
Basic principles for creating a system for minimizing information risks at a large enterprise.
Introduction
In a market economy, commercial enterprises constantly operate under risk.
This means that at any given time there are non-zero probabilities of occurrence of events undesirable for commercial enterprises related to their direct activities.
These events can be very diverse in content, for example, non-repayment of loans by borrowers, changes in interest rates, failure of automated systems, etc.
Therefore, minimizing unexpected losses when undesirable events occur is a pressing issue for any commercial enterprise.
An analysis of well-known domestic and foreign literature shows that it is possible to reduce the risks of a commercial enterprise by ensuring its physical and information security.
In this case, physical security of a commercial enterprise is understood as a state in which the maximum level of protection of the enterprise's facilities, resources and personnel from possible physical impacts is ensured, and information security— a condition that ensures the maximum level of protection for a commercial enterprise from the leakage or destruction of vital information, the use of biased information in its daily activities, the dissemination of unfavorable or dangerous information in the external environment, and the receipt of false confidential information by the enterprise's management.
Thus, the information security of a commercial enterprise will be ensured if minimal information risks are ensured, namely: leakage and destruction of information necessary for the functioning of the enterprise, use of biased information in everyday activities, lack of information necessary for making the right decision (including confidential information) by the management of the enterprise, as well as dissemination by someone in the external environment of information that is unfavorable or dangerous for the activities of the enterprise.
This will ensure the achievement of one of the most important goals of the enterprise — minimization of commercial risks associated with the operations carried out by this enterprise.
To solve this problem from the point of view of a systems approach, it is advisable to develop and implement at a commercial enterprise a system for minimizing information risks, which is an interconnected set of bodies, means, methods and measures that ensure the minimization of risks of leakage and destruction of information necessary for the functioning of the enterprise, the use of biased information in everyday activities, the lack of information necessary for making the right decision by the enterprise management (including confidential information), as well as the dissemination by someone in the external environment of information that is unfavorable or dangerous for the enterprise's activities.
Justification of the structure of the information risk minimization system
As noted earlier, the main information risks of any commercial enterprise, including a large commercial enterprise, are:
- risk of leakage and destruction of information necessary for the functioning of the enterprise;
- risk of using biased information in the activities of the enterprise;
- risk of the lack of necessary (including confidential) information by the management of the enterprise to make the right decision;
- risk of dissemination by someone in the external environment of information that is unfavorable or dangerous for the enterprise.
An analysis of the above risks shows that they are associated with confidential information (risk of leakage and destruction of information, risk of the company's management not having the necessary information) and, mainly, with ordinary information (risk of using biased information in the company's activities, risk of someone disseminating unfavorable or dangerous information).
In this case, the risk of leakage and destruction is associated with the company's own confidential information, and the risk of absence is associated with the necessary confidential information of other commercial structures and enterprises.
Therefore, eliminating these risks in the activities of the enterprise requires solving specific tasks for each of them, which do not intersect, since they have different sources of this information.
Since the risk of using biased information in the daily activities of a commercial enterprise is mainly related to the quality of the process of collecting it and is manageable, the risk of someone disseminating information that is disadvantageous or dangerous for the enterprise can be caused by a fairly large complex of external and internal reasons, for example, the leakage of some confidential information from a commercial enterprise, the target setting and tasks currently being solved by competing enterprises, etc.
Obviously, most of the reasons can be eliminated by ensuring the protection of confidential information in a commercial enterprise, as well as by collecting and providing the management of a commercial enterprise with the necessary confidential information about the plans of competing enterprises, the tasks they are currently solving, etc.
Another part of the poorly taken into account reasons, for example, personal hostility towards the head of a commercial enterprise, deterioration of commercial relations between enterprises, can lead to the appearance in the media of unfavorable, and in some cases, dangerous information for the enterprise.
Therefore, in order to eliminate or at least reduce the risk of dissemination of this information by competing enterprises, it is necessary to proactively disseminate some true information, and in some cases, disinformation.
Thus, eliminating the above information risks of a commercial enterprise requires solving a variety of sets of tasks that differ in purpose and content.
The information risk minimization system should include the following subsystems:
- information protection subsystem;
- information issuance subsystem;
- information research subsystem;
- information collection subsystem;
- a control subsystem designed to implement control of subsystems within the system.
The main tasks solved by the control subsystem are:
- analysis of the current state of subsystems based on information received from the subsystems:
- development of control actions based on existing information and information received from the management of a commercial enterprise, aimed at solving global and local problems facing the enterprise;
- communicating the relevant control actions to the subsystems;
- monitoring changes in the current state of the subsystems during the implementation of control actions and, if necessary, issuing corrective control actions.
Figure 1 shows the relationship between the information risks of a commercial enterprise and the subsystems that make up the information risk minimization system.

Fig. 1.
Information security subsystem
The main tasks solved by the information security subsystem are:
- identifying information subject to protection;
- determining sources that possess, own, or contain this information;
- identifying methods of unauthorized access to this information;
- development and implementation of organizational and technical measures to protect confidential information.
Information of a commercial enterprise can be of the following four levels of importance:
- vital, i.e. information, the leakage or destruction of which threatens the very existence of the enterprise;
- important, i.e. information, the leakage or destruction of which leads to large costs;
- useful, i.e. information, the leakage or destruction of which causes some damage, but the enterprise can function quite effectively after this;
- insignificant, i.e. information, the leakage or destruction of which does not cause damage to the enterprise and does not affect the process of its functioning.
Obviously, information of the first three levels of importance must be protected, and the degree of protection should, in general, be determined by the level of importance of the information.
This is mainly due to the fact that the level of protection is directly related to the cost of its implementation, so it is generally economically impractical to protect information with expensive means of protection if its leakage or destruction leads to insignificant damage.
Information of the first three levels, as a rule, refers to a commercial secret and is determined by the head of the enterprise in accordance with the Decree of the Government of the Russian Federation of 5.12.91 No. 35 «On the list of information that cannot constitute a commercial secret».
The procedure for identifying information constituting a commercial secret, determining sources possessing, holding or containing this information should be as follows.
By order of a commercial enterprise, heads of structural divisions are charged with the responsibility of carrying out work to determine specific information constituting a commercial secret in their areas of work, persons admitted to this information, as well as carriers of this information.
The result of this work should be a «List of information constituting a commercial secret of the enterprise» approved by the head of the enterprise, indicating such information for each of the structural divisions; persons who are the bearers of this information; documents containing this information, as well as other (technical) carriers of this information, if any.
When identifying information constituting a commercial secret, it is necessary to take into account that each structural division of a commercial enterprise is characterized by a certain selection of partners, clients, etc. and is not interested in showing, for example, to competing enterprises, its information portrait, since this display can lead to a violation of the stability of the functioning of the division and a weakening of its competitiveness.
Therefore, information of this nature should also be classified as a commercial secret.
After identifying information constituting a commercial secret and determining the sources that possess, own or contain this information, methods of unauthorized access to this information are identified by selecting methods from the set of basic methods of unauthorized access to sources of confidential information shown in Fig. 2.
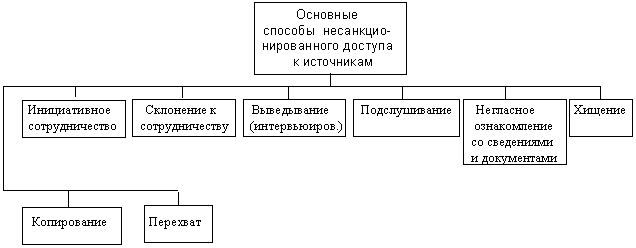
Fig. 2.
Appendix 1 presents the content of the main methods of unauthorized access to confidential information, taken into account when creating an information security subsystem, and provides data on the ratio of unauthorized access methods, based on foreign press materials.
Knowledge of the methods of unauthorized access to confidential information allows for the correct development and implementation of organizational and technical measures to protect this information.
From the above it follows that the main channels for leakage of confidential information are employees of a commercial organization, documents and technical means of processing and transmitting information.
As foreign and domestic experience shows, despite the increasingly widespread introduction of new information technologies into the practice of commercial enterprises, the main source of leakage of confidential information are employees of these enterprises.
Here it is appropriate to cite the statement of Italian psychologists that of all employees of any company: 25% are honest people, 25% are waiting for a convenient opportunity to disclose secrets and 50% will act depending on the circumstances.
Obviously, in our country these figures are unlikely to differ for the better, since there are no political or economic reasons for this.
Therefore, in relation to such a situation, it is necessary to understand that it is practically impossible to create conditions at a commercial enterprise that completely exclude unauthorized access to this source of confidential information; it is only possible to significantly reduce its role among other sources of leakage of confidential information.
