On the procedure for introducing the law …
Resolution of the Supreme Court of the Russian Federation of February 19, 1993 No. 4525-1 On the introduction of the Law of the Russian Federation On federal bodies of government communications and information.
Resolution of the Supreme Court of the Russian Federation of February 19, 1993 N 4525-1 On the entry into force of the Law of the Russian Federation On federal bodies of government communications and information. Resolution of the Supreme Council of the Russian Federation of February 19, 1993 No. 4525-1 On the Entry into Force …
Resolution of the Supreme Court of the Russian Federation of July 21, 1993 No. 5486-1 On the procedure for introducing the Law of the Russian Federation On State Secrets.
Resolution of the Supreme Court of the Russian Federation of July 21, 1993 N 5486-1 On the procedure for putting into effect the Law of the Russian Federation On State Secrets. Resolution of the Supreme Council of the Russian Federation of July 21, 1993 No. 5486-1 On the Procedure for Enacting the Law of the …
Resolution of the Supreme Court of the Russian Federation of March 5, 1992 No. 2446/1-1 On the introduction of the Law of the Russian Federation On Security.
Resolution of the Supreme Court of the Russian Federation of March 5, 1992 N 2446/1-1 On the entry into force of the Law of the Russian Federation On Security. Resolution of the Supreme Council of the Russian Federation of March 5, 1992 N 2446/1-1 On the Entry into Force of the Law of the Russian …
Improving the efficiency of night vision device development.
Increasing the efficiency of night vision device development.. Increasing the efficiency of night vision device development. VOLKOV Viktor Genrikhovich, PhD in Engineering, Associate Professor INCREASING THE EFFICIENCY OF NIGHT VISION DEVICE DEVELOPMENT As is known, night vision devices (NVD) are widely used in special equipment for observation and aiming at dusk and at night. However, …
Improving the efficiency of night vision device development.Далее …
Improving the efficiency of detecting dangerous signals using the OSCOR device based on the mapping method and peak spectrum analysis.
Improving the efficiency of detecting dangerous signals using the OSCOR device based on the mapping method and peak spectrum analysis. Improving the efficiency of detecting dangerous signals with the OSCOR device based on the method of mapping and analysis of peak spectra Aleksey Konstantinovich Lobashev, Candidate of Technical Sciences, Associate Professor Information Security Training Center …
INCREASING THE REDUNDANCY OF INFORMATION FIELDS OF ADAPTIVE CLASSIFIERS OF THE INFORMATION SECURITY SYSTEM.
INCREASING THE REDUNDANCY OF INFORMATION FIELDS OF ADAPTIVE CLASSIFIERS OF THE INFORMATION SECURITY SYSTEM.. INCREASING THE REDUNDANCY OF INFORMATION FIELDS OF ADAPTIVE CLASSIFIERS OF THE INFORMATION SECURITY SYSTEM. NESTERUK Gennady Filippovich, Candidate of Technical Sciences MOLDOVYAN Alexander Andreevich, Candidate of Technical Sciences NESTERUK Filipp Gennadievich VOSKRESENSKY Stanislav IgorevichKOSTIN Andrey Aleksandrovich INCREASING THE REDUNDANCY OF INFORMATION …
Practical implementation of absorption spectroscopy technology in a device for detecting trace amounts of explosives on objects.
Practical implementation of absorption spectroscopy technology in a device for detecting trace amounts of explosives on objects. Practical implementation of absorption spectroscopy technology in a device for detecting trace amounts of explosives on objects Boreysho Alexey Anatolyevich1, Candidate of Economic Sciences, Strakhov Sergey Yuryevich1, Candidate of Physical and Mathematical Sciences Konovalov Konstantin Anatolyevich1, Romanov Alexander …
Practical implementation of the Law on State Secrets.
Practical implementation of the law On state secrets. Practical implementation of the law On state secrets PRACTICAL IMPLEMENTATION OF THE LAW «ON STATE SECRETS» A.A. Grigoriev The Law «On State Secrets» provides for a fundamentally new approach to the procedure for issuing clearance to state secrets to enterprises, institutions and organizations. This procedure consists of …
Practical implementation of the Law on State Secrets.Далее …
Private investigation practice in the UK.
Private Investigation Practice in the UK. Private Investigation Practice in the UK Private Investigation Practice in the UK Professional private investigators are considered to play a significant role in English business, although, according to the press, some of them are characterized by a lack of control, low qualifications, and little work experience. THE RAPID EXPANSION …
Government of the Russian Federation. Resolution of July 29, 1998 No. 854.