To this end, the enterprise must solve the following tasks:
- create a legal basis for ensuring the protection of information by implementing:
- amending the Charter of the enterprise with amendments that give the management of the enterprise the right to:
- create organizational structures for the protection of commercial secrets;
- issue regulatory and administrative documents governing the procedure for determining information constituting a commercial secret and the mechanisms for protecting it;
- include requirements for the protection of commercial secrets in contracts for all types of business activities;
- demand protection of the interests of the enterprise before state and judicial authorities;
- dispose of information that is the property of the enterprise for the purpose of deriving benefits and preventing economic damage to the enterprise;
- supplementing the «Collective Agreement», if it is being developed at the enterprise, with provisions that establish the responsibilities of the administration and employees of the enterprise related to the development and implementation of measures to identify and protect commercial secrets, compliance at the enterprise with requirements for the protection of commercial secrets, bringing violators of requirements for the protection of commercial secrets to administrative or criminal liability in accordance with applicable law, instructing persons hired on the rules for maintaining commercial secrets with the execution of a written obligation not to disclose them, removing persons violating the established requirements for their protection from work related to commercial secrets;
- supplementing the «Employment Contract» with requirements for the protection of commercial secrets, if the contract is concluded in writing; when concluding a contract orally, communicating to the person with whom the employment contract is concluded the internal regulations, including requirements for the protection of commercial secrets;
- communicating to each employee of the enterprise the «List of information constituting a commercial secret of the enterprise» in the part concerning;
- creating favorable internal conditions at the enterprise for the preservation of commercial secrets by implementing:
- identifying and dismissing people who are waiting for a convenient opportunity to disclose commercial secrets (according to estimates by Italian psychologists, the share of such people in almost any company is about 25% of the total number of employees). For this purpose, data from the company's personnel department, the results of employee studies, overt and covert control over their activities, etc. can be used;
- identifying and carefully monitoring the activities of employees who are dissatisfied with something or who are in constant need of a livelihood, who work part-time at an enterprise or intend to transfer to work at another enterprise;
- formation of a psychological climate at the enterprise and in its structural divisions, in which it would be convenient and profitable for the employees of the enterprise to comply with the requirements for the protection of commercial secrets. For this purpose, for example, material incentives can be used for employees who do not violate the requirements for the protection of commercial secrets within a predetermined period;
- organization and implementation of a system of continuous training of the enterprise employees in the rules and procedures for working with confidential information, and conducting negotiations. The training of employees should involve not only the acquisition and systematic maintenance of high-level skills in working with confidential information, but also their education in terms of a deep conviction in the need to comply with the requirements for the protection of commercial secrets;
- conducting conversations with employees leaving, the main purpose of which is to prevent the leakage of confidential information or its misuse. During the conversations, it should be especially emphasized that each employee leaving is obliged not to disclose commercial secrets that became known to him/her during his/her work at the enterprise, and this obligation should be supported by a non-disclosure agreement on confidential information known to the employee;
- conducting special inspections of office premises, the purpose of which is to identify electronic eavesdropping devices introduced into these premises.
Special checks must be carried out using special methods and include the following types of work:
- special inspection and testing using technical means of the surface of walls, ceilings, floors, doors and window frames, as well as furniture, interior items, souvenirs, etc. The following equipment and technology is used to carry it out: a non-linear locator, a portable X-ray complex, a metal detector, a void detector, an electromagnetic field indicator, a radio frequency meter, as well as auxiliary inspection equipment;
- visual inspection and testing using technical means of the electronic devices located there. The following are used: a portable X-ray complex, an electromagnetic field indicator, a radio frequency meter and a set of magnifying glasses;
- visual inspection and testing using technical means of wire lines (electrical network, subscriber telephone network, clock system, fire and security alarm systems, etc.). To carry out this type of work, wire line monitoring equipment, an electromagnetic field indicator and a radio frequency meter are used;
- radio control (radio monitoring) of premises. This type of work is carried out using software and hardware control systems or conventional scanner receivers. Spectrum analyzers are used to analyze the signal structure. In order to prevent eavesdropping during a particularly important event (meeting, negotiations, meeting, etc.), it is advisable to carry out radio control of the premises allocated for this purpose before and during the event, as well as to set up targeted and noise interference using special means during the event;
- collecting and correctly responding to information about attempts at various contacts with employees of the enterprise aimed at obtaining confidential information.
The next most important source of confidential information leakage are various kinds of documents.
Here it is necessary to take into account that the rather rapid development of information technologies has led to the emergence of new types of document information carriers: computer printouts, magnetic information carriers, etc.
At the same time, the importance of traditional types of paper documents in commercial activities has not diminished: contracts, letters, analytical reviews, etc.
The emergence of new document information carriers has led not only to new difficulties in solving the problem of ensuring the protection of confidential information from unauthorized access to its contents, but also to new opportunities to ensure guaranteed protection of this information.
Here we are talking primarily about storing especially important document information on magnetic media in a form transformed using cryptographic transformations.
Therefore, to prevent unauthorized access to this source of confidential information, both traditional and non-traditional methods can be used, namely:
- implementing security of premises and offices, as well as effective entry control over access to them;
- careful selection of employees to work in the office work system;
- implementation of a clear organization of the office work system, defining the functions of ensuring the security of confidential information when working with documents and technical media and methods of performing functions when documenting information, accounting for documents, organizing document flow, ensuring the reliable storage of documents and their timely destruction, as well as checking the availability of documents and monitoring the timeliness and correctness of their execution;
- development and implementation of documents regulating all user actions when working with various documents containing confidential information and technical media;
- storage of confidential documentary information on magnetic media and in the memory of a personal computer in a form transformed using cryptographic transformations. For this purpose, the Russian data encryption standard GOST 28147 — 89, as well as other cryptographic transformations, can be used quite effectively.
Technical means of processing and transmitting information are also the main source of leakage of confidential information.
This is due to the fact that in the activities of commercial enterprises, along with traditionally used means of processing and transmitting information, for example, radio and wire telephone communications, telex and fax communications, new computer information technologies are increasingly being used, including automated workstations, local and global computer networks.
It should be noted that, regardless of the purpose of the means of processing and transmitting information and the tasks solved by this means, unauthorized access to information is possible as a result of the following actions by an intruder:
- eavesdropping on information transmitted over wired telephone lines using pre-installed telephone bugs;
- remotely retrieving confidential information from technical means of processing and transmitting information (usually from a personal computer) using pre-installed hardware bugs;
- passive reception of signals transmitted in computer networks, parasitic electromagnetic radiation and interference generated by various means of processing and transmitting information;
- copying (theft) of confidential information stored in the memory of a personal computer.
To ensure the protection of confidential information under these conditions, the following must be done:
- introduce into practice the implementation of special checks of personal computers for the purpose of identifying and eliminating hardware bugs, as well as periodic special checks of telephone sets, telephone sockets and telephone lines of a commercial enterprise for the purpose of identifying and eliminating telephone bugs;
- ensure cryptographic protection of telephone channels through which confidential information may be transmitted or may be transmitted, for example, telephone channels between the head of a commercial enterprise and the heads of structural divisions;
- ensure cryptographic protection of communication channels of the computer network through which confidential information is exchanged;
- protect computer network objects from unauthorized access to stored confidential information;
- neutralize parasitic electromagnetic radiation and interference using special technical solutions and technical means of active protection.
Appendix 2 examines the basic principles of cryptographic transformation of analog and digital telephone messages, presents data on a comparative assessment of the American federal encryption standard DES and the Russian standard GOST 28147-89, as well as the main characteristics of the means of ensuring cryptographic protection of telephone messages available on the Russian market.
Appendix 3 examines the basic principles of protecting computer networks from unauthorized access to stored and transmitted information, new algorithms for cryptographic transformation of messages transmitted in computer networks, and the formation of an electronic signature code for these messages.
Information output subsystem
The information output subsystem is designed for targeted output of information to the external environment, creating favorable conditions for the effective functioning of a commercial enterprise.
This information includes two components: information issued to the external environment for the purpose of increasing demand for the services or products offered, and information issued to the external environment for the purpose of creating a certain level of awareness necessary for a commercial enterprise.
Obviously, information issued to the external environment for the purpose of increasing demand for the services and products offered should include advertising of the products or services offered, public relations, etc., and its issuance should be handled by the advertising department or a division that carries out tasks similar to those of the advertising department.
Information issued to the external environment for the purpose of creating a certain level of awareness necessary for a commercial enterprise must be formed as a result of an analysis of the environment and the adoption of certain decisions by the management of the commercial enterprise.
For this purpose, the following activities must be carried out:
- information about the commercial enterprise must be determined, which, as a result of dissemination in the external environment, would contribute to the creation of favorable conditions for solving the current and future tasks facing the enterprise;
- an analysis was conducted of the degree of correspondence of this information with the information about the commercial enterprise currently available in the external environment;
- the information required for issuance to the external environment was identified and the procedure for issuing it was determined.
Examples of such information are information that helps create an image of a strong security service of a commercial enterprise, for example, information about the use of the latest means for cryptographic protection of data in the memory of a personal computer, which provide guaranteed stability, which can prevent attempts to copy and steal this data, and even disinformation.
Information collection subsystem
The task of the information collection subsystem is to provide the management of a commercial enterprise at the right time with objective information that allows them to make the right decisions.
An analysis of the general tasks facing a commercial enterprise shows that the initial collection of information should be carried out in the following areas with the formation of appropriate databases:
- current and potential competitors;
- customer requests, distribution channels for products and services;
- production and use of products and services;
- laws, new legislative and regulatory provisions affecting the interests of a commercial enterprise,
- financial and material resources necessary for the normal operation of the enterprise;
- general trends in the political, economic, social and demographic spheres;
- other factors influencing the activities of the enterprise.
The main sources of information necessary for the formation of databases are:
- clients, clients' partners, their leading specialists and other employees;
- suppliers of various equipment to a commercial enterprise in accordance with their areas of activity, for example, suppliers of automation systems and equipment, security alarm systems and equipment, etc.;
- partners;
- advertising agents, representatives of public relations companies, mailing companies, etc.;
- sales agents of various firms and enterprises;
- consultants and experts attracted by a commercial enterprise to solve various problems;
- local, national and international press;
- special publications and various databases (banks);
- exhibitions and conferences;
- regulatory documents.
The sources indicated can be combined, taking into account their characteristics, into the following groups:
- general publications, special publications and databases (banks);
- clients, clients' partners (including leading specialists and other employees), equipment suppliers, partners and sales agents;
- advertising agents, representatives of public relations companies, mailing companies, consultants and experts, regulatory documents;
- exhibitions and conferences.
As practice shows, these groups of sources allow you to get the necessary information in the following ratio:
- the first group — about 30-40% of the necessary information;
- the second group — about 30-40% of the necessary information;
- the third group — about 10-15% of the necessary information;
- the fourth group — about 4-5% of the necessary information.
Thus, the specified sources of information allow you to obtain from 74 to 100% of the information necessary for making the right decisions.
Note that access to the first group of sources is the easiest and cheapest. Therefore, consideration of any new issue should begin with an analysis of periodicals covering the area of interest, if there are no special publications devoted to this issue. Often, this approach is the best for obtaining the information of interest, names and addresses of organizations.
All employees of the commercial enterprise who, by virtue of their official duties, may come into contact with representatives of third-party organizations should participate in obtaining information from the second group of sources. As a rule, the information obtained from these sources allows filling databases in the following ratio: 60% of the information pertains to the databases «competitors-market-resources», 15% — «technologies», 15% — «regulatory documents» (laws, legislative and regulatory provisions); 10% — «development trends».
Information from the third group of sources allows, mainly, filling the databases of regulatory documents and development trends.
The information from the fourth group of sources is small in volume compared to the information received from other groups of sources, but it is the most accurate. Therefore, extracting the greatest information benefit from visiting exhibitions and participating in conferences requires carrying out certain preparatory work, for example, studying catalogs, questions related to the subject of the exhibition, etc.
An analysis of the tasks solved by the information collection subsystem shows that the majority of these tasks can be solved by the marketing department of a commercial enterprise with the involvement of relevant specialists of this enterprise, as well as outside experts.
Information Research Subsystem
The Information Research Subsystem is designed to solve the following tasks:
- defining the information necessary for the management of a commercial enterprise to make effective fundamental decisions on expanding (conquering) markets for its goods and services in various conditions of the current situation;
- collection, analysis and provision of this information to the management of the enterprise.
The objects of interest of this system in general are:
- various types of activities of enterprises and organizations:
- production and production activities;
- scientific activities;
- trade and financial activities;
- intermediary activities;
- other types of activities;
- products and services:
- discoveries and inventions;
- manufacturing technology;
- industrial designs;
- technical projects and reports;
- know-how, etc.;
- information:
- on finances and prices;
- on resources;
- on suppliers and clients, etc.
Obtaining information on various types of activities of enterprises and organizations, their products and services offered, finances and prices, resources, suppliers and clients, etc. is carried out from the sources of this information.
An analysis of the available data allows us to establish, with some degree of generalization, that the main sources of such information are:
- employees of enterprises and organizations;
- documents received and sent by an enterprise or organization, as well as stored at the enterprise or organization;
- technical means of processing and transmitting information, as well as various communication lines;
- products of enterprises and organizations;
- industrial and production waste.
Obviously, based on the tasks being solved by a particular enterprise or organization, it is always possible to select the most significant ones from this set of sources.
The main methods of accessing the specified sources of information on various types of activities of enterprises and organizations, their products and services offered, finances and prices, resources, suppliers and clients, etc. are the following:
- proactive cooperation;
- inclination to cooperation;
- spying (interviewing);
- eavesdropping;
- covert familiarization with information and documents;
- theft;
- copying;
- interception;
- visual observation;
- photography.
Appendix 4 provides the content of these methods and the procedure for implementing some of them.
Regardless of the specific features of the confidential information being obtained, access to it must be achieved by consistently performing the following actions:
- a clear understanding of the content, volume, features, etc. of the information that must be obtained as a result of the activities being carried out;
- identifying the sources of the information of interest and ranking them according to the degree of completeness of possession, ownership, or content of this information;
- assessment of possible methods of access to sources of information of interest and selection of the most effective of them in the conditions of existing economic, technical, etc. restrictions;
- implementation of the selected methods of access to sources of information of interest with the possibility of their subsequent correction.
It should be noted that the high level of development of technologies in various fields of technology has led to the fact that the main volume of confidential information can now be obtained with the help of modern technical means of electronic intelligence, as well as special software.
This is due to the fact that with the help of such means it is possible to access such sources of confidential information as employees of enterprises and organizations, documents stored in the memory of the computer and displayed on monitor screens, technical means of processing and transmitting information.
The main of the most common technical means intended for the unauthorized extraction of confidential information, according to experts, are various electronic eavesdropping devicesinformation or so-called bookmarks. Appendix 5 provides some characteristics and features of such electronic devices.
The procedure for using electronic eavesdropping devices in the premises of interest depends significantly on the accessibility of these premises and the range of these devices available. Therefore, the most typical cases of using electronic eavesdropping devices (bugs) that may occur in practical activities are considered below.
1. The stage of construction and reconstruction of the facility.
The stage of construction or reconstruction of the facility is the most favorable for installing bugs, since there is virtually free and uncontrolled access to the premises, its lighting systems, alarms, communications, etc.
During this period, rather complex devices can be installed, including remote-controlled ones, using complex signals and cryptographic transformation of information for transmission. These are, as a rule, network bugs, radio bugs powered by an alternating current network or a telephone line, i.e. bugs with an unlimited operating time. They are installed in hard-to-reach places and are well camouflaged.
During the construction period, long-lasting radio stethoscopes can be built into the walls of the building. The accelerometer-type sensors used in the radio stethoscope detect vibrations that occur during conversations indoors, in the frequency range from 100 Hz to 10 kHz. The transmission range is about 500 m, and the service life is 10 years.
2. The stage of daily business activities of the enterprise, when access to the premises is not controlled.
In this case, acoustic bookmarks can be installed in the interiors of the premises, everyday objects, radio equipment, power outlets and electrical appliances, technical communication equipment and their connecting lines, etc.
It is most expedient to install bookmarks during preventive maintenance on power supply systems, communications and signaling, as well as during cleaning of premises. At the same time, installing a network bookmark instead of a regular socket takes several minutes, and replacing a regular extension cord with a similar device — several seconds.
During this period, telephone bugs can also be installed in the telephone case, telephone handset, telephone socket, and also directly in the telephone line path. In this case, replacing a regular microphone capsule with a similar one, but with a telephone bug installed in it, takes no more than 10 seconds.
3. The stage of daily activity of the enterprise, when access to the premises is controlled, but visitors can be in it for a short time.
The above is typical for offices, reception areas or break rooms of the management.
In this case, it is most appropriate to install bookmarks directly in the interior of the room, for example, under a chair or table, under a windowsill, behind a curtain, or use bookmarks camouflaged as a crumpled pack of cigarettes or a piece of cardboard that can be thrown into the trash. In addition, bookmarks can be installed by replacing objects that are constantly in the room with similar ones, but equipped with bookmarks.
4. The stage of daily activity of the enterprise, when access to the premises is impossible, but access to adjacent premises is not excluded.
In this case, it is advisable to use radio stethoscopes to access information, which allow obtaining the information of interest by picking up acoustic signals from the walls of the premises, external window panes, heating and water supply pipes.
In addition, telephone bugs can be installed in the telephone line path to the distribution box, which is usually located on the same floor as the room where the monitored telephone is installed, or in the telephone line path from the distribution box to the building's distribution board, which is usually located on the first floor or in the basement.
To access information processed in a personal computer without a direct connection to the personal computer, special systems can be used that allow the restoration of information displayed on the monitor screen as a result of analysis and appropriate processing of intercepted side electromagnetic radiation. Such systems include the 4625-COM-INT and RK-6630 systems, which have relatively small dimensions and weight (for example, the 4625-COM-INT system has dimensions of 25x53x35 cm and weighs 18 kg), but have quite large capabilities.
Appendix 1
Contents of the main methods of unauthorized access
to confidential information, taken into account when creating
an information security subsystem
Proactive cooperationis manifested in certain actions of persons who are dissatisfied with something or who are in dire need of means of subsistence, usually employed by a commercial enterprise, working somewhere part-time or intending to transfer to work at another enterprise. The fundamental possibility of the existence of such a method of unauthorized access to sources of confidential information is evidenced by the well-known statement of Italian psychologists that of all employees of any company, 25% are honest people, 25% of people are waiting for a convenient opportunity to disclose secrets and 50% of people will act depending on the circumstances.
Inducement to cooperate— this is, as a rule, a violent action on the part of the attackers. Persuasion to cooperate (recruitment) can be carried out by bribery, intimidation and blackmail. Very close to persuasion to cooperate is the luring of knowledgeable specialists of the enterprise to the side of the competing enterprise in order to master their knowledge.
Eavesdropping (interviewing) — this is the desire to obtain certain information under the guise of naive questions. Experience shows that such information can be most effectively and covertly obtained through the immediate circle of the heads of the commercial enterprise (secretaries, assistants, drivers, close friends, etc.).
Eavesdropping— a method of unauthorized access to confidential information based on the use of specially trained agents, informants and special eavesdropping equipment. Eavesdropping is one of the most common ways of obtaining confidential information, since when eavesdropping, human speech is directly perceived with its features, coloring, intonation, a certain emotional load, which is often no less important than the content of the speech itself, and the eavesdropped conversations themselves are perceived in real time and, to a certain extent, can allow the intruder to make certain decisions in a timely manner.