Government of the Russian Federation. Resolution of July 29, 1998 N 854. Government of the Russian Federation. Resolution of July 29, 1998 N 854 GOVERNMENT OF THE RUSSIAN FEDERATION RESOLUTION of July 29, 1998 N 854 g. Moscow On the introduction of an amendment to the Regulation on licensing the activities of enterprises, institutions and …
Government of the Russian Federation. Resolution of July 29, 1998 No. 854.Далее …
Legal aspects of information security.
Legal aspects of information security. Legal aspects of information security Legal aspects of information security The tasks of building a civil society in Russia as an information society, the increasing role of information, information resources and technologies in the development of citizens, society and the state in the 21st century bring information security issues to …
Legal aspects of using a polygraph when working with personnel.
Legal aspects of using a polygraph when working with personnel. Polygraph surveys (often incorrectly called a «lie detector») are gradually being introduced in a number of federal government agencies as a systemic measure for selecting and checking personnel when allowing them to conduct operational-search activities and work with information constituting a state secret. A similar …
Legal aspects of using a polygraph when working with personnel.Далее …
Legal aspects of the use of chemical traps.
Legal aspects of using chemical traps. Legal aspects of using chemical traps. Legal aspects of using chemical traps. V. Pogulyaev Information protection. Confidential No. 3, 2004 The use of chemicals as one of the measures to ensure the safety of objects helps to prevent and more quickly solve many categories of crimes. In detective films, …
Night vision devices: history of generations..
Night vision devices: history of generations.. Night vision devices: history of generations. Salikov Vyacheslav Lvovich NIGHT VISION DEVICES: HISTORY OF GENERATIONS The imperfection of one's own nature, compensated by the flexibility of the intellect, continually pushed man to search. The desire to fly like a bird, swim like a fish, or, say, see at night …
New generation night vision devices..
New generation night vision devices.. New generation night vision devices. VOLKOV Viktor Genrikhovich, Candidate of Technical Sciences, Associate Professor NEW GENERATION NIGHT VISION DEVICES Night vision devices (NVD) are designed for observation and aiming in the dark — at dusk and at night. NVD appeared at the end of World War II and have since …
Charge-coupled devices. Design and basic principles of operation. Article updated 23.04 in 2023.
Charge-coupled devices. Design and basic operating principles. Sergey Ivanovich Neizvestny Oleg Yuryevich Nikulin CHARGE-COUPLED DEVICES. DESIGN AND BASIC OPERATING PRINCIPLES. Source: «Special Equipment» magazine History of development Charge-coupled devices (CCD) belong to the class of solid-state semiconductor receivers. The first receivers of this type were photodiodes and already at the dawn of their appearance they …
FAPSI Order N 158..
FAPSI Order No. 158.. FAPSI Order No. 158. FAPSI Order On approval of the Regulation on the procedure for the development, production, sale and use of cryptographic information protection tools with limited access, not containing information constituting a state secret dated September 23, 1999 N 158 Regulation On the procedure for the development, production, sale …
Order of the People's Commissar of Internal Affairs of the USSR No. 7658 for 1938.
Order of the People's Commissar of Internal Affairs of the USSR No. 7658 for 1938. Order of the People's Commissar of Internal Affairs of the USSR No. 7658 for 1938 7658 TOP SECRET ORDER OF THE PEOPLE'S COMMISSAR OF INTERNAL AFFAIRS OF THE USSR for 1938 CONTENTS: 00822-00826. Sent to appropriate authorities. 00827. On the …
Order of the People's Commissar of Internal Affairs of the USSR No. 7658 for 1938.Далее …
Application of DNAR for detection of explosives.
Application of DYAKR for detection of explosives.. Application of DYAKR for detection of explosives. GRECHISHKIN Vadim Sergeevich, Doctor of Physical and Mathematical Sciences, Professor, SHPILEVOI Andrey Alekseevich, Candidate of Physical and Mathematical Sciences, Associate Professor,PERSICHKIN Andrey Andreevich. USE OF DYAKR FOR DETECTING EXPLOSIVES One of the most reliable methods for detecting narcotics and explosives …
The use of metallized fabrics of the METACRON series for protection against electromagnetic radiation.