The following eavesdropping methods can currently be used most effectively:
- eavesdropping on conversations indoors or in a car using pre-installed acoustic bugs and portable sound recording devices;
- eavesdropping on conversations indoors using laser eavesdropping systems;
- eavesdropping on telephone conversations carried out over wired communication lines using pre-installed telephone bugs;
- remote retrieval of confidential information from technical means of processing and transmitting information (usually from a personal computer) using pre-installed hardware bugs.
Secret familiarization with information and documents— this is a method of obtaining confidential information to which the subject is not allowed, but under certain conditions he can gain access to all or part of this information.
The main reason for secret familiarization with information and documents is, as a rule, a low level of discipline at the enterprise, leaving documents containing commercial secrets on desks and in unlocked drawers, leaving information in the RAM of a personal computer after completing work, uncontrolled storage of diskettes with confidential information, etc. actions.
Secret familiarization also includes the censorship of mail of a commercial enterprise and personal correspondence.
Theft is a method of intentional illegal seizure of other people's documents and information. As a rule, the theft of documents and information is conditioned by certain conditions convenient for this.
The materials provided in one of the textbooks for students of the Law Faculty of Moscow State University present the following data, which are of interest when assessing theft as a method of unauthorized access to confidential information: 10% of people never steal, because it is incompatible with their morals; 10% of people steal at every opportunity, under any circumstances; 80% of people are usually honest, except in cases when there is a temptation to steal.
At the same time, the available materials indicate that theft can be carried out at almost any level in the hierarchy of officials of a commercial enterprise
Copying is a method of unauthorized access to confidential information by reproducing, repeating the original.
Analysis of the practice of criminal actions shows that documents, technical media, and personal computer data containing confidential information of interest to the intruder are subject to copying.
Interception— is a method of obtaining confidential information by passively receiving signals transmitted via communication channels of various physical natures, parasitic electromagnetic radiation and interference generated by various means of processing and transmitting information.
Data on the ratio of unauthorized access methods
| №№ |
Unauthorized access method |
Percentage |
| 1 | Proactive cooperation, inducement to cooperation, spying | 43 |
| 2 | Eavesdropping on telephone conversations | 5 |
| 3 | Theft of documents | 10 |
| 4 | Theft of information stored in a personal computer | 13 |
| 5 | Interception of information | 24 |
| 6 | Other methods | 5 |
Appendix 2
Cryptographic protection of telephone messages
The most effective way to protect telephone messages from unauthorized access is their cryptographic transformation.
Indeed, in order to hide the semantic content of a transmitted telephone message from intruders, this message must be changed in a certain way.
In this case, it must be changed in such a way that the restoration of the original message by an authorized subscriber would be very simple, and the restoration of the message by an intruder would be impossible or would require significant time and material costs, which would make the restoration process itself ineffective.
These are the properties that cryptographic transformations have, the purpose of which is to provide, using mathematical methods, such protection of transmitted confidential telephone messages that even if they are intercepted by intruders and processed by any means using the fastest supercomputers and the latest achievements of science and technology, the semantic content of the messages should be revealed only within a specified time, for example, within several decades.
General principles of cryptographic transformation of telephone messages
Let us consider the general principles of cryptographic transformation of telephone messages (see Fig. 1).
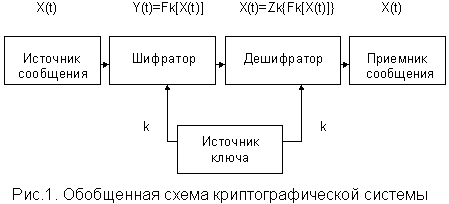
We will call the original telephone message, which is transmitted via a radio or wire channel, an open message and denote it X(t).
This message is sent to the cryptographic transformation (encryption) device, where the encrypted message Y(t) is formed using the following relationship
Y(t) = Fk[ X(t)],
where Fk[.] is the cryptographic transformation;
k is the cryptographic transformation key,
Here, the cryptographic transformation key is understood to be a certain parameter k, with the help of which a specific cryptographic transformation is selected Fk[.].
Obviously, the greater the power of the set of keys used for the cryptographic transformation K, the greater the number of cryptographic transformations that the telephone message X(t) can be subjected to, and, consequently, the greater the uncertainty of the attacker when determining the cryptographic transformation Fk[.] currently used.
Generally speaking, when encrypting a message X(t)cryptographic transformations must be used in which the degree of its protection would be determined only by the power of the set of keys of the cryptographic transformation K.
The encrypted message Y(t) is transmitted over a wired communication channel. At the receiving end, this message is decrypted in order to restore the open message using the following relationship
X(t) = Zk[Y(t)] = Zk{Fk[X(t)]},
where — Zk[.] — is the inverse transformation with respect to Fk[.].
Thus, the presence of identical keys k and cryptographic transformations Fk[.], Zk[.] among subscribers allows encryption and decryption of telephone messages without any particular difficulties.
It is obvious that in order to determine the methods of cryptographic transformation of telephone messages, it is necessary to have an idea of the processes that underlie their formation.
A telephone message is transmitted using electrical signals that are formed from acoustic signals by converting these acoustic signals into electrical signals by the telephone microphone, processing the electrical signals and amplifying them to the required level. At the receiving end, in the telephone, the electrical signals are processed and converted into acoustic signals using the telephone.
Any acoustic signal A(t) is characterized by duration and amplitude-frequency S(f) spectrum, i.e. the acoustic signal A(t) can be represented equivalently in both the time and frequency domains.
Note that the human ear can perceive an acoustic signal in the range from 15 Hz to 20 kHz, although there may be some individual differences. However, in order to maintain the recognizability of the subscriber's voice by timbre, purity and good intelligibility of sounds, it is absolutely not necessary to transmit an acoustic signal in this frequency range. As practice has shown, it is sufficient to use a frequency range from 300 Hz to 3400 Hz. This is the frequency bandwidth of standard telephone channels throughout the world.
Based on the time and frequency representations of the acoustic signal A(t), and, consequently, the open telephone message X(t), in practice, cryptographic transformations can be applied to the message itself X(t) or to its amplitude-frequency spectrum S(f).
All cryptographic transformations, from the point of view of security, can be divided into two groups.
The first group consists of computationally secure and provably secure cryptographic transformations, and the second — unconditionally secure cryptographic transformations.
Computationally secure and provably secure include cryptographic transformations whose security is determined by the computational complexity of solving some complex problem. The main difference between these cryptographic transformations is that in the first case there is reason to believe that the security is equivalent to the complexity of solving a difficult problem, while in the second case it is known that the security is at least greater. In the second case, proof must be provided that the disclosure of the transmitted encrypted message Y(t) is equivalent to solving a complex problem.
An example of computationally secure cryptographic transformations are complex cryptographic transformations composed of a large number of elementary operations and simple cryptographic transformations in such a way that an attacker needs Y(t) to decrypt the intercepted messagethere is nothing left to do but to apply the method of total testing of possible keys of cryptographic transformation, or, as it is also called, the brute force method. With the help of such cryptographic transformations, it is possible to provide guaranteed protection of the transmitted message X(t) from unauthorized access.
It is also possible to classify such simple cryptographic transformations as computationally strong cryptographic transformations, when used by an attacker for unauthorized access to the message X(t)it is necessary to use only certain algorithms for processing the message Y(t). These cryptographic transformations can only provide temporary resistance.
Unconditionally resistant cryptographic transformations are those whose resistance does not depend on either the computing power or the time that an attacker may have. That is, such cryptographic transformations that have the property of not providing an attacker with when intercepting a messageY(t) additional information regarding the transmitted telephone message X(t).
Note that it is very difficult to implement unconditionally secure cryptographic transformations and therefore they are not used in real telephone communication systems.
Cryptographic transformation of analog telephone messages
The simplest and most common method of cryptographic transformation of analog telephone messages is to split the messages X(t) into parts and transmit these parts in a certain order to the communication channel.
This method is as follows. The duration of the message X(t) (see Fig. 2) is divided into certain time intervals T of equal duration. Each such time interval is further divided into smaller time intervals of duration tau. In this case, for the value T/tau, as a rule, the condition n = T/tau = m…10m is satisfied, where m is some integer, m<10. Parts of the message X(t) at time intervals ( are recorded in the storage device, «mixed» with each other in accordance with the rule determined by the cryptographic transformation key k, and in the form of a signal Y(t)are issued into the communication channel. On the receiving side of the communication channel, where the mixing rule is known, since there is exactly the same cryptographic transformation key k, the «assembly» of the open message X(t) is carried out from the message Y(t).

The advantages of this method of cryptographic transformation include its relative simplicity and the possibility of transmitting an encrypted telephone message via standard telephone channels. However, this method allows only temporary resistance. This is due to the following. Since the open telephone message X(t) is continuous, then after recording the message Y(t) and allocating intervals of duration tau, the attacker has(the latter is easy enough to do, since there is a synchronizing signal in the communication channel) it becomes possible in principle to decrypt the message Y(t) even without knowing the key k used. For this purpose, it is possible to select intervals in such a way as to ensure the continuity of the received message at the junctions of these intervals. Obviously, with careful and painstaking work using special equipment, such continuity can be ensured fairly quickly, thereby isolating the open message X(t).
Therefore, it is advisable to use such cryptographic transformation of open telephone messages only in cases where the information is of no particular value or when its value is lost after a relatively short period of time.
Higher protection against unauthorized access can be ensured if the principle under consideration is applied to the frequency spectrum of the message X(t). For this purpose, the bandwidth of the telephone channel Fis divided by a system of bandpass filters into n frequency bands of width df, which are mixed according to some rule determined by the cryptographic transformation key k. The frequency bands are mixed at a rate of V cycles per second, i.e. one band permutation lasts 1/V c, after which it is replaced by the next one.
To increase protection against unauthorized access, after mixing the frequency bands, the frequency spectrum of the message Y(t) can be inverted.
Figure 3 illustrates the method under consideration. The upper part of Figure 3 shows the frequency spectrum of the message X(t), and the lower part shows the spectrum of the message Y(t) in one of the mixing cycles at n = 5.
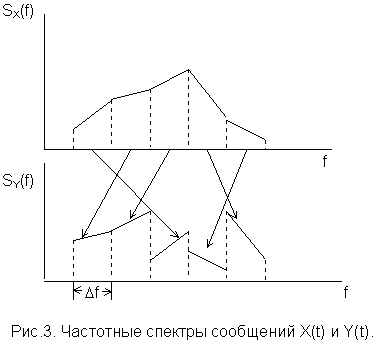
The considered method allows for higher protection of telephone messages from unauthorized access compared to the previous method, since to restore the open message X(t)In this case, the attacker must have additional data on the relative frequencies of sounds and their combinations in colloquial speech, the frequency spectra of voiced and voiceless sounds, and the formant structure of sounds. Table 1 contains data on the relative frequencies of some sounds and the boundaries of formant regions of sounds in Russian speech, which can be used by the attacker to restore intercepted telephone messages.
Table 1. Data on the relative frequencies of some sounds and the boundaries of formant regions
| Sound | Relative frequency of occurrence | 1st formant region, Hz | 2nd formant region, Hz |
| Vowel | |||
| a | 0.079 | 1100 — 1400 | — |
| and | 0.089 | 2800 — 4200 | — |
| o | 0 ,11 | 400 — 800 | — |
| y | 0.026 | 200 — 600 | — |
| s | 0.022 | 200 — 600 | 1500 — 2300 |
| e | 0.002 | 600 — ; 1000 | 1600 — 2500 |
| Consonant | |||
| z | 0.016 | 0 — 600 | 4200 — 8600 |
| w | 0.008 | 200 — ; 600 | 1350 — 6300 |
| l | 0.04 | 200 & #8212; 500 | 700 — 1100 |
| m | 0.031 | 0 — ; 400 | 1600 — 1850 |
| n | 0.069 | 0 — ; 400 | 1500 — 3400 |
| р | 0.05 | 200 & #8212; 1500 | — |
| s | 0.054 | 4200 — 8600 | — |
| f | 0.001 | 7000 — 12000 | — |
| х | 0.012 | 400 — 1200 | — |
| w | 0.008 | 1200 — 6300 | — |
It is obvious that the highest level of protection of telephone messages from unauthorized access can be ensured by combining the methods considered. In this case, time permutations will destroy the semantic structure, and frequency permutations will mix up vowel sounds.
The devices implementing the above methods are called scramblers. In this regard, the series of scramblers, for which the SCR — M1.2 scrambler was used as a base, is of particular interest. These scramblers implement the above methods of cryptographic transformation of analog telephone messages and are quite widely used in various government and commercial structures. Table 2 shows the main characteristics of some scramblers in this series.
Table 2. Main characteristics of scramblers created on the basis of the SCR-M1.2 scrambler
| Scrambler | Operating mode | Subscriber identification | Entering a session key | Power of multiple keys | Dimensions, mm | Weight, kg | Power supply |
| SCR-M1.2 | Duplex communication | Provided | Open key distribution method | 2E18 | 180x270x 40 | 1.5 | 220 V 50 Hz |
| SCR-M1.2mini | Duplex communication | Provided | Open key distribution method | 2E18 | 112x200x 30 | 0.8 | From a 9-15 V network adapter or battery pack |
| SCR-M1.2multi | Duplex communication | Can be provided at the customer's request | By open key distribution method | 2E18 | — | — | 220 V 50 Hz |
It should be noted that the methods considered cannot, in principle, provide guaranteed protection of analog telephone messages from unauthorized access, so it is advisable to use scramblers when the message is not of particular value.
In order to ensure guaranteed protection of transmitted telephone messages, it is necessary to use means implementing fundamentally different methods of cryptographic transformation of these messages. Such a means is, for example, the means of protecting telephone messages «IRIS», in which the transformation of an analog telephone message is carried out by imposing on this message some implementation of noise generated by a special generator. Since the number of noise implementations used is 1E8, and the implementations themselves are selected randomly and used once, this excludes the possibility for an intruder to determine the semantic content of the transmitted message over a sufficiently long period of time (about 1 year).
Cryptographic transformation of digital telephone messages
In practice, to transform a telephone message X(t) into digital form on the transmitting side and restore the message X(t)On the receiving side, speech codecs are used, which implement one of two methods of encoding telephone messages: forms and parameters.
The basis of digital telephony is currently the encoding of the message form, encoding of message parameters or, as they say, vocoder communication is used much less often. This is due to the fact that encoding the signal form allows you to preserve the individual characteristics of the human voice, to meet the requirements not only for intelligibility, but also for the naturalness of speech.
Pulse code modulation (PCM), differential PCM, delta modulation are widely used in signal form encoding.
Let's briefly consider the principles of implementing PCM, differential PCM and delta modulation.
PCM is based on discretization, quantization of samples and encoding of the quantization level number (see Fig. 4).

A telephone message X(t) of duration T, having a spectrum limited by the frequency fm, after filtering is converted into a sequence of narrow pulses X(l) = X(ldt), l =1,N, where N = T/dt, dt = 1/2fm, modulated by amplitude. The obtained instantaneous values X(l), l=1,N, is quantized by value using a uniform, non-uniform or adaptively variable quantization scale. The quantized values of the samples Xkv(l), l=1,N are converted by the encoder into code words characterized by the number of binary symbols that are output to the communication channel.
On the receiving side, the code words are converted by the decoder into the values of the samples Xkv(l), l=1,N, from which the message X(t) is restored using a low-pass filter.
Differential PCM and delta modulation differ from PCM in that they use nonlinear tracking of the transmitted telephone message.
Differential PCM differs from simple PCM in that it is not the telephone message samples themselves X(l), l=1,N that are quantized, but the difference between the corresponding sample X(l) and the prediction result Xpr(l), formed at the predictor output. In this case, code words containing codes of this difference and its sign (polarity) are sent to the communication channel. And, finally, delta modulation differs from simple PCM in that only sign (polarity) codes are sent to the communication channel in the form of a sequence of pulses, the time position of which allows the transmitted telephone message X(t) to be restored on the receiving side, for example, using an integrator .
It should be noted that differential PCM is the most preferable for generating digital messages. This is mainly due to the fact that the use of differential PCM allows for a reduction in the length of code words, since only information about the sign and magnitude of the increment is transmitted. In addition, the use of differential PCM allows for the elimination of slope overload, which is encountered with linear delta modulation.
Taking into account the regularities of the functioning of the peripheral organs of speech formation and transformation led to the creation of synthetic or vocoder telephony systems. In such systems, data on the deformations of the speaker's peripheral vocal apparatus are transmitted over a telephone channel. The receiving device in such systems is a model of the human vocal apparatus, the parameters of which change in accordance with the received data. In this case, the number of parameters characterizing the vocal apparatus is relatively small (10-20) and the rate of their change is commensurate with the speed of pronunciation of phonemes. In Russian speech, the number of phonemes is taken to be 42 and they represent the equivalent of different sounds that exclude each other.
The vocoder communication system functions as follows. In the transmitting part of the system, an analysis of the telephone message X(t) coming from the microphone is carried out in order to isolate the values of the parameters describing the excitation signal, as well as characterizing the resonant structure of the vocal tract. The values of the parameters in the digital code are transmitted via the communication channel. On the receiving side, the message X(t) is synthesized.using the accepted parameter values.
Thus, both when using waveform coding using PCM, differential PCM and delta modulation, and when coding parameters, sequences of symbols are output to the communication channel.
Consequently, well-known and widely used cryptographic transformations and algorithms in practice can be applied to these sequences.
Currently, the most well-known cryptographic algorithms that provide guaranteed protection of transmitted messages from unauthorized access are the American data encryption standard DES (Data Encryption Standard), which has been adopted as a US federal standard, and the Russian standard GOST-28147 — 89.
Encryption using the DES cryptographic algorithm is carried out as follows.
The original message, which is a sequence of characters, is divided into blocks of 64 characters each. Then, the following sequence of operations is performed on each block.
1. A block designated L0R0, where L0 is a block representing one of the parts of the L0R0 block, consisting of 32 characters; R0 is a block representing another part of the L0R0 block, also consisting of 32 characters, is permuted in accordance with a predetermined rule.
2. For each At the nth iteration, n = 1.16, the following sequence of operations is performed:
a) the Rn-1 block is divided into 8 blocks of 4 symbols each;
b) these blocks are transformed into 8 blocks of 6 symbols by adding the next symbols of the Rn-1 block to the left and right of the symbols of each block. For example, if a block consisted of the symbols X0X1X2X3, then as a result of adding the specified symbols to the left and right, the block will have the following form X31X0X1X2X3X4;
c) the symbols of the resulting 8 blocks are added according to mod2 with 48 symbols of the cryptographic transformation key corresponding to the n-th iteration and determined by the list of keys;
d) then the 8 blocks are fed to the inputs of the corresponding 8 substitution blocks S[ j ], j = 0.7, which transform 8 blocks of 6 symbols each into 8 blocks of 4 symbols each in accordance with a predetermined rule;
d) the 32 symbols obtained as a result of the substitution are switched in accordance with a predetermined rule;
e) then the block Sn-1 is formed by adding the symbols obtained during operation d) with the symbols of the block Ln-1 in mod2 order;
g) the symbols of the block Rn-1 are written to the place of the block Ln, and the symbols of the block Sn-1— in place of the Rn block.