Application of metallized fabrics of the METACRON series for protection against electromagnetic radiation. Application of metallized fabrics of the METACRON series for protection against electromagnetic radiation. Application of metallized fabrics of the Metacron series» for protection against electromagnetic radiation A.V. Mareichev, Ph.D. in Engineering, Director of NPP Tekhnostil Over the past decades, the total intensity …
Application of the dimensional ontology method in selecting means of technical protection of information from unauthorized access.
Application of the dimensional ontology method in selecting means of technical protection of information from unauthorized access. Application of the dimensional ontology method in selecting means of technical protection of information from unauthorized access. NAGORNY Sergey Ivanovich DONTSOV Vadim Vladimirovich, Candidate of Technical Sciences, Senior Researcher Application of the dimensional ontology method in selecting means …
Application of satellite radio navigation methods to create systems and complexes of technical means for determining the location of moving objects.
Application of satellite radio navigation methods to create systems and complexes of technical means for determining the location of moving objects.. Application of satellite radio navigation methods to create systems and complexes of technical means for determining the location of moving objects. Petrov Nikolay Nikolaevich, Candidate of Technical Sciences APPLICATION OF SATELLITE RADIONAVIGATION METHODS FOR …
Use of a polygraph in ensuring the security of a commercial bank.
Using a polygraph to ensure the security of a commercial bank. The development of market relations in Russia and the emergence of commercial enterprises of various forms of ownership have led to the emergence of a new class of crimes in the country, which have existed abroad for many decades and are united by the …
Use of a polygraph in ensuring the security of a commercial bank.Далее …
Use of the polygraph in Poland.
The use of the polygraph in Poland. Attention to the applied use of the polygraph appeared in Poland before the Second World War, when this device was purchased by the Institute of Mental Hygiene in Warsaw. Although it is not known whether the polygraph was used in criminal investigations before the war, nevertheless, such a …
The use of the polygraph in Russia: order must be restored.
Use of the polygraph in Russia In December 1994, the Ministry of Internal Affairs of Russia officially put the method of interrogation using a polygraph (hereinafter — IIP) into service of its operational units. Now, fifteen years later, the Ministry of Internal Affairs is the largest Russian user of the polygraph in law enforcement practice …
The use of the polygraph in Russia: order must be restored.Далее …
Application of psychophysiological method of lie detection in Japan.
Application of psychophysiological method of lie detection in Japan. Application of psychophysiological method of lie detection in Japan Yu. I. Kholodny Doctor of Law, Candidate of Psychological Sciences (Bauman Moscow State Technical University) Application of psychophysiological method of lie detection in Japan Source: Vestnik Kriminalisticy (issue 4(28)) The development of the psychophysiological method of lie …
Application of psychophysiological method of lie detection in Japan.Далее …
Application of vector signal analyzers in radio monitoring systems.
Application of vector signal analyzers in radio monitoring systems.. Application of vector signal analyzers in radio monitoring systems. SILANTIEV Vladimir Anatolyevich, Candidate of Technical Sciences USE OF VECTOR SIGNAL ANALYZERS IN RADIO CONTROL SYSTEMS Vector signal analyzers were created to study complex radio signals, such as signals with digital quadrature modulation, as well as …
Application of vector signal analyzers in radio monitoring systems.Далее …
The principles of operation of the GPS system and its use.
GPS system operation principles and its use. GPS system operation principles and its use. GPS system operation principles and its use. S. Markov, KNUSA. Introduction. Modern approaches to the creation of cadastral databases allow the widespread use of modern methods of geodetic measurements, primarily GPS — technologies. The satellite radio navigation system or, as it …
The principles of operation of the GPS system and its use.Далее …
Signs of authenticity of banknotes and determination of the method of production of counterfeit banknotes.
Signs of authenticity of banknotes and determination of the method of manufacturing counterfeit banknotes.. Signs of authenticity of banknotes and determination of the method of manufacturing counterfeit banknotes. Signs of authenticity of banknotes and determination of the method of manufacturing counterfeit banknotes Source: There are several approaches to solving the problem of checking banknotes for …
Signs that you may be being eavesdropped on.
Signs that you may be being eavesdropped. Signs that you may be being eavesdropped James M. Atkinson, Granite Island Group Signs that you may be being eavesdropped Obvious warning signs of covert eavesdropping or bookmarking. 1. Your competitors may know your professional secrets or confidential business matters. This is the most common indicator. Theft of …
Problems of combating radio-controlled explosive devices.