3. The L16R16 block obtained after 16 iterations is subjected to a permutation that is the inverse of the permutation performed during operation 1.
The result of operation 3 is an encrypted block consisting of 64 characters.
Note that the length of the input key of the cryptographic transformation kis 56 characters. Since only 48 of the 56 characters are used at each iteration, each character of the input key is used multiple times.
The main disadvantages of the DES cryptographic algorithm, according to experts, are:
- small length of the cryptographic transformation key used;
- small number of iterations;
- complexity of practical implementation of the permutations used.
The development of the DES standard is the Russian encryption standard GOST — 28147 — 89, which was formed taking into account world experience, shortcomings and unrealized capabilities of the DES cryptographic algorithm. This standard is recommended for use to protect any data presented in the form of binary sequences.
It should be noted that the cryptographic algorithm GOST — 28147 — 89, like the cryptographic algorithm DES, is used for cryptographic transformation of messages pre-divided into blocks of 64 characters each. The algorithm is quite complex, so its concept will be mainly presented.
The GOST — 28147 — 89 algorithm provides for the following operating modes: replacement, gamma, and gamma with feedback. All these modes use the cryptographic transformation key k, consisting of 256 characters.
The replacement mode is an iterative process (the number of iterations is 32), which uses the addition operations by mod2 and mod2^32, permutations, substitutions and cyclic shifts applied to blocks of 32 characters, and combining two blocks of 32 characters each into a block of 64 characters.
In gamma mode, a cryptographic transformation of the message is performed by adding mod2 the message characters with the characters of a sequence (gamma) generated in accordance with a certain rule in blocks of 64 characters.
The feedback gamma mode differs from the gamma mode in that the symbols of the next gamma block are formed taking into account the symbols of the previous encrypted block.
The algorithm of GOST — 28147 — 89 also provides for the operation of generating an imitative insertion, which is the same for all cryptographic transformation modes. The imitative insertion is a binary sequence consisting of p symbols, which is intended to protect the message from imitation. In this case, the value of pis selected based on the condition of ensuring the required level of imitation protection.
The imitation insert is transmitted over the communication channel after the encrypted message. On the receiving side, an imitation insert is generated from the received message, which is compared with the received one. If the imitation inserts do not match, the received message is considered false.
Thus, the main difference between the cryptographic algorithm GOST — 28147 — 89 and the cryptographic algorithm DES is the length of the cryptographic transformation key used k, which ensures higher resistance of the cryptographic algorithm GOST — 28147 — 89.
Indeed, if an attacker uses total testing of cryptographic transformation keys to disclose a transmitted telephone message, and the key k from the set of cryptographic transformation keys, the power of which is equal to K, is assigned equally likely, then the probability P(T)the probability of determining the key by an attacker in time T can be estimated using the following dependence
P(T) = TW/K,
where W is the number of times the attacker tries the cryptographic transformation keys per unit of time.
Table 3. as an illustration shows the values of the probability P(T) for the DES and GOST algorithms — 28147 — 89 with W = 1E9 1/s.
Table 3. Probability valuesP(T)at W = 1E9 1/s.
| T | DES Algorithm | GOST algorithm — 28147 — 89 |
| 1 year | 0.44 | 2.72E — 61 |
| 2 years | 0.88 | 5.44E — 61 |
| 10 years | 1.0 | 2.72E — 60 |
From the analysis of the data presented in Table 3, it follows that by setting the required probability value P, it is always possible to determine such a time interval Tand a cryptographic transformation algorithm that will ensure that the specified requirement is met.
Thus, the advantages of using the above-considered algorithms for cryptographic transformation of digital telephone messages in comparison with the methods of cryptographic transformation of analog telephone messages are obvious and consist mainly in the possibility of ensuring high stability of transmitted messages. However, these advantages are achieved by using complex and expensive equipment and the rejection in most cases of a standard telephone channel.
Indeed, if PCM is used to transmit a telephone message, then to restore it on the receiving side it is necessary to receive at least 6800 instantaneous values per second. Further, if 8-bit analog-to-digital and digital-to-analog converters are used to convert instantaneous values into code, then the symbol transmission rate in the communication channel will be 54.4 kbps. Consequently, to ensure the transmission of a telephone message in this case, it is necessary to significantly increase the bandwidth of the communication channel. In addition, it is also necessary to create an encoder (decoder) that would perform cryptographic transformation of the message at a rate of 54.4 kbps.
It should be noted here that without increasing the bandwidth of the communication channel, it is possible to transmit only sequences of symbols in vocoder communication systems. However, in this case, although the speech retains acceptable intelligibility, it is often difficult to identify the subscriber by the timbre of the voice, since the voice is synthesized by a speech synthesizer and has a «metallic» tint.
Unfortunately, there are very few vocoder communication systems on the domestic market that are guaranteed to be protected from unauthorized access to transmitted telephone messages. And all of them, as a rule, are characterized by low syllabic intelligibility and difficulty in identifying the subscriber by voice timbre. An example of such a system is the Voice coder 2400 system, which uses the fairly old LPC 10 telephone message parameter encoding algorithm together with the GOST 28147 89 cryptographic algorithm.
Among the systems that stand out in a positive way, it is possible to note the domestic system SKR — 511, which is in the final stage of development, which is designed to ensure the confidentiality of telephone conversations when working on intracity and intercity communication lines. The system is located in the case of the telephone set «Panasonic KX-T2355/2365» and implements the most modern algorithm for encoding the parameters of telephone messages CELP, which ensures high speech quality. To protect against unauthorized access to transmitted messages, the cryptographic algorithm GOST — 28147 — 89 is used. The system is powered from a 220 V 50/60 Hz network or direct current with a voltage of 9 — 12 V. In this case, the consumed electrical power does not exceed 5 W.
Appendix 3
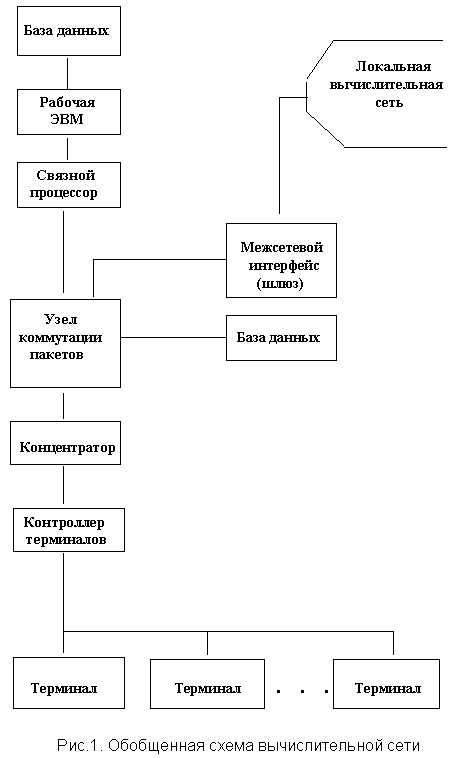
Protection of computing networks
Computer networks (CN) generally include various types of computers, data transmission networks, communication subsystems, communication devices, and internetwork interfaces (see Fig. 1). A large number of different components, resources and objects of the Armed Forces creates a very attractive environment for various types of intrusions and unauthorized actions.
The protection of the Armed Forces is carried out in the following main areas:
- protection of Armed Forces objects;
- protection of data transmission networks;
- protection of databases;
- protection of the Armed Forces control subsystem.
When protecting Armed Forces objects, a distinction is made between the protection of the objects themselves and the protection of a group of objects.
Protection of the aircraft object includes:
- identification of the object;
- confirmation of authenticity;
- granting of authority.
In practice, to identify an object, some information is used that allows for the unique identification of this object. This can be a number, a sequence of characters, or an algorithm. In this case, if an object has a certain identifier registered in the network, it is called a legal object, otherwise the object is considered illegal.
The user's work in the CS begins with the system asking for his name and identification number. In accordance with the user's answers, the CS identifies him. Note that the identification of an object is one of the functions of the security system, which is performed first when the object attempts to enter the network. If the procedure is completed successfully, the object is considered legal for this network.
The object's authenticity is then verified by asking for a password, which establishes that the supposedly legitimate object is indeed who it claims to be.
It should be noted that the use of passwords is one of the methods of authentication. In practice, authentication can also be accomplished using hardware elements at the user's disposal (keys, magnetic cards, microchips, etc.); the user's characteristic personal characteristics (fingerprints, retinal pattern, body size, voice timbre); the user's characteristic techniques and behavioral traits in real time (dynamics, keyboard style, reading speed, ability to use manipulators, etc.); habits (for example, the use of specific computer templates).
Once an object has been identified and its authenticity confirmed, its scope of activity and available resources of the CS are established. This procedure is called granting authority.
The formal description of the granting authority mechanisms is based on the concept of distinguishing between subjects that are active components of the network, such as users, processes, and objects that are passive components of the network to which network subjects can be allowed. Examples of objects may be a file, a printer, a central processor, a memory segment, or a database.
Subjects have different access rights to objects, for example, a user has the right to read a file but not write to it, to execute a program but not change it. In such cases, the user is said to have permission to read the file but not permission to write to the file. The set of all permissions granted to a subject is called the object's protection scope.
The listed procedures relate to a single object and therefore can be classified as protection tools for the object itself.
An example of a hardware and software complex for protecting information from unauthorized access is the Accord-AMDZ complex, which implements the functions of identification, user authentication, access control, and integrity of the software environment in various operating systems (MS DOS, Windows 95, Windows NT, OS/2, Unix).
Protection of a group of objects, as a rule, includes:
- mutual confirmation of authenticity;
- digital signature;
- delivery notification.
Mutual confirmation of the authenticity of objects is performed at the very beginning of a communication session during the process of establishing a connection between objects and is aimed at providing a high degree of confidence that the connection is established with an equal object. Note that within the framework of the CS, it is natural for network users to want to verify each other's authenticity.
The simplest method of mutual authentication of objects is to exchange passwords after identifying the objects. At the same time, in practice, more complex methods can be used, such as those involving the use of cryptographic systems, etc.
Once the connection is established, procedures are performed that allow:
- the recipient to gain confidence in the authenticity of the data source and the data itself;
- the sender to gain confidence in the delivery of data to the recipient and in the authenticity of the delivered data.
When solving the first problem, the means of protection is, as a rule, a digital signature (electronic signature code). A digital signature (electronic signature code) is a string of characters that depends on both the sender's identifier and the content of the message. In this case, the formation of a digital signature (electronic signature code) must be carried out by the sender of a specific message, and verification of authenticity — only by the recipient of this message. And no one, not even the sender of the message, can change the sent message so that the content of the signature (signature code) remains unchanged.
Note that if such a means of protection is used, only the recipient has confidence in the security of the message. In order to guarantee the same degree of confidence for the sender, the sender must receive a receipt of receipt, i.e. a notice of delivery. To achieve this goal, a digital signature (electronic signature code) of the confirming response message is used, which, in turn, is proof of the transmission of the original message.
Data transmission networks are one of the most vulnerable components of the Armed Forces. They contain a fairly large number of potentially dangerous places through which attackers can penetrate the Armed Forces. At the same time, attackers can use both passive and active methods.
In passive intrusion, the attacker only controls the passage of messages along communication lines, without interfering with the content of the transmitted information. In this case, he, as a rule, analyzes the transmitted information, the flow of transmitted messages, recording their destinations or only the fact of the message passing, its length and frequency of exchange, if the content of the message is unrecognizable.
To counter passive intrusions, the following are used in practice:
- protection of the message content by using various cryptographic transformations;
- prevention of the possibility of analyzing the time of sending messages and the frequency of communication sessions.
In active intrusion, the main task of the attacker is to replace the information transmitted to the CS by modifying the true messages, as well as imposing false messages. Therefore, to counteract active intrusions, protection against unauthorized or accidental modifications is used, guaranteeing the correct transmission of the message content.
Generally speaking, in practice, the functions of protecting the content of a message (ensuring confidentiality) and protecting the message from unauthorized or accidental modifications can be used both together and separately.
Protecting a message from unauthorized or accidental modifications is used in cases where the authenticity of the data plays an extremely important role. Such protection is used, for example, in the implementation of financial transactions. In practice, the following methods of ensuring the authenticity of a message are widely used:
- adding an electronic signature code or encrypted checksum to the message;
- introducing digital signatures.
However, quite often when transmitting messages it is necessary to guarantee their confidentiality. For this purpose it is necessary to use both cryptographic transformation of messages to ensure their confidentiality and an electronic signature code (digital signature). This is due to the fact that using only cryptographic transformation of messages is not always effective in protecting against their modification.
Protection of the databases of the Armed Forces means protection of the data itself and its controlled use on the network's working computers.
Protection of databases, as a rule, includes:
- protection of data content, excluding unauthorized disclosure of confidential data and information from the database;
- access control, ensuring access to data only for authorized entities in accordance with strictly defined rules and conditions;
- control of the flow of protected data during transfer from one database segment to another, during which the data is moved together with the protection mechanisms inherent in this data;
- control of consistency during use of the database, ensuring the protection and integrity of individual data elements;
- prevention of the creation of unauthorized information by using means that warn that an object receives (generates) information that exceeds the level of access rights.
Protection of the control subsystem of the aircraft system is usually understood as protection of processes circulating in the aircraft system.
Protection of the control subsystem of the aircraft includes:
- ensuring protection of network resources from the impact of unauthorized processes and unauthorized requests from authorized processes;
- ensuring the integrity of resources in the event of a violation of the schedule and synchronization of processes in the network;
- ensuring protection of network resources from unauthorized control, copying or use (software protection);
- ensuring protection during the interaction of unfriendly software systems (processes);
- implementation of software systems that do not have memory;
- protection of distributed computing.
Object identification
Traditionally, each user of the computer system receives an identification number (identifier) and a password. At the beginning of work on the terminal, the user indicates his identification number (identifier) to the system, which then asks the user for a password.
Note that if someone who does not have the authority to log in somehow learns the password and ID of a legitimate user, they will gain access to the system. User IDs are often not a secret and are known to employees of the organization. As for passwords, there is a certain risk that a user will learn another user's password and use it to their advantage.
One simple way to identify another user's password is for an attacker to use a program that replaces the standard request screen. In this case, the user, when using such a program, will give the password to the attacker's program without even knowing it.
To protect against password compromise, a so-called changing password scheme can be used. In this case, the user must use different passwords from the password list each time he logs into the system.
A more complex scheme with changing passwords is based on some one-way function y=F(x) with the following properties:
- the value of y is easily computable from the value of x;
- the value of x is difficult to computable from the known value of y.
When using this scheme, the user has some sequence of passwords
Fk-1(x), Fk-2(x), . . . , F(x), x,
where Fj(x)=F[Fj-1(x)];
k, j — are some integers.
When logging into the system for the first time, the user enters the password Fk-1(x), which is converted in the system to the value Fk(x) = F[Fk-1(x)]. After a positive comparison result, the value Fk(x)with the one stored in the system, the user is allowed into the system. The next time the user logs in, he must enter the password Fk-2(x), etc.
Note that the scheme with changing passwords has a number of disadvantages, which are as follows:
- the user must remember a long list of passwords, or keep it with him all the time, risking losing it;
- if an error occurs when transmitting a password during the login process, the user does not know whether he should use the same password or move on to the next one.
Regardless of the scheme used in practice, passwords should always be stored in a transformed form in a file accessible only to the network administrator.
Both cryptographic transformations and one-way functions can be used for this purpose.
For example, Bell Laboratories used the DES cryptographic transformation algorithm to protect its UNIX systems. In this case, the password was used as a key for the cryptographic transformation of a certain constant.
Note that passwords should never be displayed on the console or appear in printouts. If possible, printers should be turned off when entering a password.
Passwords should be transmitted in data networks in a form transformed using some cryptographic transformation.
In order to ensure guaranteed protection of the computer system, it is necessary to correctly select the password, the frequency of its replacement, and the time interval for its use.
In this regard, it should be noted that by leaving the choice of password to the users, one can often find oneself in a situation where passwords are easily guessed regardless of the time of their use.
Therefore, the choice of passwords should be made either by the person responsible for ensuring security or by the computing system itself.
For example, some operating systems, such as VAX/VMS 4.0, have special password generators.
Therefore, when a user requires a new password, the generator gives him a series of passwords of a certain length, from which the user can choose the desired one. The passwords offered to choose from should be easy to remember, but difficult for an intruder to guess.
Passwords should be changed at certain intervals in order to exclude the possibility of their guessing by an intruder. Moreover, the longer the password, the more difficult it is to guess and the more effective the system protection.
In practice, other methods of confirming the authenticity of a network object are often used.
For example, the so-called «handshake» method, methods that use individual user characteristics — personal signature, voice, fingerprints, as well as a method of confirming authenticity using identification cards.
The implementation of the «handshake» method is based on a certain function y=q(x), known only to the user and the system.
This function is used as follows. When the user needs to log in to the system, he receives some number x from it. Then the user calculates the value of the function y=q(x), which he gives to the system.
Having received the value y from the user, the system independently calculates the value of the function y by the number x and compares it with the one received from the user. In this case, the user is allowed to access the system if the result of the comparison is positive.
Obviously, this method does not require the transfer of any confidential information between the user and the computing system. This is an undoubted advantage of the «handshake» method.
However, to ensure a high level of protection, the function y=q(x) must be complex enough so that an attacker, knowing a pair of numbers (x,y), could not guess this function.
Authentication using identification cards is usually used in the business sector. The most well-known example of such cards is the credit card.
Currently, the most common are the so-called magnetic cards, which contain the user's identification number, a cryptographic transformation key and some control data used together with a password that confirms the user's authenticity.
The cryptographic transformation key is used, for example, by the system's cache memory controller for cryptographic transformation of transaction messages to be sent to the bank's computer.
The use of magnetic cards is based on the symbols embossed on the card and the information recorded on the tracks of the magnetic strip.
The existing international standard ISO 7811 defines in detail all aspects of the use of magnetic cards (embossed symbols and the content of the tracks of the magnetic strip).
The main disadvantages of such cards are the fairly frequent failure of the magnetic strip, which leads to the need to identify it only by the symbols embossed on it, and an insufficiently high level of protection against counterfeiting.
Intellectual cards, or, as they are called, smart cards, have higher protection against counterfeiting and higher reliability. Therefore, at present, a number of countries, for example, France, have almost completely abandoned magnetic cards and switched to smart cards.
A smart card is a rectangle measuring 85 by 54 mm and 0.76 mm thick. These card dimensions, like all other parameters, are defined by the international standard ISO 7816.
For example, magnetic cards, which are widely used in our country, are exactly the same size as smart cards.