Problems of combating radio-controlled explosive devices.. Problems of combating radio-controlled explosive devices. ISKHAKOV Boris Simukovich, KARGASHIN Viktor Leonidovich, Candidate of Technical Sciences YUDIN Leonid Mikhailovich, Candidate of Technical Sciences PROBLEMS OF COMBATING RADIO-CONTROLLED EXPLOSIVE DEVICES In modern Russia, the lives of prominent political figures and leading executives of banking and commercial structures are constantly …
Problems of combating radio-controlled explosive devices.Далее …
Problems with the use of alarm systems in the UK.
Problems of using alarm systems in the UK. Problems of using alarm systems in the UK. International Security Review.- 1995 .- The alarm Special issue.- P. 5, 6. Problems of using alarm systems in the UK The International Security Review magazine reports on the use of alarm systems to combat crime in the UK and …
Problems and solutions to the problem of detecting modern voice recorders.
Problems and solutions to the problem of detecting modern voice recorders.. Problems and solutions to the problem of detecting modern voice recorders. Problems and solutions to the problem of detecting modern voice recorders. Gudkov Sergey Alexandrovich Special equipment 2001, No. 3 The complexity of the task of detecting modern voice recorders is that, on the …
Problems and solutions to the problem of detecting modern voice recorders.Далее …
Problems of detection and identification of radio signals of means of covert information control. Part 2.
Problems of detection and identification of radio signals of covert information control means. Part 2.. Problems of detection and identification of radio signals of covert information control means Kargashin Viktor Leonidovich Candidate of Technical Sciences Special Equipment, No. 4, 2000 Part 2. Efficiency of multichannel receivers As noted in the first article, signals from special …
Problems of using non-lethal weapons.
Problems of using non-lethal weapons. Problems of using non-lethal weapons. Jane's Defence Weekly.- 1996 .- 25, №10.-P. 6; № 13 .- P. 6. Jane's Defence Contracts.- 1996 .- November.- P. 4,5. Problems of using «non-lethal weapons» As noted in Jane's Defence Weekly, there has been a debate for over two years about which name for …
Design and manufacture of highly mobile special-purpose robots using modern CAD systems.
Design and manufacture of highly passable special-purpose mobile robots using modern CAD systems.. Design and manufacture of highly passable special-purpose mobile robots using modern CAD systems. Design and manufacture of highly passable special-purpose mobile robots using modern CAD systems Authors: Oleg Maslov, Andrey Puzanov, Konstantin Kuvanov, Oleg Platov (OAO SKB PA, Kovrov) The mind …
Design and manufacture of highly mobile special-purpose robots using modern CAD systems.Далее …
Parabens Device Seizure portable device expertise program.
Parabens Device Seizure portable device examination program. Parabens Device Seizure portable device examination program Parabens portable device examination program Device Seizure» Parabens Device Seizure main window. Digital forensics has taken a giant step forward with the evolution of Device Seizure. By combining PDA Seizure & Cell Seizure technologies, Paraben has provided investigators with a powerful …
Parabens Device Seizure portable device expertise program.Далее …
Counteraction to explosive devices with radio fuses.
Counteraction to explosive devices with radio fuses. Counteraction to explosive devices with radio fuses According to statistics, in the vast majority of cases, explosive devices (ED) with radio fuses (RF) were used to destroy slow-moving or stationary objects. For this purpose, moments were chosen when the target of the attack was entering or leaving the …
Radio headsets for special applications of portable short-range VHF radio communications.
Radio headsets for special applications of portable short-range VHF radio communications. Radio headsets for special applications of portable short-range VHF radio communications. Radio headsets for special applications of portable short-range VHF radio communications. 1. Classification. The most important attribute of portable VHF radio communication equipment is a radio headset, which is, as a rule, a …
Radio headsets for special applications of portable short-range VHF radio communications.Далее …
Ground surveillance radar station.
Ground surveillance radar. Ground surveillance radar VINITI, 1996 Ground surveillance radar Ground surveillance radar EL/M-2140 by Eita Electronics Industries— is a wide-band radar that automatically detects armored vehicles, light vehicles and people. Any sector within 10 to 380° can be scanned with a selectable scan speed of up to 4 rpm. Seven scales can be …
Radiometer for detection of alpha-emitting aerosols in indoor air.
Radiometer for detecting alpha-emitting aerosols in indoor air.. Radiometer for detecting alpha-emitting aerosols in indoor air. TIKHONOV Andrey Anatolyevich RADIOMETER FOR DETECTING ALPHA-EMITTING AEROSOLS IN INDOOR AIR Traditionally, when the task of protecting an object from the possible use of radioactive substances for terrorist purposes arises, technical means are proposed that allow detecting radioactive sources …
Radiometer for detection of alpha-emitting aerosols in indoor air.Далее …
IPSA 2 radio transmitter connected to a telephone line.