However, unlike magnetic cards that store information on a magnetic strip, a smart card has a special microcircuit built into it. Smart cards can be used both for storing and processing information.
Moreover, thanks to special built-in tools, smart cards provide a qualitatively new level of protection of data recorded in memory, compared to magnetic cards.
Smart cards contain a microprocessor with a small amount of memory. In this case, the memory consists of three parts:
- read-only memory with elements of intelligence;
- random access memory;
- programmable read-only memory.
In turn, programmable read-only memory consists of two parts: unprotected and protected.
The first part contains the user identification data, and the second part contains the cryptographic transformation keys.
Currently, smart cards with their own keyboards are being developed, in which the entire authentication procedure is implemented. This procedure includes the following operations: the user tells the card his password, the card checks the authenticity and confirms to the system cache controller that the user is the true owner of the card.
In this case, neither the password nor other identification data are transmitted to the cache memory controller.
Appendix 4
Contents of the main methods of access to information taken into account when creating an information research subsystem
Initiative cooperationmanifests itself in certain actions of persons who are dissatisfied with something or who are in dire need of means of subsistence, usually those employed by a commercial enterprise, working somewhere part-time, or intending to transfer to work at another enterprise.
These persons either already possess confidential information or have the opportunity to obtain it without overcoming the physical and technical obstacles that must be overcome by persons not employed by this enterprise.
Inducement to cooperate— this is usually a violent action on the part of the attackers. Inducement to cooperate (recruitment) can be carried out by bribery, intimidation and blackmail.
Bribery in the presence of money is the most direct and very effective way to achieve goals. Bribery is a rather complex process, including economic intelligence in its purest form.
When bribery is carried out, the following sequence of operations is performed:
- finding out the capabilities of a particular official of the enterprise in facilitating the solution of the problem of obtaining some confidential information;
- establishing the financial position of this official and his family status, as well as identifying the habits, inclinations, weaknesses inherent in both himself and his family members;
- collecting the necessary compromising material on the trusted persons of this official, since they mainly act as intermediaries;
- contacting an official through trusted persons with an offer of a certain amount of money for a service rendered.
Surveying (interviewing) is an attempt to obtain certain information under the guise of naive questions.
Experience shows that such information can be most effectively and covertly obtained through the immediate circle of the heads of a commercial enterprise (secretaries, assistants, drivers, close friends, etc.).
It is also possible to obtain information through false employment.
In this case, an application is written, the documents required for employment are prepared, and during the conversations it is established what a particular department does, what professions the enterprise is interested in, what an employee of the enterprise should know and be able to do.
In order to obtain certain confidential information, false enterprises can be created that widely offer work to specialists from competing enterprises.
In order to carry out the information gathering in this case, the following sequence of operations is performed:
- identifying the circle of persons who may be the source of the information of interest;
- finding out the names of the newspapers that the identified persons receive;
- placing relevant advertisements in these newspapers, for example, such and such specialists are needed, the salary is at least 2-3 times higher than that received by the identified persons;
- questionnaire survey of visiting specialists (among whom are the persons of interest) and conducting conversations with the «management» of the enterprise, during which the persons of interest, wanting to show themselves from the best side, often reveal commercial secrets;
- after some time, informing these persons that they are not suitable for work at this enterprise.
Eavesdropping— a method of unauthorized access to confidential information based on the use of specially trained agents, informants and special eavesdropping techniques.
Eavesdropping is one of the most common ways of obtaining confidential information, since when eavesdropping, human speech is directly perceived with its features, coloring, intonation, a certain emotional load, which is often no less important than the content of the speech itself, and the eavesdropped conversations themselves are perceived in real time and, to a certain extent, can allow the intruder to make certain decisions in a timely manner.
The following eavesdropping methods can be used most effectively at present:
- eavesdropping on conversations indoors or in a car using pre-installed acoustic bugs and portable sound recording devices;
- eavesdropping on conversations indoors using laser eavesdropping systems;
- eavesdropping on telephone conversations carried out over wired communication lines using pre-installed telephone bugs;
- remote retrieval of confidential information from technical means of processing and transmitting information (usually from a personal computer) using pre-installed hardware bugs.
Secret familiarization with information and documents — this is a method of obtaining confidential information to which the subject is not allowed, but under certain conditions he can gain access to all or part of this information.
The main reason for covert familiarization with information and documents is, as a rule, a low level of discipline at the enterprise, leaving documents containing commercial secrets on work desks and in unlocked drawers, leaving information in the RAM of a personal computer after completing work, uncontrolled storage of diskettes with confidential information, etc. actions.
Covert familiarization also includes the censorship of mail of a commercial enterprise and personal correspondence.
Theft is a method of intentionally illegally taking possession of someone else's documents and information. As a rule, the theft of documents and information is determined by certain conditions that are convenient for this.
The materials provided in one of the textbooks for students of the Law Faculty of Moscow State University contain the following data, which are of interest when assessing theft as a method of unauthorized access to confidential information: 10% of people never steal, because it is incompatible with their morals; 10% of people steal at every opportunity, under any circumstances; 80% of people are usually honest, except in cases when there is a temptation to steal.
At the same time, the available materials indicate that theft can be carried out at almost any level in the hierarchy of officials of a commercial enterprise
Copying— is a method of unauthorized access to confidential information by reproducing, repeating the original. Analysis of the practice of criminal actions shows that documents, technical media, and also personal computer data containing confidential information of interest to the intruder are subject to copying.
Interception— is a method of obtaining confidential information by passively receiving signals transmitted via communication channels of various physical natures, parasitic electromagnetic radiation and interference generated by various means of processing and transmitting information.
Visual surveillance— is a method of conducting reconnaissance on the status and activities of competitors. As a result of observation, it is possible to obtain valuable information about the object of confidential interests. For example, knowing certain signs characteristic of the activities of a particular object, it is possible to detect or establish the preparation of certain organizational or industrial and commercial events.
Photography — is a method of obtaining a visible image of objects of confidential interests on photographic material. The peculiarity of the method is its documentary nature, which allows, when deciphering photographs by elements and unmasking signs, to obtain very valuable, detailed information about the object of observation.
Appendix 5
Some characteristics and features of electronic devices for eavesdropping
Depending on the type of information perceived, it is possible to divide the bugs into acoustic, telephone and hardware.
Acoustic bugs are designed for eavesdropping on acoustic (speech) information.
The information eavesdropped by acoustic bugs can be recorded using portable sound recording devices or transmitted via a radio channel, an optical channel, an alternating current power grid, connecting lines of auxiliary technical equipment (for example, a telephone line), metal structures of buildings, pipes of heating and water supply systems.
In this case, the bugs can be made in the form of a separate module, usually in the form of a parallelepiped, or camouflaged as everyday objects: an ashtray, a light bulb, a lighter, a wristwatch, a pen, a vase, etc.
If the sensitive element in an acoustic bug transmitting information via a radio channel is an electret microphone that perceives acoustic vibrations propagating via a direct acoustic (air) channel, then this bug is called a radio bug, but if the sensitive element is a contact microphone that perceives acoustic vibrations propagating via a vibroacoustic channel, then this bug is called a radio stethoscope.
In order to increase the operating time, these acoustic bugs can be equipped with systems for controlling the activation of the radio transmitter by voice (VAS or VOX systems), as well as remote control systems. Scanner receivers and software and hardware control systems are used to receive information transmitted by radio bugs and radio stethoscopes.
In addition to acoustic bugs that transmit information via a radio channel, bugs that use 220 V power lines to transmit information are widely used in practice. Such acoustic bugs are called network bugs.
To receive information transmitted by network bugs, special receivers are used that are connected to the power grid within the building (power substation). In this case, dozens of such bugs can operate simultaneously in one power grid without significantly affecting each other.
In practice, it is also possible to use acoustic bugs that transmit information via security and fire alarm systems, as well as telephone lines. The simplest device that transmits information via a telephone line is the so-called «telephone ear».
The above-mentioned features of acoustic bugs, as well as their relatively small size and weight (for example, the acoustic bug HKG-2000 from Helling has dimensions of 59( 39( 17 mm, weight 55 g and provides a range of information transmission equal to 1000 m) allow them to be placed in interiors of premises, building structures, everyday objects, radio equipment, electrical outlets and electronic devices, extension cords, technical means of communication and their connecting lines, as well as directly in power lines.
Telephone bugsare designed to eavesdrop on information transmitted over telephone lines. The eavesdropped information can be recorded using portable sound recording devices, transmitted over a radio channel or a telephone line.
Telephone bugs are made as a separate module or are camouflaged as elements of a telephone set, for example, a capacitor, telephone or microphone capsules, telephone plug or socket.
Both contact and contactless methods are used to retrieve information in such bugs. In the latter case, information is retrieved using a miniature induction sensor, which eliminates the possibility of establishing the fact of eavesdropping on information.
As a rule, the transmission of information using such a bookmark begins the moment the subscriber picks up the phone, and the transmission of information in most cases is carried out via a radio channel. Therefore, the same means are used to receive information from such telephone bugs as for conventional radio bugs.
Hardware bugs are installed in technical means of processing and transmitting information (usually in a personal computer) and are intended to ensure remote retrieval of information at the right time, disruption of its integrity and blocking.
Hardware bugs are assembled from standard modules used in computers, with minor modifications and are installed in the computer in such a way that there is access to input or output information, for example, information displayed on the PC monitor screen.
Such features of hardware bugs allow them to be placed in a personal computer when assembling a personal computer by order of the enterprise of interest, as well as when troubleshooting or modifying during service or warranty maintenance.

Добавить комментарий