IPSA 2 radio transmitter connected to a telephone line. IPSA 2 radio transmitter connected to a telephone line. VINITI, 1996 IPSA 2 radio transmitter connected to a telephone line. IPSA 2 transmitterVHF range, connected in parallel to the telephone line, is designed for government services and police in strict accordance with the standards for devices …
IPSA 2 radio transmitter connected to a telephone line.Далее …
Radio detonators.
Radio fuses. Recently, when carrying out terrorist acts in populated areas using explosive devices, devices equipped with radio fuses are becoming increasingly widespread. This trend is due to the fact that the detonation of explosive charges by electrical means using a wire line in a populated area causes a whole series of technical difficulties associated …
Prices for TSCM services provided by Granite Island Group.
Prices for TSCM services provided by Granite Island Group. Prices for TSCM services provided by Granite Island Group James M. Atkinson, Granite Island Group Prices for TSCM services provided by Granite Island Group Granite Island Group offers TSCM services at the following prices (plus expenses): $3,750 per day for the first day (minimum two days …
Prices for TSCM services provided by Granite Island Group.Далее …
Order of the Government of the Russian Federation of February 28, 1996 No. 286-r.
Order of the Government of the Russian Federation of February 28, 1996 N 286-r. Order of the Government of the Russian Federation of February 28, 1996 N 286-r Order of the Government of the Russian Federation of February 28, 1996 N 286-r In accordance with the Decree of the President of the Russian Federation of …
Order of the Government of the Russian Federation of February 28, 1996 No. 286-r.Далее …
DEVELOPMENT, PRODUCTION AND SUPPLY OF INTELLIGENCE TECHNICAL MEANS. Part 2.
Principles of upgrading computers for harsh operating conditions Until recently, it was considered common practice when preparing technical specifications for military equipment to assume that it could operate in all conceivable operating conditions. Such equipment had to meet the most stringent standards for heat and vibration resistance and resistance to electromagnetic interference. With the current …
DEVELOPMENT, PRODUCTION AND SUPPLY OF INTELLIGENCE TECHNICAL MEANS. Part 2.Далее …
Development of a system for protecting confidential information.
Development of a system for protecting confidential information.. Development of a system for protecting confidential information. Development of a system for protecting confidential information Stolyarov Nikolay Vladimirovich Source— security.meganet.md Disclosure of CI means intentional or careless actions of persons admitted to CI, leading to premature dissemination of said information among persons, not caused by official …
Development of a system for protecting confidential information.Далее …
Intelligence at the Service of Your Enterprise Part 1
Intelligence at the service of your enterprise. 1. INFORMATION — MATERIAL OF OUR EPOCH Information is everywhere Imagine.. 7:30 in the morning. Jean Martin wakes up to the sound of the radio transmitting a short news bulletin: «Unrest in the Caucasus, 30 dead; oil tanker shipwrecked off the coast of California — there is a …
Intelligence at the Service of Your Enterprise Part 1Далее …
Recommendations for assessing the security of confidential information from leakage due to EMI.
Recommendations for assessing the security of confidential information from leakage due to PEMI.. Recommendations for assessing the security of confidential information from leakage due to PEMI. Recommendations for assessing the security of confidential information from leakage due to PEMI. E. V. Kurenkov, A. V. Lysov, A. N. Ostapenko FSUE «NPP «Gamma», VIKA im. A. F. …
Controlix Vision X-ray system for inspection of baggage and small items.
Controlix Vision X-ray system for baggage and small cargo screening. Controlix Vision X-ray system for baggage and small cargo screening Controlix Vision X-ray system for baggage and small cargo screening The Controlix Vision system by Shiumberger Industries (France) is a new generation of screening and detection equipment. It is designed for fast and efficient screening …
Controlix Vision X-ray system for inspection of baggage and small items.Далее …
SCRF solution according to the DECT standard.
State Commission on Radio Frequencies (SCRF) decision on the DECT standard. State Commission on Radio Frequencies (SCRF) decision on the DECT standard State Commission on Radio Frequencies (SCRF) decision on the DECT standard: On the conditions for using the 1880-1900 MHz radio frequency band by DECT equipment In recent years, DECT equipment has become widespread …